The
Acropalypse
flaw
in
the
Markup
tool
of
Google
Pixel
allowed
the
partial
recovery
of
edited
or
redacted
screenshots
and
images.
Security
researchers
Simon
Aarons
and
David
Buchanan
have
discovered
a
vulnerability,
named
‘Acropalypse,’
in
the
Markup
tool
of
Google
Pixel.
The
Markup
tool
is
a
built-in
Markup
utility,
released
with
Android
9
Pie
that
allows
Google
Pixel
users
to
edit
(crop,
add
text,
draw,
and
highlight)
screenshots.
The
vulnerability
allowed
the
partial
recovery
of
the
original,
unedited
image
data
of
a
cropped
and/or
redacted
screenshot.
Aarons
described
how
to
exploit
the
vulnerability
via
Twitter.
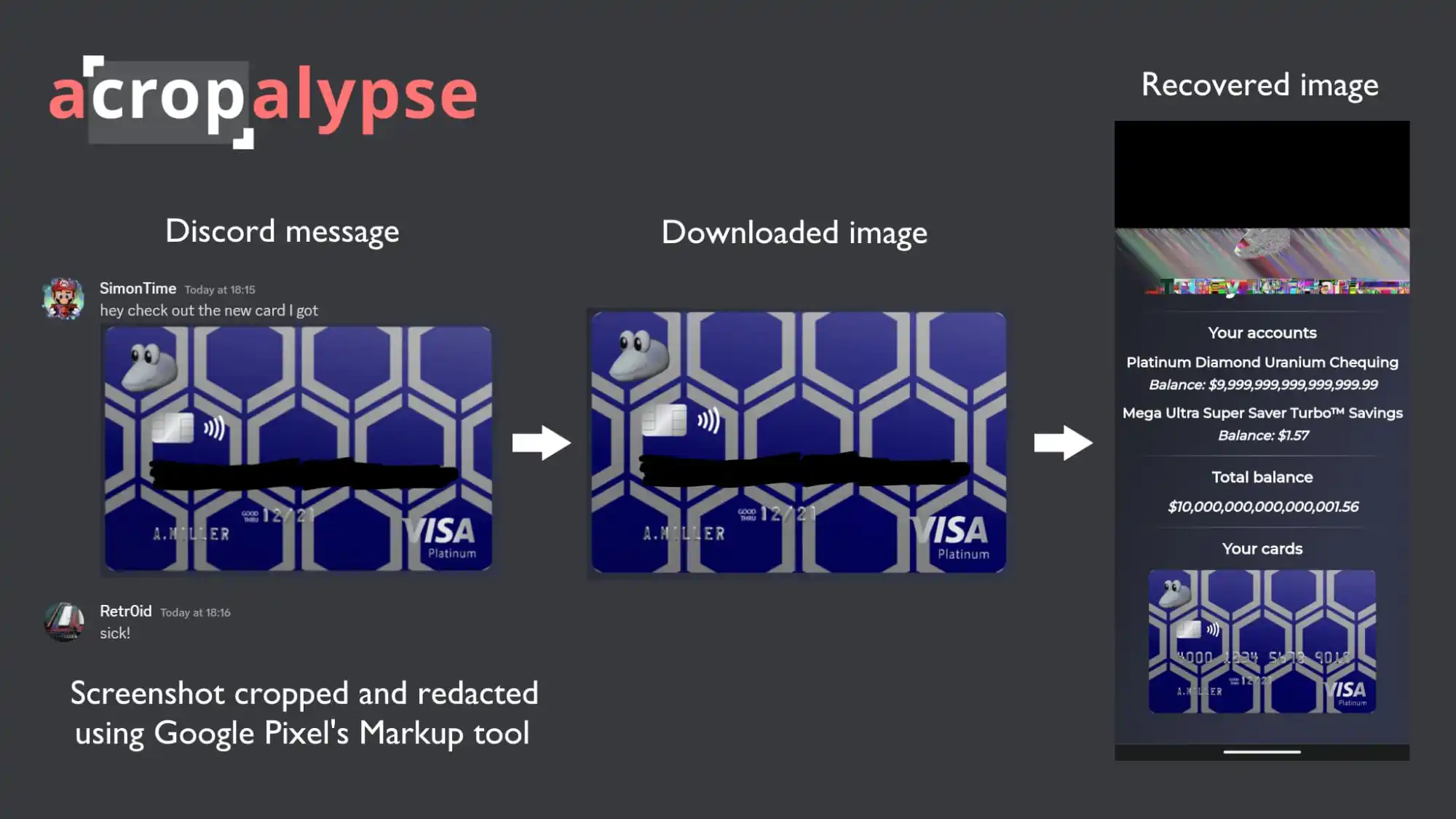
Let’s
imagine
a
user
uploading
a
screenshot
from
a
bank
app
or
website
that
includes
an
image
of
his
payment
card.
