Saudi Ministry exposed sensitive data for 15 months

Saudi Ministry of Industry and Mineral Resources (MIM) had an environment file exposed, opening up sensitive details for anybody willing to take them. The Cybernews research team believes that the sensitive data was accessible for 15 months.
An environment (env.) file serves as a set of instructions for computer programs, making it a critical component for any system. Leaving these files open to anyone exposes critical data and provides threat actors with various attack options.
Meanwhile, the now-closed MIM’s env. file exposed information that attackers could employ for lateral movement within the ministry’s systems, potentially escalating to anything from account takeover to a ransomware attack.
MIM is a government body responsible for industry and mineral resources operations. It was established in 2019 to diversify Saudi Arabia’s economy away from oil and gas.
According to the team, the first time the env. file was indexed by IoT search engines was in March 2022, meaning that the data was exposed for at least 15 months. The file has since been closed and is no longer accessible to the public.
“Cybercriminals may exploit the leaked credentials to gain initial access to government systems and launch ransomware attacks. They could try to encrypt critical government data, demanding a ransom for its release or threatening to leak sensitive information publicly,” our researchers said.
We have reached out to the ministry for comment but did not receive one before publishing this article.
What MIM data was exposed?
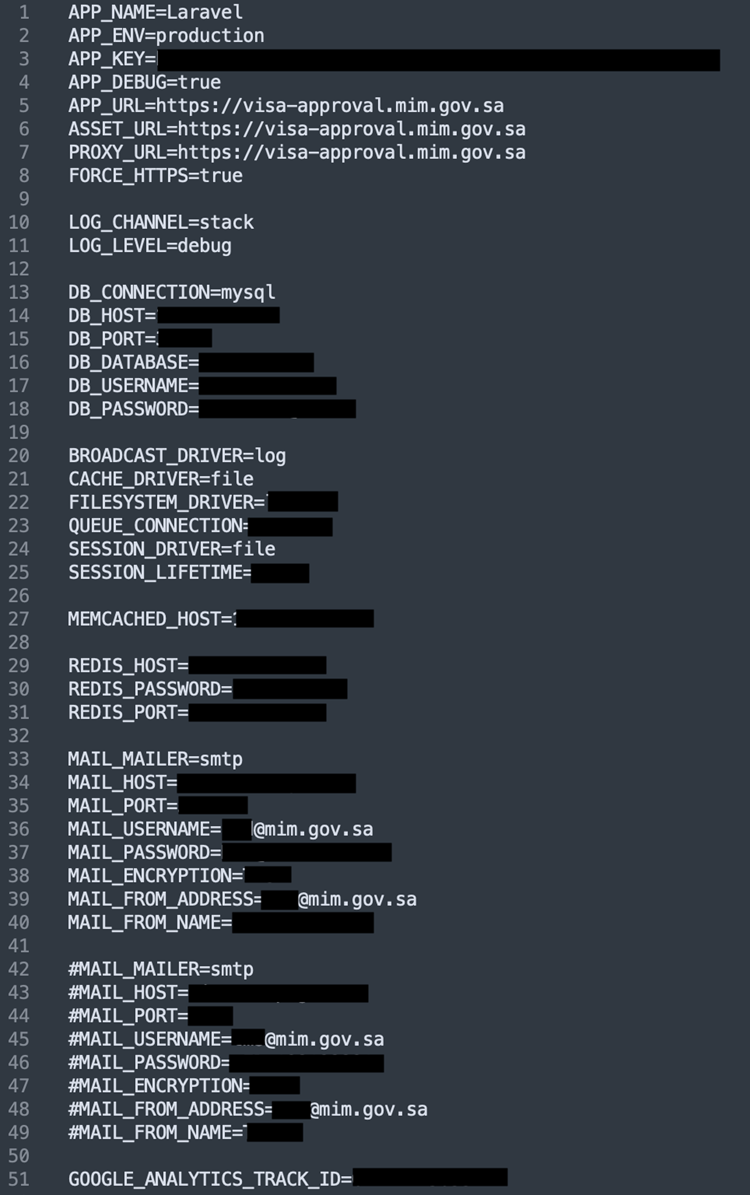
The exposed env. file leaked several types of database credentials, mail credentials, and data encryption keys. For example, the researchers discovered exposed SMTP (Simple Mail Transfer Protocol) credentials.
“With access to government SMTP credentials, attackers can impersonate government officials or employees to conduct social engineering attacks. They may attempt to deceive victims into disclosing additional sensitive information, perpetrating fraud, or gaining access to other systems or resources,” researchers said.
The now closed env. file also contained the Laravel APP_Key. The APP_Key is a configuration setting used for encryption, for example, securing session data and cookies. An exposed APP_Key would allow attackers to decrypt sensitive information, jeopardizing the data’s confidentiality.
The team also discovered credentials for MySQL and Redis databases. Organizations use MySQL databases for storing, managing, and retrieving data. Meanwhile, Redis is used for real-time analytics and messaging purposes in applications.
According to the team, both databases were available only on local networks, which means that attackers could exploit the exposed credentials if they had already established a foothold in the MIM’s systems.
Having the credentials to a government-owned database could expose sensitive government information, classified documents, personally identifiable information (PII), or other confidential records.
Risky business
The implications of leaking such information are far and wide, as attackers could perform account takeover attacks. Leaked credentials enable malicious actors to gain unauthorized access to government email accounts and database systems, which could be exploited to hijack communications, manipulate data, send malicious emails, or gain further access to other systems or resources.
According to the team, leaked database credentials pose a real risk of data breaches and exfiltration since leaked credentials grant attackers access to government-based systems.
“This can include personally identifiable information (PII) of citizens, classified information, financial records, or other sensitive government data. The stolen data can be used for identity theft, blackmail, or sold on the black market,” researchers said.
CyberNews researchers published a set of recommendations to avoid similar issues that are available in the original post at:
https://cybernews.com/security/saudi-ministry-mim-exposed-sensitive-data/
About the author: Vilius Petkauskas, Deputy Editor @CyberNews
Follow me on Twitter: @securityaffairs and Facebook and Mastodon
(SecurityAffairs – hacking, Saudi Ministry)








 " title="
" title="
