The FBI acquired 7,000 LockBit decryption keys, individuals impacted should contact the authorities for aid

Affected by the LockBit ransomware? The FBI holds over 7,000 decryption keys to help you recover your data.
The FBI is urging individuals affected by the LockBit ransomware to come forward as they have obtained over 7,000 decryption keys that may enable them to retrieve their encrypted data without charge.
“Furthermore, as a result of our continuous disruption of LockBit, we now possess over 7,000 decryption keys and can assist those impacted to retrieve their data and reconnect online.” stated Bryan Vorndran, the Assistant Director at the FBI Cyber Division, during the 2024 Boston Conference on Cyber Security. “We are reaching out to known LockBit victims and encouraging anyone who suspects they were a victim to visit our Internet Crime Complaint Center at ic3.gov.”
In February, a collaborative law enforcement initiative dubbed Operation Cronos led by law enforcement agencies from 11 nations temporarily disrupted the LockBit ransomware operation.

This initiative follows a law enforcement action where they dismantled LockBit’s infrastructureOperation Cronos.”
The operation resulted in the apprehension of two members of the ransomware group in Poland and Ukraine, alongside the impoundment of numerous crypto wallets utilized by the group.
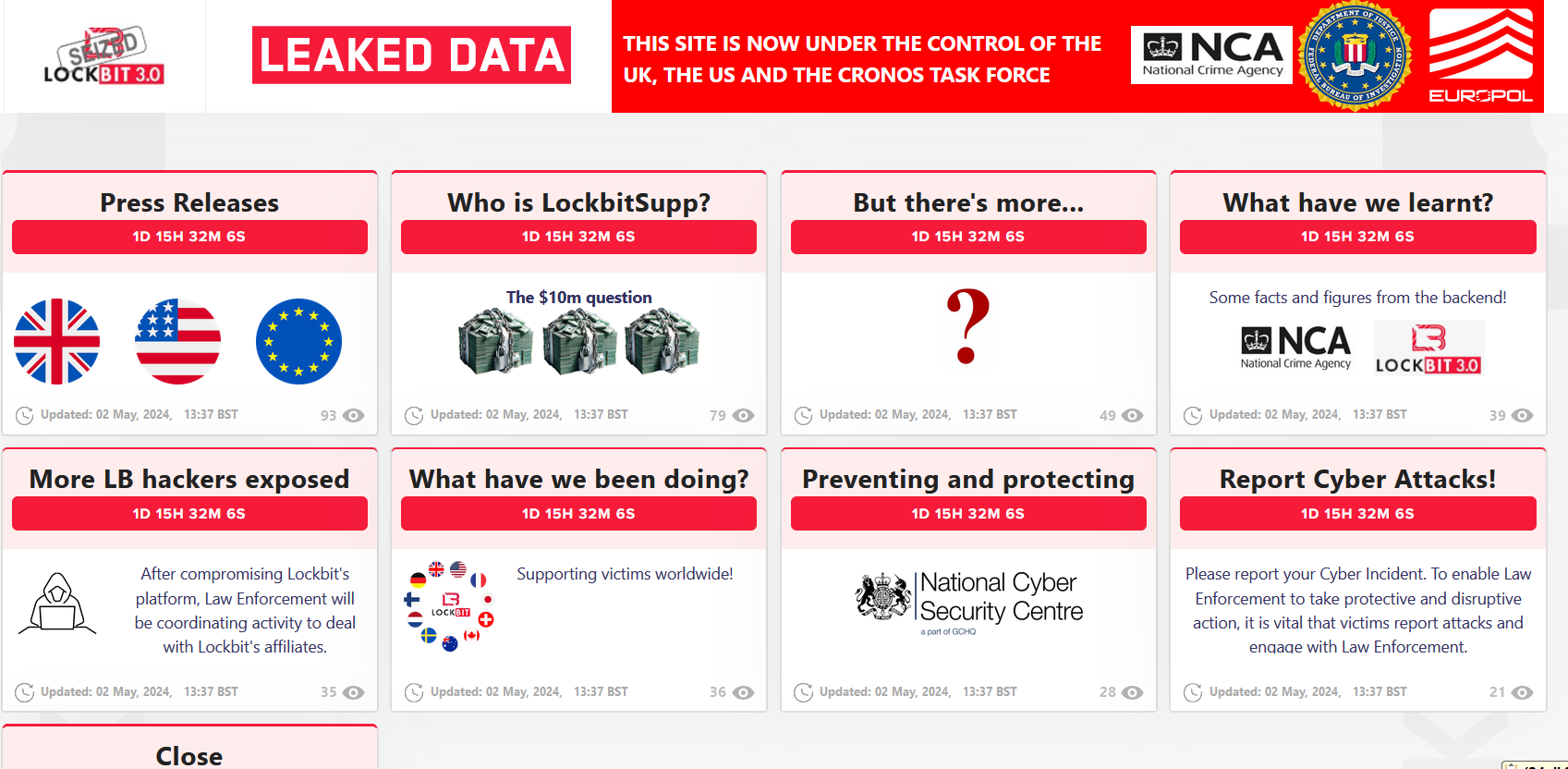
The British NCA gained control of LockBit’s central administration platform utilized by the RaaS affiliates to execute their cybercrimes. The authorities also confiscated the dark web Tor leak site employed by the group.
The NCA took over the Tor leak site and is now utilizing it to release updates on the law enforcement operation and offer assistance to the group’s victims.
Furthermore, the NCA procured the source code of the LockBit platform and an extensive amount of information concerning the group’s operations, which includes details on affiliates and supporters.
Law enforcement also accessed data pilfered from the victims of the ransomware operation, indicating that despite paying a ransom, the ransomware group frequently neglects to erase the stolen information.
“LockBit utilized a custom-made data exfiltration tool, known as Stealbit, which was utilized by affiliates to siphon off victim data. In the past 12 hours, this infrastructure, located across three nations, has been seized by members of the Op Cronos taskforce, and 28 servers belonging to LockBit affiliates have also been shut down.” reads the NCA’s announcement. “The technical infiltration and disruption is only the commencement of a series of actions against LockBit and their affiliates. In a broader operation coordinated by Europol, two LockBit actors were arrested this morning in Poland and Ukraine, over 200 cryptocurrency accounts tied to the group have been frozen.”
The NCA and its global counterparts have unlocked over 1,000 decryption keys, enabling victims of the group to restore their files without charge. The NCA reached out to victims situated in the UK providing aid to facilitate the recovery of encrypted data.
