DinodasRAT Linux variant targets users worldwide

A Linux variant of the DinodasRAT backdoor used in attacks against users in China, Taiwan, Turkey, and Uzbekistan, researchers from Kaspersky warn.
Researchers from Kaspersky uncovered a Linux version of a multi-platform backdoor DinodasRAT that was employed in attacks targeting China, Taiwan, Turkey, and Uzbekistan.
DinodasRAT (aka XDealer) is written in C++ and supports a broad range of capabilities to spy on users and steal sensitive data from a target’s system. ESET researchers reported that a Windows version of DinodasRAT was used in attacks against government entities in Guyana.
ESET first discovered a new Linux version of DinodasRAT in October 2023, but experts believe it has been active since 2022.
In March 2024, Trend Micro researchers uncovered a sophisticated campaign conducted by a threat actor tracked as Earth Krahang while investigating the activity of China-linked APT Earth Lusca.
The campaign seems active since at least early 2022 and focuses primarily on government organizations.
Since 2023, the Earth Krahang shifted to another backdoor (named XDealer by TeamT5 and DinodasRAT by ESET). Compared to RESHELL, XDealer provides more comprehensive backdoor capabilities. In addition, we found that the threat actor employed both Windows and Linux versions of XDealer to target different systems.
The DinodasRAT Linux implant was mainly employed in attacks against Red Hat-based distributions and Ubuntu Linux. Once executed, the malware creates a hidden file in the same directory as the executable, following the format “.[executable_name].mu”.
The malware establishes persistence on the host by using SystemV or SystemD startup scripts. The backdoor gathers information about the infected machine and sends it to the C2 server.
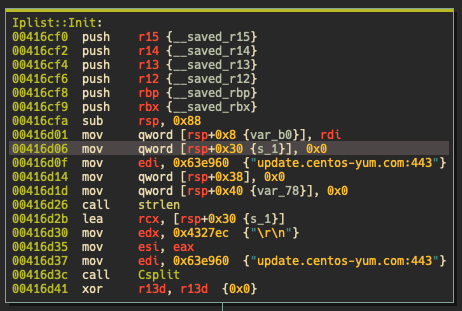
Both Linux and Windows versions of DinodasRAT communicates with the C2 over TCP or UDP. The C2 domain is hard-coded into the binary.
The researchers noticed that unlike other RAT, the attackers do not collect any user-specific data to generate this UID. The UID typically includes the date of infection, MD5 hash of the dmidecode command output (a detailed report of the infected system’s hardware), randomly generated number as ID, and backdoor version.
Below is the list of commands supported by the backdoor:
| ID | Function | Command |
| 0x02 | DirClass | List the directory content. |
| 0x03 | DelDir | Delete directory. |
| 0x05 | UpLoadFile | Upload a file to the C2. |
| 0x06 | StopDownLoadFile | Stop file upload. |
| 0x08 | DownLoadFile | Download remote file to system. |
| 0x09 | StopDownFile | Stop file download. |
| 0x0E | DealChgIp | Change C2 remote address. |
| 0x0F | CheckUserLogin | Check logged-in users. |
| 0x11 | EnumProcess | Enumerate running processes. |
| 0x12 | StopProcess | Kill a running process. |
| 0x13 | EnumService | Use chkconfig and enumerate all available services. |
| 0x14 | ControlService | Control an available service. If 1 is passed as an argument, it will start a service, 0 will stop it, while 2 will stop and delete the service. |
| 0x18 | DealExShell | Execute shell command and send its output to C2. |
| 0x19 | ExecuteFile | Execute a specified file path in a separate thread. |
| 0x1A | DealProxy | Proxy C2 communication through a remote proxy. |
| 0x1B | StartShell | Drop a shell for the threat actor to interact with. |
| 0x1C | ReRestartShell | Restart the previously mentioned shell. |
| 0x1D | StopShell | Stop the execution of the current shell. |
| 0x1E | WriteShell | Write commands into the current shell or create one if necessary. |
| 0x27 | DealFile | Download and set up a new version of the implant. |
| 0x28 | DealLocalProxy | Send “ok”. |
| 0x2B | ConnectCtl | Control connection type. |
| 0x2C | ProxyCtl | Control proxy type. |
| 0x2D | Trans_mode | Set or get file transfer mode (TCP/UDP). |
| 0x2E | Uninstall | Uninstall the implant and delete any artifacts from the system. |
The Linux version of DinodasRAT uses Pidgin’s libqq qq_crypt library functions for encryption and decryption of data. The library uses the Tiny Encryption Algorithm (TEA) in CBC mode to cipher and decipher the data.
“They do not collect user information to manage infections. Instead, hardware-specific information is collected and used to generate a UID, demonstrating that DinodasRAT’s primary use case is to gain and maintain access via Linux servers rather than reconnaissance.” concludes the report. “The backdoor is fully functional, granting the operator complete control over the infected machine, enabling data exfiltration and espionage.”
Follow me on Twitter: @securityaffairs and Facebook and Mastodon
(SecurityAffairs – hacking, Linux)