
Phishing, misconfigurations and missing patches are top concerns among security leaders, but they also say their organizations are letting observability tools gather rust.

Content delivery, security and cloud services company Akamai, in partnership with U.S. cybersecurity training company SANS Institute, released on Tuesday the results of a new study examining the most worrisome security risks related to APIs. The 2023 SANS Survey on API Security found that the top risk is phishing attacks.
In addition, the 2023 global survey, which polled 231 application security professionals, found that fewer than 50% of respondents have API security testing tools in place and only 29% have API discovery tools. It also found that only 29% of respondents use the API security controls that are already included in DDoS and load balancing services.
Jump to:
Top six API security risks
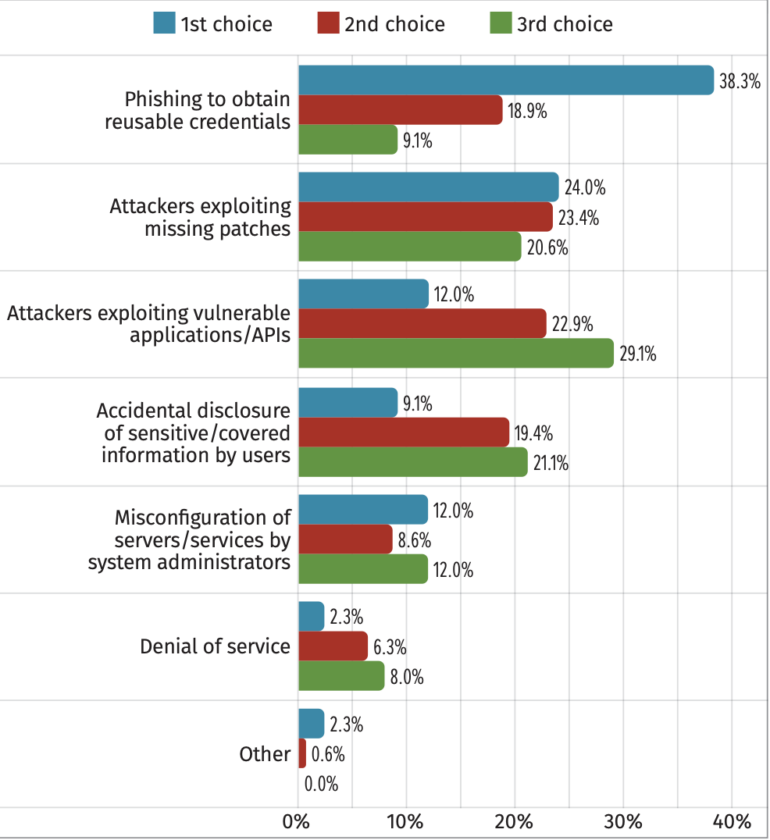
When asked what they perceived as the top API security risk, respondents most often said:
- Phishing to obtain reusable credentials (38.3%).
- Attackers exploiting missing patches (24%).
- Attackers exploiting vulnerable applications/APIs (12%).
- Misconfiguration of servers/services by system administrators (12%)
- Accidental disclosure of sensitive/covered information by users (9.1%).
- Denial of service (2.3%) (Figure A).
Figure A
API proliferation makes security challenges more complex
Akamai reported earlier this year that 2022 broke records for application and application programming interface attacks. Part of the problem is the sheer number of APIs in use by organizations, which is an issue that fits nicely into the “you don’t know what you don’t know” risk bucket.
John Pescatore, director of emerging security trends at SANS and author of the 2023 study, pointed out that the proliferation of APIs is emblematic of how complexity is the enemy of security. He also explained how the very nature of distributed applications increases the threat surface for attackers and the likelihood of vulnerabilities being part of production code.
In the new study, Akamai cites a report by 451 Research that states the average enterprise has more than 15,000 APIs in use. To give a sense of the volume of attacks, Akamai earlier this year reported that on one day, Oct. 8, 2022, there were 161 million API attacks worldwide.
