Lenovo, AMI and Insyde have released patches for LogoFAIL, an image library poisoning attack.
Researchers at firmware supply chain security platform company Binarly discovered a set of security vulnerabilities that open almost all Windows and Linux computers up to attack. The security researchers named the attack LogoFAIL because of its origins in image parsing libraries. Binarly announced its discovery on Nov. 29 and held a coordinated mass disclosure at the Black Hat Security Conference in London on Dec. 6.
Any x86 or ARM-based device using the Unified Extensible Firmware Interfaces firmware ecosystem could potentially be open to the LogoFAIL attack. Binarly is still investigating whether additional manufacturers are affected. LogoFAIL is particularly dangerous because it can be remotely executed in ways many endpoint security products can’t detect.
This vulnerability is not known to have been exploited, though several vendors have released patches.
Jump to:
How does the LogoFAIL attack work?
LogoFAIL is a series of vulnerabilities whereby the graphic image parsers in system firmware can use customized versions of image parsing libraries. Essentially, an attacker can replace an image or logo (thus the name) that appears while the device boots up and gain access to the operating system and memory from there (Figure A).
Figure A
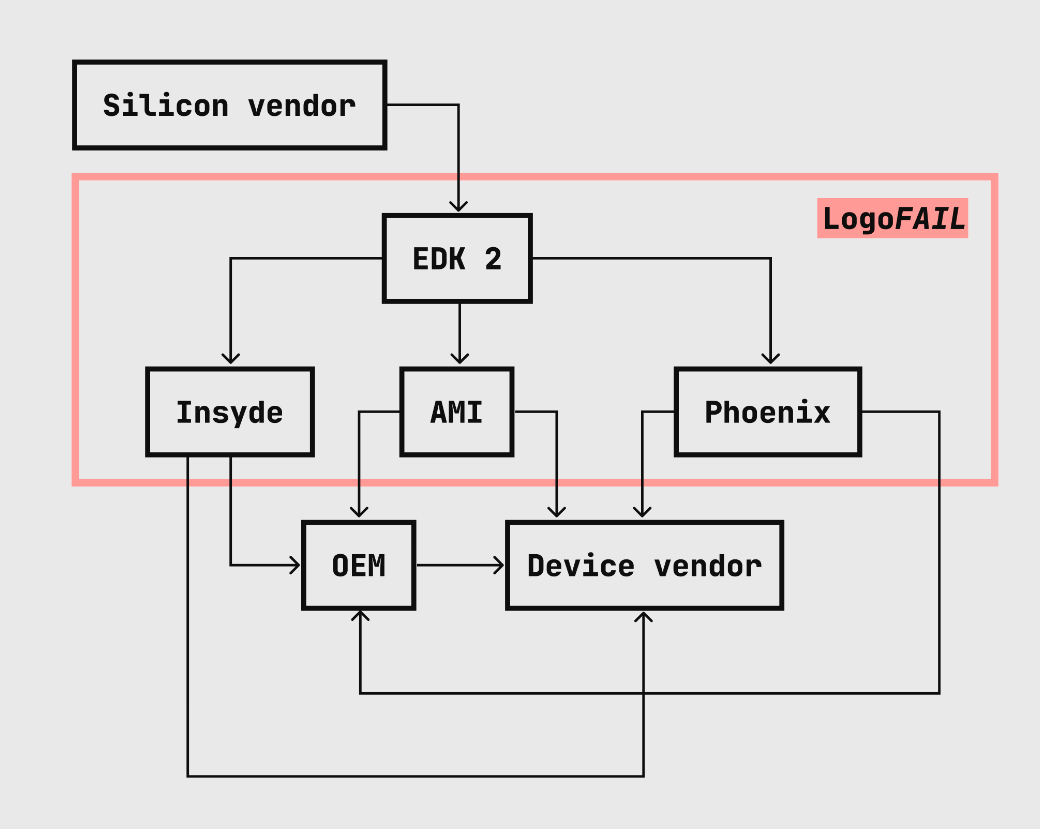
Attacks based on the UEFI system firmware have been around since the early 2000s, but “… the number of image parsers have significantly increased over the years,” Binarly wrote. More image parsers means a wider attack surface.