The
user
uses
the
Markup’s
Pen
tool
to
remove
the
payment
card
data
number
from
the
image
before
sharing
it
on
a
service,
like
Discord.

The
vulnerability
in
the
Markup
tool
could
have
allowed
an
attacker
that
downloaded
the
image
to
perform a
“partial
recovery
of
the
original,
unedited
image
data
of
cropped
and/or
redacted
screenshot.”
The
exploitation
of
the
bug
can
allow
an
attacker
to
remove
the
black
lines
used
to
hide
the
card
number,
as
well
as
~80%
of
the
full
screenshot,
which
might
include
other
sensitive
information.
“The
third
panel
is
titled
“Recovered
image”
and
depicts
a
fake
bank
website.
The
top
20%
of
the
image
is
corrupted,
but
the
remainder
of
the
image
–
including
a
photo
of
the
credit
card
with
its
number
visible
–
is
fully
recovered.”
Aarons
explained.
The
duo
has
also
published
a
demo
utility that
allows
the
owners
of
the
Pixel
devices
to
test
their
own
redacted
images
and
see
if
they
are
recoverable.
The
experts
also
announced
that
they
will
publish
a
FAQ
shortly.
“When
an
image
is
cropped
using
Markup,
it
saves
the
edited
version
in
the
same
file
location
as
the
original.
However,
it
does
not
erase
the
original
file
before
writing
the
new
one.
If
the
new
file
is
smaller,
the
trailing
portion
of
the
original
file
is
left
behind,
after
the
new
file
is
supposed
to
have
ended.”
states
the
9to5google
website.
According
to
a
technical
analysis
published
by
David
Buchanan,
the
root
cause
of
the
flaw
was
due
to
this
horrible
bit
of
API
“design”: https://issuetracker.google.com/issues/180526528.
“Google
was
passing
“w”
to
a
call
to
parseMode(),
when
they
should’ve
been
passing
“wt”
(the
t
stands
for
truncation).
This
is
an
easy
mistake,
since
similar
APIs
(like
POSIX
fopen)
will
truncate
by
default
when
you
simply
pass
“w”.
Not
only
that,
but
previous
Android
releases
had
parseMode(“w”)
truncate
by
default
too!
This
change
wasn’t
even
documented
until
some
time
after
the
aforementioned
bug
report
was
made.”
wrote
Buchanan.
“The
end
result
is
that
the
image
file
is
opened
without
the
O_TRUNC
flag,
so
that
when
the
cropped
image
is
written,
the
original
image
is
not
truncated.
If
the
new
image
file
is
smaller,
the
end
of
the
original
is
left
behind.”
The
vulnerability,
tracked
as
CVE-2023-21036,
was
reported
to
Google
in
January
2023,
and
the
IT
giant
addressed
it
on
March
13,
2023.
Despite
Google
has
addressed
the
issue,
the
images
edited
with
the
tool
and
shared
in
the
past
five
years
are
vulnerable
to
the
Acropalypse
attack.
The
experts
verified
that
there
are
a
lot
of
cropped
screenshots
on
platforms
like
Discord.
Buchanan
wrote
a
script
to
scrape
his
own
message
history
to
look
for
vulnerable
images
and
discovered
that
there
were
lots
of
them.
“The
worst
instance
was
when
I
posted
a
cropped
screenshot
of
an
eBay
order
confirmation
email,
showing
the
product
I’d
just
bought.
Through
the
exploit,
I
was
able
to
un-crop
that
screenshot,
revealing
my
full
postal
address
(which
was
also
present
in
the
email).
That’s
pretty
bad!”
Buchanan
concluded.
Follow
me
on
Twitter:
@securityaffairs
and
Facebook
and
Mastodon
(SecurityAffairs –
hacking,
Google
Pixel)