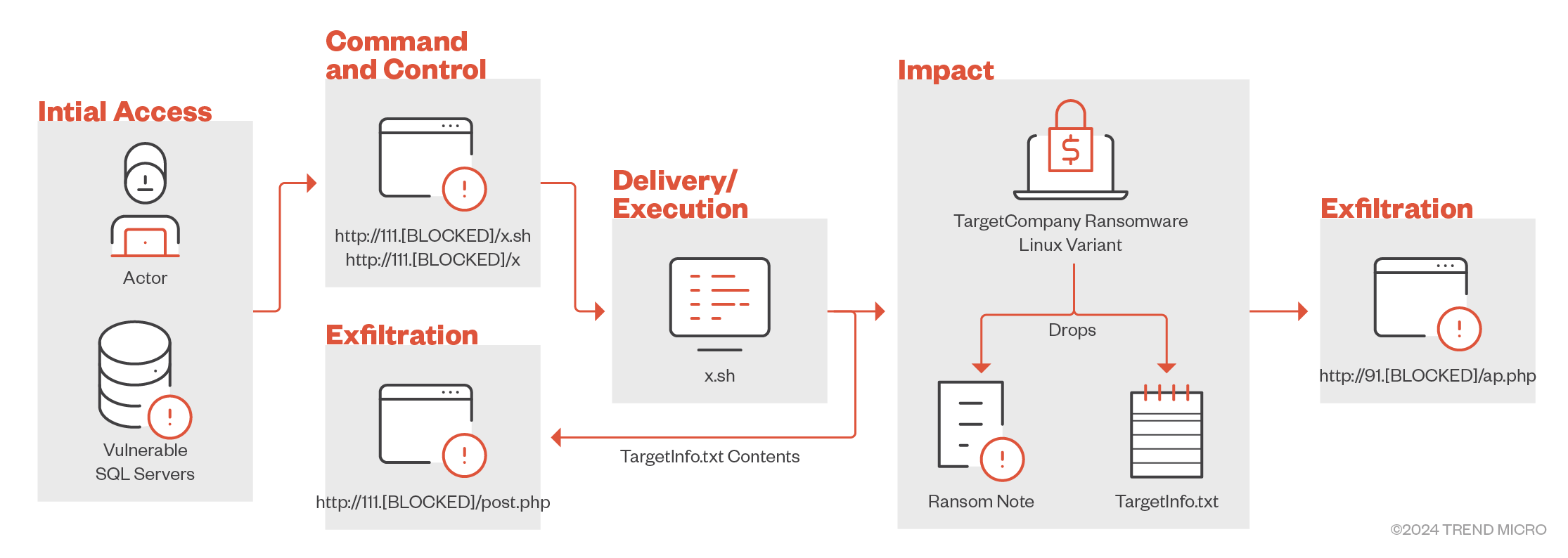

A custom shell script is the choice of payload delivery and execution for the new Linux variant of TargetCompany ransomware focused on VMware ESXi environments.
The TargetCompany ransomware family has introduced a new technique in the wild, using a custom shell script for payload delivery and execution.
This script is also used for data exfiltration with stolen data sent to two different servers, ensuring a backup for the ransomware actors.
The newly introduced Linux variant is specifically tailored to attack VMWare ESXi environments.

TargetCompany made its presence known in June 2021, identified by its unique extension add-on to encrypted filenames.
Similar to other ransomware strains, TargetCompany removes shadow copies across all drives, terminates processes that could hold valuable files, such as databases.
In February 2022, Avast, a Czech cybersecurity software firm, released a decryption tool for victims of TargetCompany ransomware, offering file recovery under certain conditions.
Expanding their scope, the threat actors behind TargetCompany are now targeting virtualization environments to widen the scale of their attacks and amplify disruption. The ransomware operators have included the ability to identify VMWare ESXi environments by running the “uname” command.
If the system name matches “vmkernel,” indicating a machine running VMware’s ESXi hypervisor, the malware proceeds to “VM mode” for encrypting files with specific extensions.
Upon execution, the ransomware deposits a victim information file named TargetInfo.txt, which is then sent to a C2 server, akin to the Windows variant.
Following encryption completion, the ransomware appends the “.locked” extension to filenames and leaves a ransom note file named “HOW TO RECOVER !!.TXT” in all folders housing encrypted files.
According to Trend Micro’s report, the IP address used for payload delivery and system information exfiltration is distinct from past TargetCompany campaigns. The IP is associated with China Mobile Communications, an ISP in China, and the certificate has a short three-month validity, hinting at a short-term purpose.
Trend Micro linked the analyzed sample to an affiliate named “vampire” through data transmitted to its C2 server. Larger ransom campaigns with hefty demands and expansive IT system targets are believed to be in progress. The affiliate may be connected to a report by Sekoia.
Malicious actors are continually evolving their tactics, as evident from TargetCompany’s new Linux variant enabling broader targeting of VMware ESXi environments.
Trend Micro has also issued the indicators of compromise for this threat.
Follow me on Twitter: @securityaffairs and Facebook and Mastodon
(SecurityAffairs – hacking, ransomware)










