A
new
variant
of
the
Android
banking
trojan
named
Xenomorph
has
surfaced
in
the
wild,
the
latest
findings
from
ThreatFabric
reveal.
Named
“Xenomorph
3rd
generation”
by
the
Hadoken
Security
Group,
the
threat
actor
behind
the
operation,
the
updated
version
comes
with
new
features
that
allow
it
to
perform
financial
fraud
in
a
seamless
manner.
“This
new
version
of
the
malware
adds
many
new
capabilities
to
an
already
feature-rich
Android
banker,
most
notably
the
introduction
of
a
very
extensive
runtime
engine
powered
by
Accessibility
services,
which
is
used
by
actors
to
implement
a
complete
ATS
framework,”
the
Dutch
security
firm
said
in
a
report
shared
with
The
Hacker
News.
Xenomorph
first
came
to
light
a
year
ago
in
February
2022,
when
it
was
found
to
target
56
European
banks
through
dropper
apps
published
on
the
Google
Play
Store.
In
contrast,
the
latest
iteration
of
the
banker
–
which
has
a
dedicated
website
advertising
its
features
–
is
designed
to
target
more
than
400
banking
and
financial
institutions,
including
several
cryptocurrency
wallets.
ThreatFabric
said
it
detected
samples
distributed
via
Discord’s
Content
Delivery
Network
(CDN),
a
technique
that
has
witnessed
a
surge
since
2020.
Two
of
the
Xenomorph-laced
apps
are
listed
below
–
-
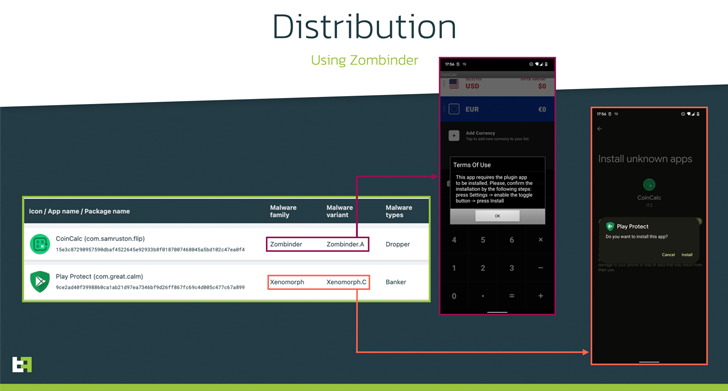
Play
Protect
(com.great.calm) -
Play
Protect
(meritoriousness.mollah.presser)
“Xenomorph
v3
is
deployed
by
a
Zombinder
app
‘bound’
to
a
legitimate
currency
converter,
which
downloads
as
an
‘update’
an
application
posing
as
Google
Protect,”
ThreatFabric
explained.
Zombinder
refers
to
an
APK
binding
service
advertised
on
the
dark
web
since
March
2022,
wherein
the
malware
is
delivered
via
trojanized
versions
of
legitimate
apps.
The
offering
has
since
been
shut
down.
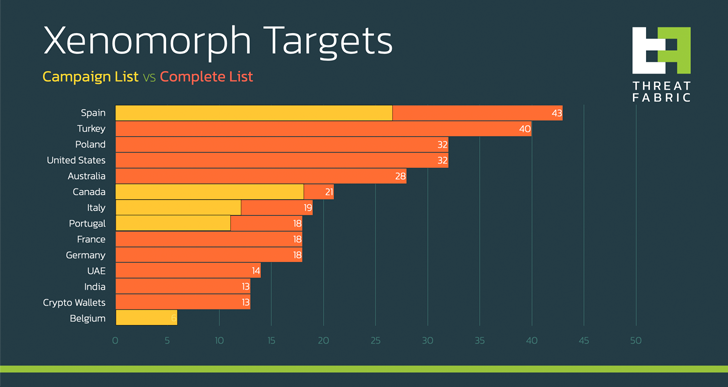
Targets
of
the
latest
campaign
go
beyond
its
European
focus
(i.e.,
Spain,
Italy,
and
Portugal)
to
include
Belgian
and
Canadian
financial
entities.
WEBINAR
Discover
the
Hidden
Dangers
of
Third-Party
SaaS
Apps
Are
you
aware
of
the
risks
associated
with
third-party
app
access
to
your
company’s
SaaS
apps?
Join
our
webinar
to
learn
about
the
types
of
permissions
being
granted
and
how
to
minimize
risk.
Xenomorph,
like
banking
malware,
is
known
to
abuse
Accessibility
Services
to
perform
fraud
through
overlay
attacks.
It
also
packs
in
capabilities
to
automatically
complete
fraudulent
transactions
on
infected
devices,
a
technique
called
Automated
Transfer
System
(ATS).
With
banks
moving
away
from
SMS
for
two-factor
authentication
(2FA)
to
authenticator
apps,
the
Xenomorph
trojan
incorporates
an
ATS
module
that
allows
it
to
launch
the
app
and
extract
the
authenticator
codes.
The
Android
malware
further
boasts
of
cookie-stealing
functions,
enabling
the
threat
actors
to
perform
account
takeover
attacks.
“With
these
new
features,
Xenomorph
is
now
able
to
completely
automate
the
whole
fraud
chain,
from
infection
to
funds
exfiltration,
making
it
one
of
the
most
advanced
and
dangerous
Android
Malware
trojans
in
circulation,”
the
company
said.