Russian Cybercriminals Aim at Europe with HeadLace Malware and User Data Harvesting
A Russian cybercriminal group known as APT28 has been identified as the instigator of a series of attacks aimed at networks across Europe using the HeadLace malware and deceptive web pages to collect user credentials.
Also recognized by various aliases such as BlueDelta, Fancy Bear, Forest Blizzard, FROZENLAKE, Iron Twilight, ITG05, Pawn Storm, Sednit, Sofacy, and TA422, APT28 is an advanced persistent threat (APT) organization associated with the GRU, Russia’s military intelligence unit.
The hacking team works discreetly and with sophistication, showcasing their ability to adapt through thorough preparedness and specialized tools, leveraging legitimate internet services (LIS) and living off-the-land binaries (LOLBins) to camouflage their activities within standard network traffic.
“Between April and December 2023, BlueDelta deployed Headlace malware in multiple stages using geofencing strategies to target European networks, particularly focusing on Ukraine,” according to Recorded Future’s Insikt Group reports.
“BlueDelta’s espionage campaigns form part of a larger scheme aimed at gathering intelligence on entities deemed militarily significant to Russia amidst the ongoing conflict with Ukraine.”
HeadLace, as previously reported by the Computer Emergency Response Team of Ukraine (CERT-UA), Zscaler, Proofpoint, and IBM X-Force, is disseminated through spear-phishing emails containing malicious links that trigger a multi-step infection process to install the malware.
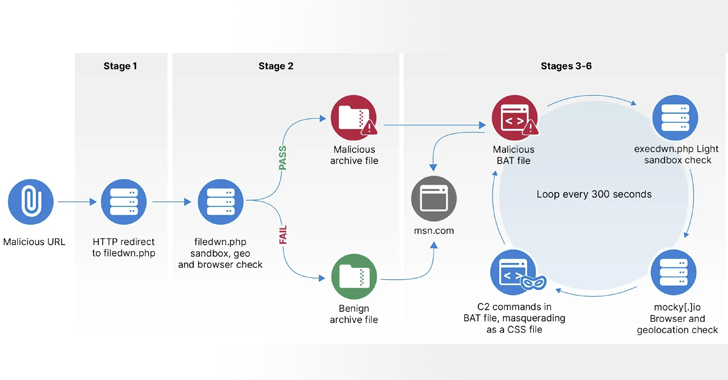
During the initial phase, BlueDelta utilized a seven-stage infrastructure to distribute a malicious Windows BAT script (HeadLace) capable of downloading and executing subsequent shell commands, contingent on sandbox and geofencing validations.
The second phase, which began on September 28, 2023, saw the use of GitHub as the starting point for an infrastructure redirection, with the third phase transitioning to PHP scripts hosted on InfinityFree starting October 17, 2023.
“The final activity detected in phase three dated back to December 2023,” the company disclosed. “Subsequently, BlueDelta likely discontinued the use of InfinityFree hosting in favor of hosting infrastructure on webhook[.]site and mocky[.]io directly.”
BlueDelta has also engaged in user data harvesting operations aimed at platforms like Yahoo! and UKR[.]net, by serving counterfeit pages to deceive victims into entering their login details.
Another tactic involved developing dedicated web pages on Mocky that communicate with a Python script operating on compromised Ubiquiti routers to extract the entered credentials. Earlier in February, a joint law enforcement operation led by the U.S. disrupted a botnet comprising Ubiquiti EdgeRouters that APT28 utilized for this purpose.
The targets of the user data harvesting campaign encompassed the Ukrainian Ministry of Defense, Ukrainian arms dealers, European railway networks, and a think tank in Azerbaijan.
“Successfully breaching the networks of Ukraine’s Ministry of Defense and European railway systems could provide BlueDelta with intelligence that might influence battle strategies and overall military tactics,” Recorded Future remarked.
“Moreover, BlueDelta’s interest in the Azerbaijan Center for Economic and Social Development indicates a desire to comprehend and potentially steer regional policies.”
This development coincides with observations of another state-backed Russian threat group named Turla that has been reported utilizing human rights seminar invites as phishing bait to distribute a payload similar to the TinyTurla backdoor via the Microsoft Build Engine (MSBuild).











