A
North
Korean
espionage
group
tracked
as
UNC2970
has
been
observed
employing
previously
undocumented
malware
families
as
part
of
a
spear-phishing
campaign
targeting
U.S.
and
European
media
and
technology
organizations
since
June
2022.
Google-owned
Mandiant
said
the
threat
cluster
shares
“multiple
overlaps”
with
a
long-running
operation
dubbed
“Dream
Job”
that
employs
job
recruitment
lures
in
email
messages
to
trigger
the
infection
sequence.
UNC2970
is
the
new
moniker
designated
by
the
threat
intelligence
firm
to
a
set
of
North
Korean
cyber
activity
that
maps
to
UNC577
(aka
Temp.Hermit),
and
which
also
comprises
another
nascent
threat
cluster
tracked
as
UNC4034.
The
UNC4034
activity,
as
documented
by
Mandiant
in
September
2022,
entailed
the
use
of
WhatsApp
to
socially
engineer
targets
into
downloading
a
backdoor
called
AIRDRY.V2
under
the
pretext
of
sharing
a
skills
assessment
test.
“UNC2970
has
a
concerted
effort
towards
obfuscation
and
employs
multiple
methods
to
do
this
throughout
the
entire
chain
of
delivery
and
execution,”
Mandiant
researchers
said
in
a
detailed
two-part
analysis,
adding
the
effort
specifically
targeted
security
researchers.
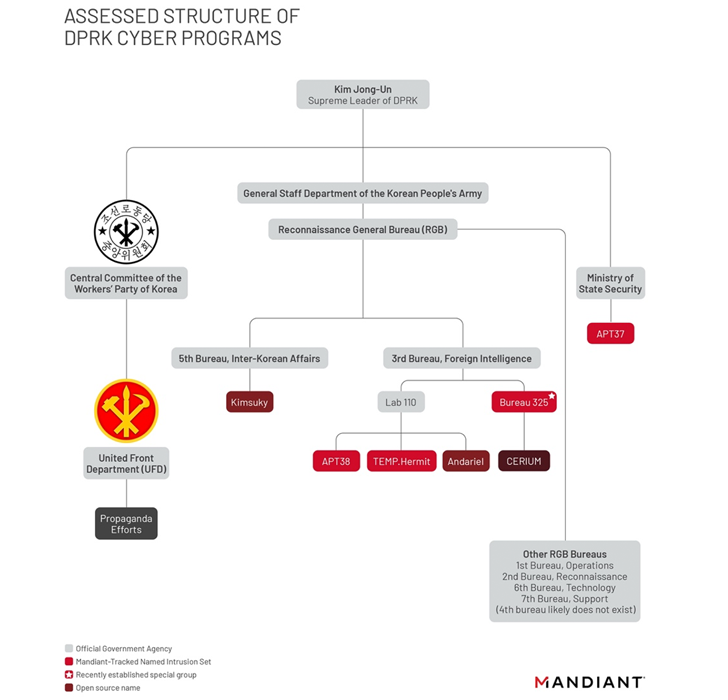
Temp.Hermit
is
one
of
the
primary
hacking
units
associated
with
North
Korea’s
Reconnaissance
General
Bureau
(RGB)
alongside
Andariel
and
APT38
(aka
BlueNoroff).
All
three
actor
sets
are
collectively
referred
to
as
the
Lazarus
Group
(aka
Hidden
Cobra
or
Zinc).
“TEMP.Hermit
is
an
actor
that
has
been
around
since
at
least
2013,”
Mandiant
noted
in
a
March
2022
report.
“Their
operations
since
that
time
are
representative
of
Pyongyang’s
efforts
to
collect
strategic
intelligence
to
benefit
North
Korean
interests.”
The
latest
set
of
UNC2970
attacks
are
characterized
by
initially
approaching
users
directly
on
LinkedIn
using
“well
designed
and
professionally
curated”
fake
accounts
posing
as
recruiters.
The
conversation
is
subsequently
shifted
to
WhatsApp,
after
which
a
phishing
payload
is
delivered
to
the
target
under
the
guise
of
a
job
description.
In
some
instances,
these
attack
chains
have
been
observed
to
deploy
trojanized
versions
of
TightVNC
(named
LIDSHIFT),
which
is
engineered
to
load
a
next-stage
payload
labeled
as
LIDSHOT
that’s
capable
of
downloading
and
executing
shellcode
from
a
remote
server.
Establishing
a
foothold
within
compromised
environments
is
achieved
by
means
of
a
C++-based
backdoor
known
as
PLANKWALK
that
then
paves
the
way
for
the
distribution
of
additional
tooling
such
as
–
-
TOUCHSHIFT
–
A
malware
dropper
that
loads
follow-on
malware
ranging
from
keyloggers
and
screenshot
utilities
to
full-featured
backdoors -
TOUCHSHOT
–
A
software
that’s
configured
to
take
a
screenshot
every
three
seconds -
TOUCHKEY
–
A
keylogger
that
captures
keystrokes
and
clipboard
data -
HOOKSHOT
–
A
tunneling
tool
that
connects
over
TCP
to
communicate
with
the
command-and-control
(C2)
server -
TOUCHMOVE
–
A
loader
that’s
designed
to
decrypt
and
execute
a
payload
on
the
machine -
SIDESHOW
–
A
C/C++
backdoor
that
runs
arbitrary
commands
and
communicates
via
HTTP
POST
requests
with
its
C2
server
UNC2970
is
also
said
to
have
leveraged
Microsoft
Intune,
an
endpoint
management
solution,
to
drop
a
bespoke
PowerShell
script
containing
a
Base64-encoded
payload
referred
to
as
CLOUDBURST,
a
C-based
backdoor
that
communicates
via
HTTP.
WEBINAR
Discover
the
Hidden
Dangers
of
Third-Party
SaaS
Apps
Are
you
aware
of
the
risks
associated
with
third-party
app
access
to
your
company’s
SaaS
apps?
Join
our
webinar
to
learn
about
the
types
of
permissions
being
granted
and
how
to
minimize
risk.
In
what’s
a
continuing
use
of
the
Bring
Your
Own
Vulnerable
Driver
(BYOVD)
technique
by
North
Korea-aligned
actors,
the
intrusions
further
employ
an
in-memory-only
dropper
called
LIGHTSHIFT
that
facilitates
the
distribution
of
another
piece
of
malware
codenamed
LIGHTSHOW.
The
utility,
besides
taking
steps
to
hinder
dynamic
and
static
analysis,
drops
a
legitimate
version
of
a
driver
with
known
vulnerabilities
to
perform
read
and
write
operations
to
kernel
memory
and
ultimately
disarm
security
software
installed
on
the
infected
host.
“The
identified
malware
tools
highlight
continued
malware
development
and
deployment
of
new
tools
by
UNC2970,”
Mandiant
said.
“Although
the
group
has
previously
targeted
defense,
media,
and
technology
industries,
the
targeting
of
security
researchers
suggests
a
shift
in
strategy
or
an
expansion
of
its
operations.”