SEE: The C-suite considers API security a top concern (TechRepublic)
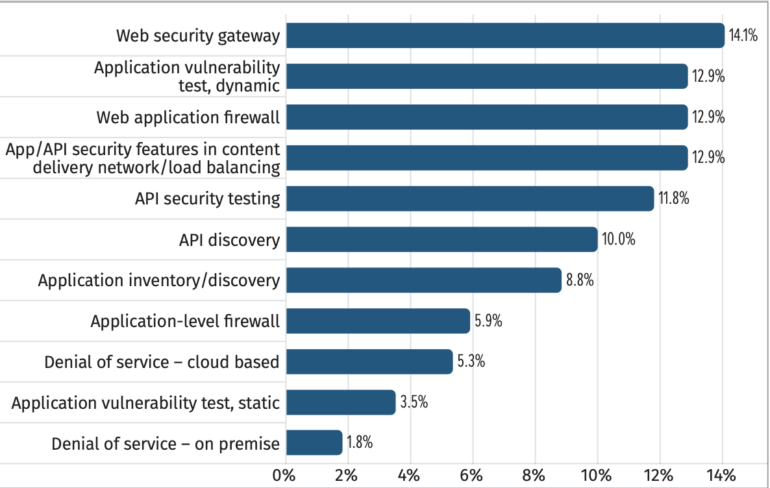
According to the report, the survey’s respondents said they planned to close API security gaps in the future with:
- Web security gateways (14%).
- API security features in content delivery network/load balancing (13%).
- Web application firewalls (13%).
- Dynamic application security testing (13%) (Figure B).
Figure B
Zero-day risks getting too much credence, misconfiguration not enough
The Akamai study suggests that respondents are giving too little weight to the risk of misconfigured applications and too much to zero-day risks, according to Rupesh Chokshi, general manager of application security at Akamai.
“An organization’s API security plan should include building secure APIs and configuring applications correctly. At the same time, organizations should understand zero-day risks, such as how APIs become vulnerable and at risk of exploitation. The distinction is important because it shows that robust API security needs to give significant weight to every aspect of the API lifecycle; otherwise, vulnerabilities will be missed,” said Chokshi.
Closing the door to application layer misconfigurations
Ory Segal, chief technology officer of Palo Alto Networks Prisma Cloud, concurred that misconfiguration in modern, cloud-native applications poses a substantial risk that is frequently underplayed by organizations.
“Unfortunately, many focus their attention towards zero-day risks and known vulnerabilities in open source software packages (i.e., common vulnerabilities and exposures). However, statistics and reality show that attackers are more likely to exploit application layer misconfigurations, exposing organizations to significant risk and potential data breaches — just look at the number of recent breaches involving publicly open cloud storage buckets.”
Among Segal’s recommendations:
- For expediting configuration management, infrastructure as code scanning can provide consistency in configuration and reduce human error.
- Improving API observability is essential. This can be achieved by implementing robust logging and monitoring.
- Detailed logs, including API calls, response times and error messages, can offer invaluable insights into the performance and security of APIs.
- Automated anomaly detection can assist in identifying unusual activities indicative of a potential attack.
- For more comprehensive API security, adopting the principle of least privilege is recommended, allowing each user only the minimum levels of access necessary to perform their tasks.
- Regular audits and automated testing for common security issues, such as injection-based attacks, can help ensure the ongoing security of APIs.
Proper API hygiene: Inventories, patches, threat assessment
Pescatore wrote that an organization’s API security plan should encompass:
- Inventory of APIs in use and processes that use those APIs.
- Vulnerability assessment of APIs in use.
- Threat assessment of active attacks exploiting those vulnerabilities.
- Risk-based mitigation of critical API vulnerabilities.
Sixty-two percent of respondents to the survey said they use web application firewalls as part of API risk mitigation, and 79% of survey takers reported training development staff on application security. Also, 57% of respondents reported API inventory accuracy of between 25% and 75%.
SEE: Gigamon report shines light on deep observability (TechRepublic)
“Security hygiene controls like strong authentication, asset inventory, vulnerability management and change control need to address API security issues,” Pescatore wrote. “Prevention and detection need to be upgraded to deal with API-centric attacks, and infrastructure services (such as content delivery networks and denial of service filtering) need to be put to work as well.”









