Threat
actors
are
abusing
the
legitimate
Adobe
Acrobat
Sign
service
to
distribute
the
RedLine
information
stealer.
Avast
researchers
reported
that
threat
actors
are
abusing
the
legitimate
Adobe
Acrobat
Sign
service
to
distribute
the
RedLine
information
stealer.
Adobe
Acrobat
Sign
allows
registered
users
to
sign
documents
online
and
send
a
document
signature
request
to
anyone.
This
latter
process
consists
of
generating
an
email
that
is
sent
to
the
intended
recipients.
The
message
includes
a
link
to
the
document
that
that
will
be
hosted
on
Adobe
itself.
The
experts
pointed
out
that
the
users
can
also
add
a
text
to
the
email,
this
option
can
be
abused
by
the
attackers.
Le
e-mail
generate
dai
servizi
hanno
come
indirizzo
del
mittente
‘[email protected]’,
che
ovviamente
è
un
indirizzo
e-mail
legittimo
considerato
affidabile
da
qualsiasi
soluzione
di
difesa.
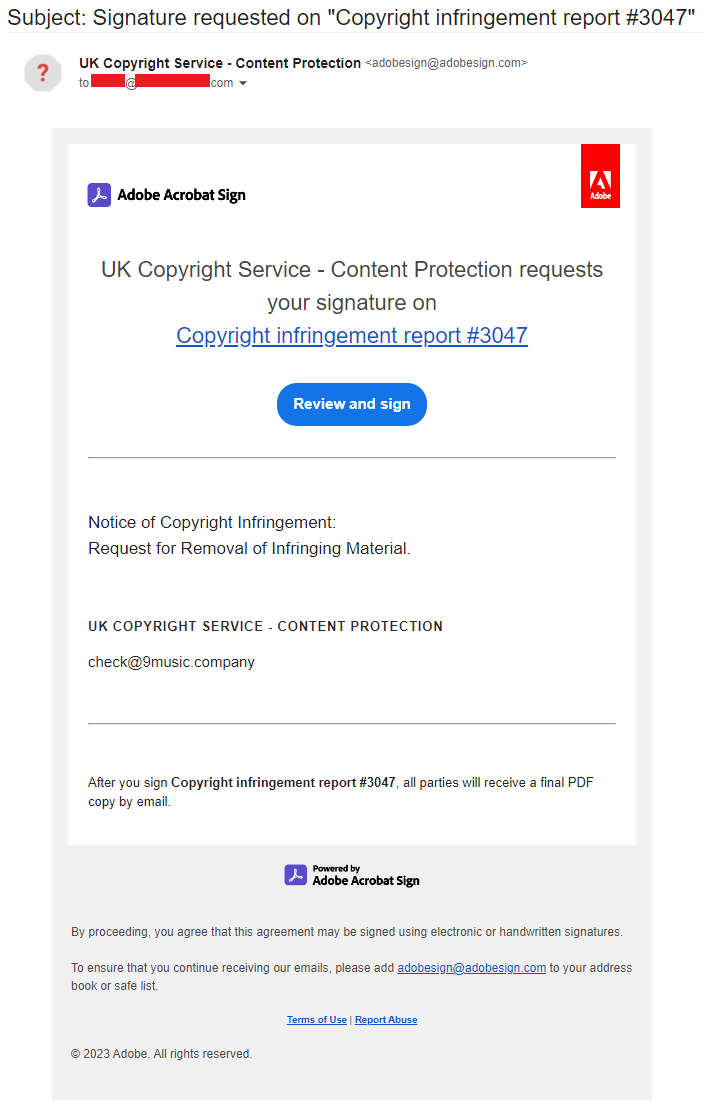
When
the
victim
clicks
on
the
“Review
and
sign”
button,
it
takes
them
to
a
page
hosted
in
“eu1.documents.adobe.com/public/”,
which
is
another
legitimate
source
that
belongs
to
Adobe.
As
I
mentioned
earlier,
people
using
this
service
can
upload
a
broad
variety
of
file
types
to
Adobe
Acrobat
Sign,
which
will
be
displayed
in
the
email
with
the
option
to
sign
them.
Avast
researchers
observed
crooks
including
text
with
a
link
in
a
document
that
attempts
to
trick
the
victim
into
thinking
that
they’ll
be
through
the
content
before
signing
it.
Once
clicked
on
the
link,
the
victim
is
redirected
to
another
site
where
they’re
asked
to
enter
a
CAPTCHA
that
is
hardcoded.
Upon
providing
the
CAPTCHA,
the
victim
will
be
asked
to
download
a
ZIP
archive
containing
the Redline
Trojan variant.
The
experts
also
observed
threat
actors
targeting
the
same
recipient
days
later
by
adding
another
link
to
the
email
sent
by
Adobe.
Upon
clicking
on
that
link,
the
recipient
is
redirected
to
a
page
that
is
hosted
on
dochub.com,
which
offers
electronic
document
signing
too.
The
archive
used
in
this
second
attack
includes
another
Redline
Trojan
variant
and
some
non-malicious
executables
belonging
to
the
Grand
Theft
Auto
V
game.
The
attackers
also
employed
a
simple
trick
in
an
attempt
to
avoid
detection,
they
artificially
increased
the
size
of
the
Redline
Trojan
to
more
than
400MB.
“One
of
the
characteristics
of
the
two
variants
of
Redline
that
these
cybercriminals
used
in
these
attacks
is
that
they’ve
artificially
increased
the
size
of
the
Trojan
to
more
than
400MB.
This
is
not
noticeable
by
the
victim
during
the
download,
as
the
file
is
compressed
and
most
of
that
artificial
size
has
just
been
filled
with
zeros.”
reads
the
anaysis
published
by
Avast.
“The
reason
for
this
is
unknown;
it’s
possible
that
the
cybercriminals
are
using
it
in
the
hope
of
bypassing
some
antivirus
engines
that
could
behave
differently
with
big
files.”
The
experts
concludes
that
the
abuse
of
Adobe
Acrobat
Sign
to
distribute
malware
is
a
new
technique
used
by
attackers
in
targeted
attacks.
“Our
team
has
yet
to
detect
other
attacks
using
this
technique;
nevertheless,
we
fear
that
it
may
become
a
popular
choice
for
cybercriminals
in
the
near
future.”
concludes
the
report.
Follow
me
on
Twitter:
@securityaffairs
and
Facebook
and
Mastodon
(SecurityAffairs –
hacking,
malware)







