The number of Microsoft vulnerabilities has mostly flattened in 2023, with elevation of privilege and identity attacks being particularly common, according to BeyondTrust’s annual Microsoft Vulnerabilities report.
Identity and access management solutions company BeyondTrust studied the most significant CVEs of 2023 and Microsoft vulnerability data from Microsoft’s monthly Patch Tuesday bulletins. The report includes vulnerability trends and tips about how to reduce identity attacks.
Microsoft reported 1,228 vulnerabilities in 2023
The total number of Microsoft vulnerabilities has remained mostly steady for the past four years, with a slight (5%) dip in 2023 from 1,292 to 1,228 reported vulnerabilities.
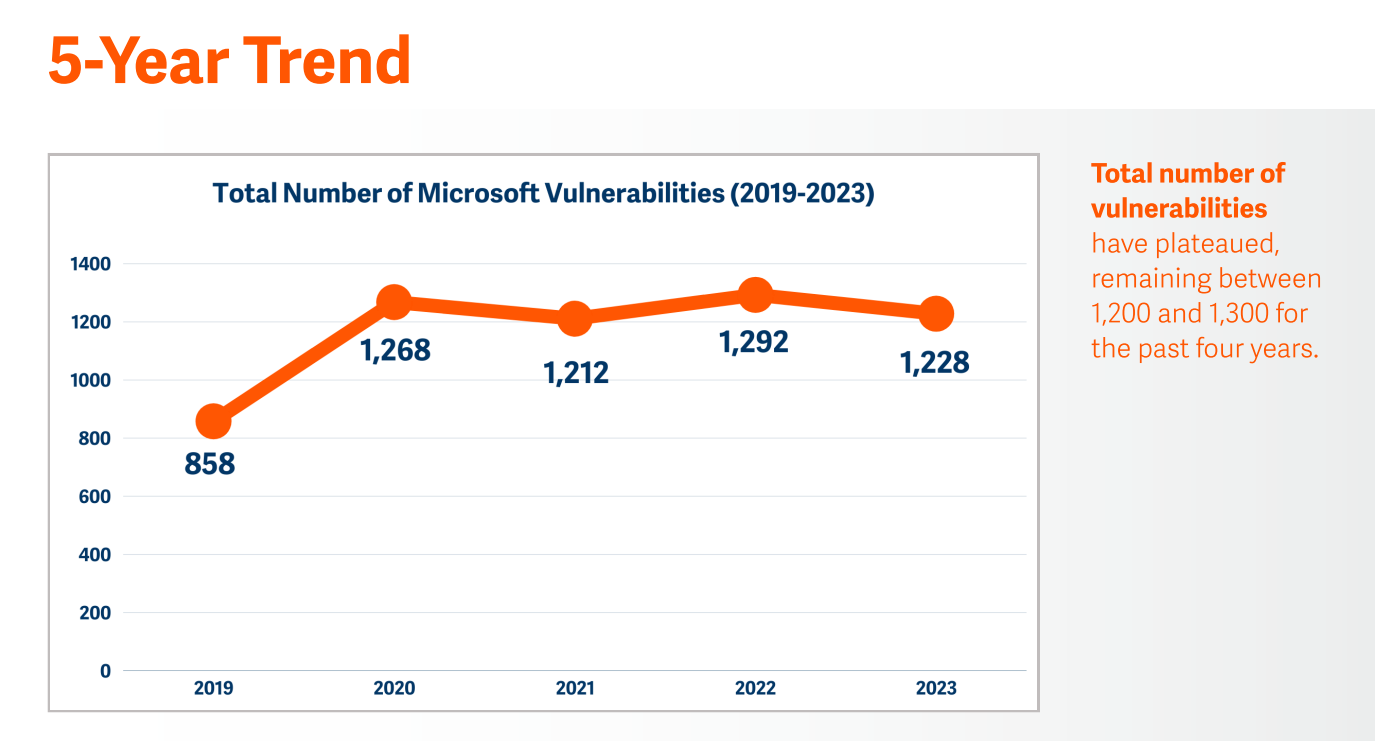
“Microsoft’s efforts to promptly patch known vulnerabilities may be offsetting the discovery of new ones by reducing the window of opportunity for attackers to exploit vulnerabilities,” David Morimanno, director of identity and access management technologies, Integral Partners, told BeyondTrust. “Also, as the MS codebase matures, new vulnerabilities might be getting introduced at a slower rate.”
