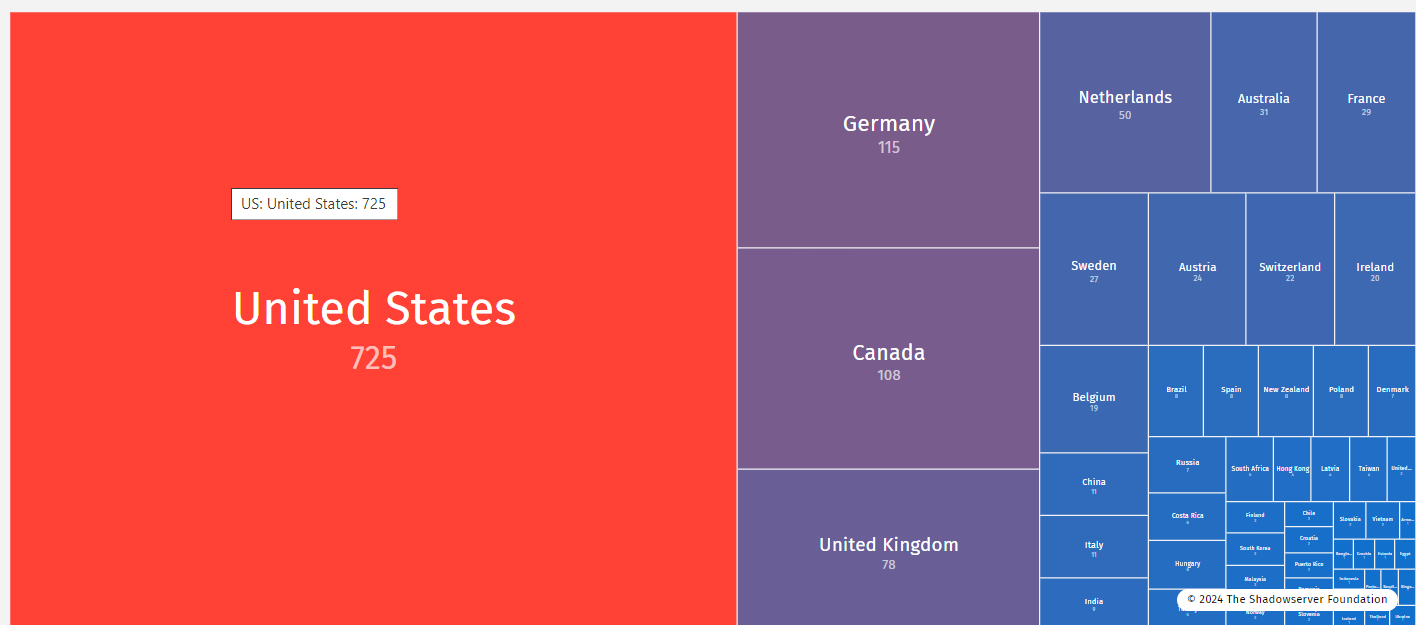
StrelaStealer targeted 100+ organizations across the EU and US
StrelaStealer targeted over 100 organizations across the EU and US

Researchers reported that over 100 organizations in Europe and US were targeted by a wave of large-scale StrelaStealer campaigns
Palo Alto Networks’ Unit42 spotted a wave of large-scale StrelaStealer campaigns impacting over 100 organizations across the EU and US.
The threat actors sent out spam emails with attachments that eventually launched the StrelaStealer malware.
The malware StrelaStealer is an email credential stealer that DCSO_CyTec first documented in November 2022. The most recent StrelaStealer variant is delivered through a zipped JScript and it employs an updated obfuscation technique in the DLL payload.
Since the discovery of StrelaStealer, threat actors launched numerous massive campaigns. WildFire researchers reported a massive campaign that occurred in November 2023 and targeted organizations in the U.S. and EU.
Unit 42 researchers observed another large-scale campaign that peaked on January 29, 2024, threat actors used a spam email localized and the subject line has the pattern of Factura/Rechnung/invoice####. The campaign targeted organizations in many sectors, including the high-tech, finance, legal services and manufacturing industries.
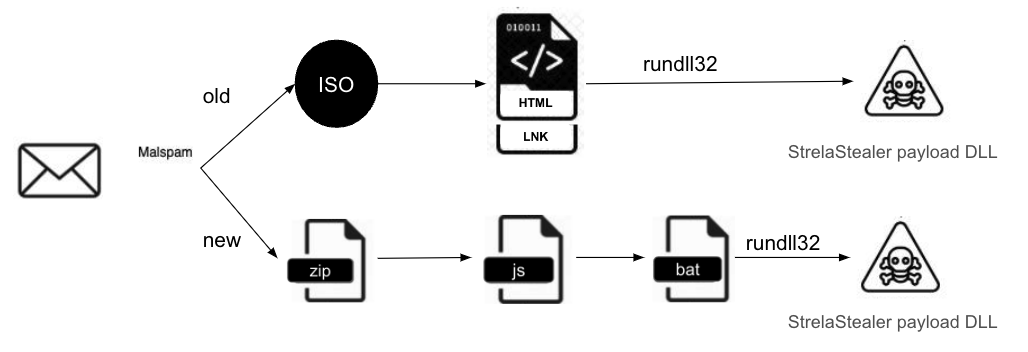
The infection chain was continuously updated, current StrelaStealer version is distributed via spear phishing emails containing a ZIP file attachment. Upon downloading and opening the archive, a JScript file is dropped onto the system.
“The JScript file then drops a Base64-encrypted file and a batch file. The Base64-encrypted file is decoded with the certutil -f decode command, resulting in the creation of a Portable Executable (PE) DLL file.” reads the report published by Palo Alto Networks. “Depending on the user’s privileges, the file drops into either %appdata%temp or c:temp on the local disk. The DLL file is then executed through the exported function hello using rundll32.exe.”

The latest StrelaStealer variant uses a packer that employs a control flow obfuscation technique to render analysis more difficult.
The authors also remove PDB strings to evade detection based on static signatures.
“StrelaStealer malware is an active email credential stealer that is always evolving. With each new wave of email campaigns, threat actors update both the email attachment, which initiates the infection chain, and the DLL payload itself. Attackers do this to evade detection by security vendors.” concludes the report.
Follow me on Twitter: @securityaffairs and Facebook and Mastodon
(SecurityAffairs – hacking, malware)