Put simply, attackers could embed malicious code into logos that appear during the Driver Execution Environment stage in the boot process, such as the device manufacturer’s logo. From there, attackers can access and control the device’s memory and disk (Figure B). Binarly has a technical explanation.
Figure B
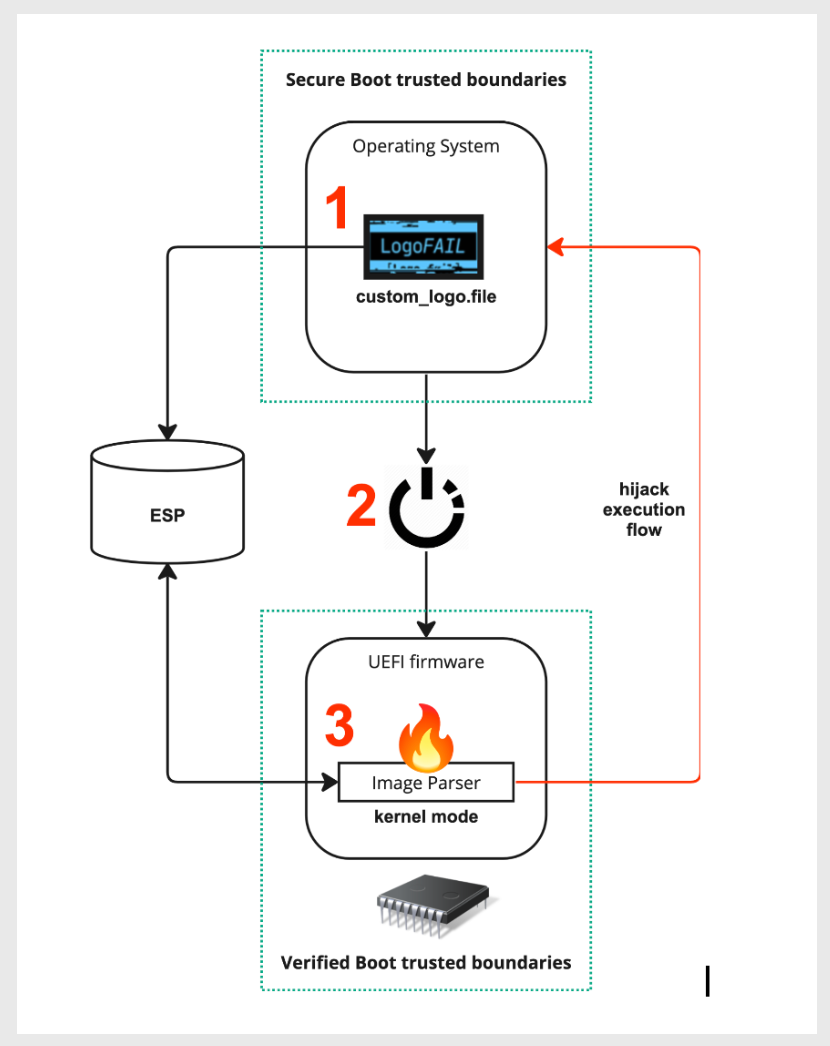
Binarly showed they could load executable code onto the hard drive before the device had fully booted up.
“We have been heavily focused on reporting vulnerabilities mainly discovered by the Binarly Transparency Platform product, but the work on LogoFAIL was different and originally initiated as a small research project just for fun,” Binarly’s team wrote. “After demonstrating a massive number of interesting attack surfaces from image-parsing firmware components, the project grew into a massive industry-wide disclosure.”
SEE: Cisco Talos analyzed cybersecurity trends of 2023 (TechRepublic)
How to defend against LogoFAIL
The following companies have released patches for LogoFAIL:
ArsTechnica recommends running UEFI defenses such as Secure Boot, Intel Boot Guard, Intel BIOS Guard or their equivalents for AMD or ARM CPUs. Tech department leaders should inform employees how to download patches as appropriate.