Tick APT Targeted High-Value Customers of East Asian Data-Loss Prevention Company
A
cyberespionage
actor
known
as
Tick
has
been
attributed
with
high
confidence
to
a
compromise
of
an
East
Asian
data-loss
prevention
(DLP)
company
that
caters
to
government
and
military
entities.
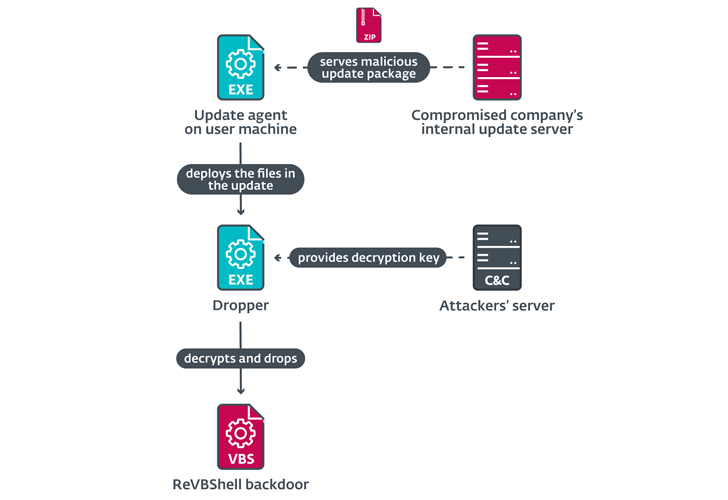
“The
attackers
compromised
the
DLP
company’s
internal
update
servers
to
deliver
malware
inside
the
software
developer’s
network,
and
trojanized
installers
of
legitimate
tools
used
by
the
company,
which
eventually
resulted
in
the
execution
of
malware
on
the
computers
of
the
company’s
customers,”
ESET
researcher
Facundo
Muñoz
said.
Tick,
also
known
as
Bronze
Butler,
Stalker
Panda,
REDBALDKNIGHT,
and
Stalker
Taurus,
is
a
suspected
China-aligned
collective
that
has
primarily
gone
after
government,
manufacturing,
and
biotechnology
firms
in
Japan.
It’s
said
to
be
active
since
at
least
2006.
Other
lesser-known
targets
include
Russian,
Singaporean,
and
Chinese
enterprises.
Attack
chains
orchestrated
by
the
group
have
typically
leveraged
spear-phishing
emails
and
strategic
web
compromises
as
an
entry
point.
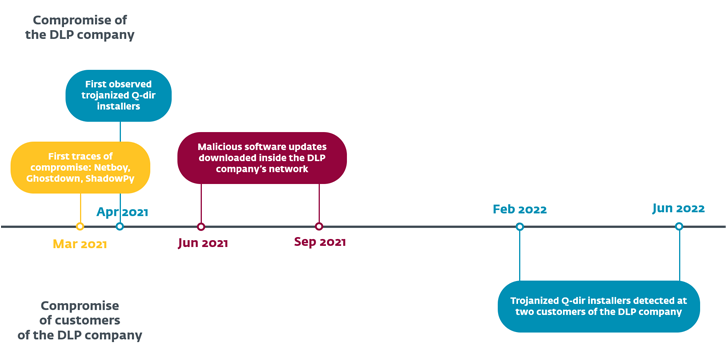
In
late
February
2021,
Tick
emerged
as
one
of
the
threat
actors
to
capitalize
on
the
ProxyLogon
flaws
in
Microsoft
Exchange
Server
as
a
zero-day
to
drop
a
Delphi-based
backdoor
in
a
South
Korean
IT
company.
Around
the
same
time,
the
adversarial
collective
is
believed
to
have
gained
access
to
the
network
of
an
East
Asian
software
developer
company
through
unknown
means.
The
name
of
the
company
was
not
disclosed.
This
was
followed
by
the
deployment
of
a
tampered
version
of
a
legitimate
application
called
Q-Dir
to
drop
an
open
source
VBScript
backdoor
named
ReVBShell,
in
addition
to
a
previously
undocumented
downloader
named
ShadowPy.
ShadowPy,
as
the
name
indicates,
is
a
Python
downloader
that’s
responsible
for
executing
a
Python
script
retrieved
from
a
remote
server.
Also
delivered
during
the
intrusion
were
variants
of
a
Delphi
backdoor
called
Netboy
(aka
Invader
or
Kickesgo)
that
comes
with
information
gathering
and
reverse
shell
capabilities
as
well
as
another
downloader
codenamed
Ghostdown.
WEBINAR
Discover
the
Hidden
Dangers
of
Third-Party
SaaS
Apps
Are
you
aware
of
the
risks
associated
with
third-party
app
access
to
your
company’s
SaaS
apps?
Join
our
webinar
to
learn
about
the
types
of
permissions
being
granted
and
how
to
minimize
risk.
“To
maintain
persistent
access,
the
attackers
deployed
malicious
loader
DLLs
along
with
legitimate
signed
applications
vulnerable
to
DLL
search-order
hijacking,”
Muñoz
said.
“The
purpose
of
these
DLLs
is
to
decode
and
inject
a
payload
into
a
designated
process.”
Subsequently,
in
February
and
June
2022,
the
trojanized
Q-Dir
installers
were
transferred
via
remote
support
tools
like
helpU
and
ANYSUPPORT
to
two
of
the
company’s
customers,
an
engineering
and
a
manufacturing
firm
located
in
East
Asia.
The
Slovak
cybersecurity
company
said
the
goal
here
was
not
to
perform
a
supply
chain
attack
against
its
downstream
customers,
but
rather
that
the
rogue
installer
was
“unknowingly”
used
as
part
of
technical
support
activities.
The
incident
is
also
likely
related
to
another
unattributed
cluster
detailed
by
AhnLab
in
May
2022
that
involved
the
use
of
Microsoft
Compiled
HTML
Help
(.CHM)
files
to
drop
the
ReVBShell
implant.