The number of devices infected by the MyloBot botnet is rapidly increasing
Researchers
warn
that
the
MyloBot
botnet
is
rapidly
spreading
and
it
is
infecting
thousands
of
systems
worldwide.
The
MyloBot
botnet
has
been
active
since
2017
and
was first
detailed by
cybersecurity
firm
Deep
Instinct
in
2018.
MyloBot
is
a
highly
evasive
Windows
botnet
that
supports
advanced
anti-analysis
techniques.
The
first
sample
of
the
bot
analyzed
by
the
experts
(dated
October
20,
2017)
had
three
different
stages.
Since
November
2018,
BitSight
researchers
started
sinkholing
the
botnet.
In
2018,
the
botnet’s
proxy
sample
contained
a
lot
of
hardcoded
DGA
domains,
allowing
the
researchers
to
track
almost
any
bot.
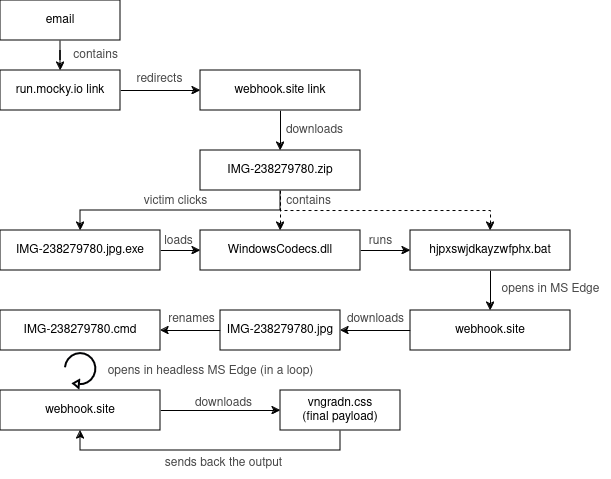
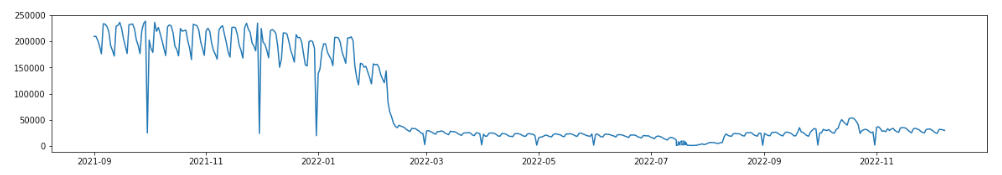
The
researchers
discovered
that
it
reached
a
maximum
of
250,000
unique
daily
infected
machines
at
the
beginning
of
2020.
The
latest
version
of
the
botnet,
which
appeared
in
early
2022,
doesn’t
contain
hardcoded
DGA
domains,
for
this
reason,
the
experts
were
not
able
to
get
a
complete
estimation
of
the
number
of
infected
systems.
Then
the
experts
started
monitoring
Mylobot
downloader’s
domains
to
observe
the
botnet
evolution. They
also
noticed
a
link
between
the
Mylobot
and
the
residential
proxy
service
BHProxies,
a
circumstance
that
indicates
that
the
compromised
machines
are
being
used
by
the
latter.
Researchers
warn
that
the
botnet
is
rapidly
growing,
they
observed
it
is
infecting
thousands
of
systems
worldwide.
“We
are
currently
seeing
more
than
50,000
unique
infected
systems
every
day,
but
we
believe
we
are
only
seeing
part
of
the
full
botnet,
which
may
lead
to
more
than
150,000
infected
computers
as
advertised
by
BHProxies’
operators.”
reads
the
report
published
by
Bitsight.

Most
of
the
infections
were
observed
in
India,
followed
by
the
US,
Indonesia,
and
Iran.
Additional
details,
including
indications
of
compromise
(IoCs)
are
reported
in
the
analysis
published
by
the
experts.
Follow
me
on
Twitter:
@securityaffairs
and
Facebook
and
Mastodon
(SecurityAffairs –
hacking,
MyloBot
botnet)