“This NCA-led investigation is a pioneering disruption of the world’s most damaging cybercrime group. It demonstrates that no criminal operation, regardless of their location, and regardless of their sophistication, is beyond the jurisdiction of the Agency and our partners.” said National Crime Agency Director General, Graeme Biggar.
“Through our close collaboration, we have outsmarted the cybercriminals; assumed control of their infrastructure, confiscated their source code, and gained keys that will enable victims to decrypt their systems.”
The free decryptor for the Lockbit ransomware can be obtained from the website of the ‘No More Ransom’ initiative. The specific version of the ransomware targeted by the decryptor remains unclear.
The FBI, UK National Crime Agency, and Europol have also revealed the identity of the administrator of the LockBit ransomware operation, known as ‘LockBitSupp’ and ‘putinkrab’ , and imposed sanctions against him. This marked the first instance where law enforcement identified the administrator of the notorious group.
The individual is a Russian citizen named Dmitry Yuryevich Khoroshev (31) from Voronezh, Russia.
“The sanctions against Russian national Dmitry Khoroshev (pictured), the administrator and developer of the LockBit ransomware group, are being announced today by the FCDO alongside the US Department of the Treasury’s Office of Foreign Assets Control (OFAC) and the Australian Department of Foreign Affairs.” reads the press release published by NCA.
The NCA declares that Khoroshev will now be subjected to a series of asset freezes and travel bans.
“Khoroshev, AKA LockBitSupp, who thrived on anonymity and offered a $10 million reward to anyone who could reveal his identity, will now be subject to a series of asset freezes and travel bans.” continues the NCA.

The UK agency reported that data obtained from the systems of the ransomware group showed that between June 2022 and February 2024, the criminals conducted more than 7,000 attacks. The primary targets were the US, UK, France, Germany, and China.
Despite the actions taken by law enforcement, the LockBit gang remains operational and has continued to attack multiple organizations since February.
LockBit, a well-known ransomware operation that appeared in September 2019, was highly active in 2022 and maintained its presence in 2023. Since January 2020, affiliates using LockBit have targeted organizations across various sectors, including financial services, agriculture, education, energy, government, healthcare, manufacturing, and transportation. The LockBit ransomware group operated through a Ransomware-as-a-Service (RaaS) model, recruiting affiliates to conduct ransomware attacks with the help of LockBit ransomware tools and infrastructure.
According to a collaborative report by US authorities and international partners, the total ransoms paid to LockBit from the US amount to approximately $91 million since LockBit’s activities were first observed in the US on January 5, 2020.
Connect with me on Twitter: @securityaffairs, Facebook: Facebook, and Mastodon
(SecurityAffairs – hacking, ransomware)