The rate of critical Microsoft vulnerabilities (i.e., those with a score of 9.0 or higher on NIST’s Common Vulnerability Scoring System) has slowed. There were 84 Microsoft critical vulnerabilities in 2023, compared to 89 in 2022 and a five-year high of 196 in 2020.
How Microsoft vulnerabilities are classified
Microsoft has its own severity rating system distinct from NIST, which will produce slightly different numbers. For example, 33 Microsoft vulnerabilities from 2023 were classified as critical in NIST’s scoring system, but Microsoft itself classified 84 vulnerabilities in 2023 as critical. Microsoft’s classification system still reflects the overall trend of a slight decrease in vulnerabilities year-over-year, showing a decrease in severe vulnerabilities by 6%.
BeyondTrust noted that not all recorded Microsoft vulnerabilities pose significant risk; some are mostly theoretical or would have minimal impact even if they were exploited. However, some would be severely damaging to an organization if exploited, and these are the ones Microsoft tends to classify as critical — whether or not a threat actor has actively exploited the vulnerability.
The most common types of Microsoft vulnerabilities
The most common types of vulnerabilities in 2023 were:
- Elevation of privilege (490).
- Remote code execution (356).
- Information disclosure (124).
- Denial of service (109).
- Spoofing (90).
- Security failure bypass (56).
- Tampering (3).
Among the vulnerabilities listed as critical, most were found in the Windows Desktop and Server categories. These two categories have the same codebase, so it’s not surprising their numbers are similar.
Although elevation of privilege was the most common vulnerability, with 490 instances in 2023, that was a significant decrease from 715 instances in 2022. Azure and Windows Server in particular saw much fewer elevation of privilege vulnerabilities.
SEE: Microsoft recently opened general access to Security Copilot, the generative AI add-on to its suite of security products. (TechRepublic)
Remote code execution vulnerabilities decreased in Azure, Office and Windows but increased in Windows Server.
Details on which types of vulnerabilities cropped up in which Microsoft products and when can be found in the complete report.
Threat actors focus on identity-based infiltration techniques
“As the overall number of Microsoft vulnerabilities stabilizes and the number of critical vulnerabilities decreases, we see that attackers, much like water, will flow to the path of least resistance and focus much more of their attention on identities,” the report stated.
Microsoft suffered the Midnight Blizzard attack, a state-sponsored breach that may have impacted U.S. federal agencies because of identity-based infiltration enabled by password spraying.
“Midnight Blizzard was another case of the popular adage, ‘Attackers don’t break in – they log in,’” Jay Beale, CEO and CTO of IT consulting company InGuardians, Inc., told BeyondTrust in the report.
Identity-based infiltration is as simple as an attacker acquiring legitimate login information somehow. Identity risks can be difficult to identify ahead of time and can crop up in any of the following ways:
- The joiner, mover and leaver process.
- User permissions, rights, privileges and roles.
- Entitlements authentication, such as multi-factor authentication or single sign-on.
- Authorization for identities and accounts at rest and operating during runtime.
Defenders should start to think more holistically about privileges, identity hygiene and identity threat detection in order to detect more identity-based infiltration attacks, the report advised.
“Fostering a culture of awareness and education among all users is crucial,” Paula Januszkiewicz, CEO of CQURE, told BeyondTrust. “Unlike hacking, which is often a solitary job, cybersecurity is inherently a collaborative effort. This perspective, echoed in the report, highlights the importance of a people-centric approach to cybersecurity.”
Why Microsoft vulnerabilities are decreasing
BeyondTrust listed some possible reasons why risks to Microsoft products are gradually decreasing. Refresh cycles continue, finally phasing out long-forgotten code that could be unsupported and up to 20 years old. In particular, products made before Microsoft instituted the Security Development Lifecycle in 2004 are being fully phased out. Microsoft’s long-term security efforts may be paying off. Cloud technologies have matured and can now be secured more effectively.
BeyondTrust attributed some of the success in decreasing vulnerabilities to Microsoft’s increased collaboration with its security research community. In particular, the security research community detected many of the remote code execution vulnerabilities found in Windows Server in 2023.
Using a Chromium code base for Edge instead of a custom Microsoft codebase and removing support for Internet Explorer may have both reduced instances of critical vulnerabilities in Edge.
Microsoft has locked down many ways attackers can exploit phishing and malware payloads using Office applications. However, the addition of support for SketchUp Software’s proprietary SKP files in June 2022 allowed for some vulnerabilities to be exploited through 3D models.