Raging Blizzard Increases Deceptive Spear-Phishing Assaults Against More Than 100 Organizations

A recent assault has been unveiled by the Microsoft Threat Intelligence team, revealing a new offensive by the Russian threat entity, Midnight Blizzard. This operation is aimed at numerous users associated with over 100 institutions. The attack employs targeted spear-phishing emails containing RDP configuration files, which allow the infiltrators to establish connections to and potentially compromise the specified systems.
The onslaught has affected a vast number of individuals within the realms of higher education, defense, non-governmental bodies, and governmental agencies. Multiple countries have suffered the repercussions, notably the U.K., Europe, Australia, and Japan, aligning with past spear-phishing campaigns conducted by Midnight Blizzard.
Inclusion of RDP Configuration File in Phishing Emails
The most recent attack campaign by Midnight Blizzard involved sending meticulously crafted emails to recipients, utilizing social engineering tactics that focused on topics related to Microsoft, Amazon Web Services, and the principle of Zero Trust.
Notably, emails were dispatched from legitimate organizations’ email addresses that had been acquired by the threat actor through prior compromises. All emails came with an RDP configuration file, endorsed with a complimentary LetsEncrypt certificate, containing numerous critical settings.
Upon launching the file, an RDP link was established to a system under the control of the attacker. This connection enabled the malefactor to extract data concerning the targeted system, including files, network drives, peripherals like printers, microphones, and smart cards.
Furthermore, this connection facilitated the pilfering of clipboard data, web verification utilizing Windows Hello, passkeys, security keys, and even Point-of-Sale devices. Through such access, the attacker could potentially implant malware on the targeted system or on any network share(s) that were mapped.
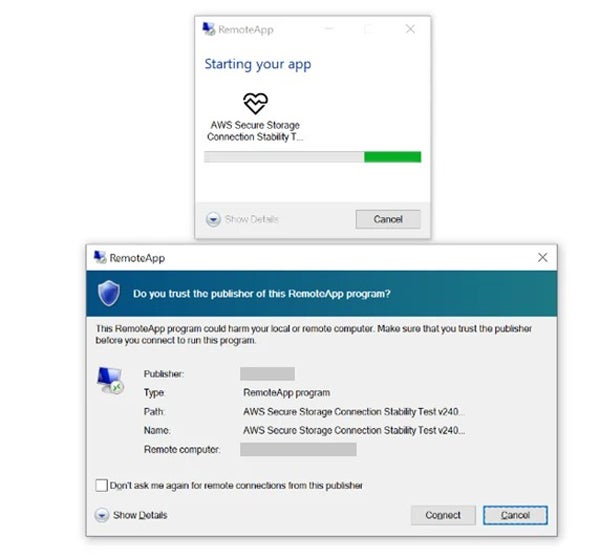
The outbound RDP connections were initiated towards domains engineered to deceive targets into believing they were AWS domains. In collaboration with the Ukrainian CERT-UA to combat this menace, Amazon promptly began the process of confiscating the affected domains to disrupt the operation. Conversely, Microsoft directly informed affected customers who were under threat or had already been compromised.
Diverse Sectors Targeted by Midnight Blizzard in Recent Times
As indicated in a collaborative cybersecurity advisory, Midnight Blizzard, along with the APT29, Cozy Bear, and the Dukes threat groups, are linked to the Russian Federation Foreign Intelligence Service.
Since at least the year 2021, Midnight Blizzard has been consistently attacking entities in the Defense, Technology, and Finance sectors from the U.S., Europe, and globally, with espionage objectives and to facilitate further cyber actions, including supporting Russia’s active invasion of Ukraine.
EXPLORE: Strategies for Developing an Effective Cybersecurity Awareness Initiative (TechRepublic Premium)
In January 2024, the cohort targeted Microsoft and Hewlett Packard Enterprise, successfully gaining entry into the email inboxes of multiple personnel. In response to this incident, Microsoft publicly acknowledged that the attackers set out by initially pursuing email accounts for information regarding Midnight Blizzard itself.
Later, in March 2024, the threat actor is said to have adjusted its strategies to focus more on cloud infrastructures.
Microsoft noted that Midnight Blizzard is among the most covert perpetrators of cyberattacks. According to a separate Microsoft report, the group previously deactivated the organization’s Endpoint Detection and Response mechanisms following a system reboot. Subsequently, they patiently waited for a month for the systems to reboot and exploited susceptible machines that were yet to be patched.
Furthermore, the threat entity showcases technical finesse, having been observed deploying MagicWeb, a malicious DLL planted on Active Directory Federated Services servers to maintain persistence and extract data. This tool also enables Midnight Blizzard to create tokens that circumvent AD FS policies and log in as any user.
Safeguarding Against Midnight Blizzard
To shield against this threat, the following measures should be taken:
- Disable or control outbound RDP connections to external or public networks
- Prohibit RDP files from email clients or webmail services
- Prevent users from executing RDP files
- Enable multi-factor authentication wherever feasible
- Implement phishing-resistant authentication mechanisms, such as utilizing FIDO tokens. Refrain from using SMS-based MFA, as it may be vulnerable to SIM-jacking attacks
- Enforce Conditional Access Authentication Strength to mandate the use of phishing-resistant authentication methods
Furthermore, deploying Endpoint Detection and Response (EDR) solutions is essential for identifying and blocking suspicious activities. Organizations should also consider incorporating antiphishing tools and antivirus software to detect and counteract the threat effectively.
Disclaimer: I am employed by Trend Micro; however, the opinions expressed in this piece are solely my own.




