As
the
digital
age
evolves
and
continues
to
shape
the
business
landscape,
corporate
networks
have
become
increasingly
complex
and
distributed.
The
amount
of
data
a
company
collects
to
detect
malicious
behaviour
constantly
increases,
making
it
challenging
to
detect
deceptive
and
unknown
attack
patterns
and
the
so-called
“needle
in
the
haystack”.
With
a
growing
number
of
cybersecurity
threats,
such
as
data
breaches,
ransomware
attacks,
and
malicious
insiders,
organizations
are
facing
significant
challenges
in
successfully
monitoring
and
securing
their
networks.
Furthermore,
the
talent
shortage
in
the
field
of
cybersecurity
makes
manual
threat
hunting
and
log
correlation
a
cumbersome
and
difficult
task.
To
address
these
challenges,
organizations
are
turning
to
predictive
analytics
and
Machine
Learning
(ML)
driven
network
security
solutions
as
essential
tools
for
securing
their
networks
against
cyber
threats
and
the
unknown
bad.
The
Role
of
ML-Driven
Network
Security
Solutions
ML-driven
network
security
solutions
in
cybersecurity
refer
to
the
use
of
self-learning
algorithms
and
other
predictive
technologies
(statistics,
time
analysis,
correlations
etc.)
to
automate
various
aspects
of
threat
detection.
The
use
of
ML
algorithms
is
becoming
increasingly
popular
for
scalable
technologies
due
to
the
limitations
present
in
traditional
rule-based
security
solutions.
This
results
in
the
processing
of
data
through
advanced
algorithms
that
can
identify
patterns,
anomalies,
and
other
subtle
indicators
of
malicious
activity,
including
new
and
evolving
threats
that
may
not
have
known
bad
indicators
or
existing
signatures.
Detecting
known
threat
indicators
and
blocking
established
attack
patterns
is
still
a
crucial
part
of
overall
cyber
hygiene.
However,
traditional
approaches
using
threat
feeds
and
static
rules
can
become
time-consuming
when
it
comes
to
maintaining
and
covering
all
the
different
log
sources.
In
addition,
Indicators
of
Attack
(IoA)
or
Indicators
of
Compromise
(IoC)
may
not
be
available
at
the
time
of
an
attack
or
are
quickly
outdated.
Consequently,
companies
require
other
approaches
to
fill
this
gap
in
their
cybersecurity
posture.
In
summary,
the
mentioned
drawbacks
of
rule-based
security
solutions
highlight
the
significance
of
taking
a
more
holistic
approach
to
network
security,
which
should
nowadays
include
ML-powered
Network
Detection
and
Response
(NDR)
solutions
to
complement
traditional
detection
capabilities
and
preventive
security
measures.
The
Benefits
of
ML
for
Network
Security
So,
how
is
Machine
Learning
(ML)
shaping
the
future
of
network
security?
The
truth
is
ML-powered
security
solutions
are
bringing
about
a
significant
transformation
in
network
security
by
providing
security
teams
with
numerous
benefits
and
enhancing
the
overall
threat
detection
capabilities
of
organizations:
-
Big
data
analytics:With
the
ever-increasing
amount
of
data
and
different
log
sources,
organisations
must
be
able
to
process
vast
amounts
of
information
in
real-time,
including
network
traffic
logs,
endpoints,
and
other
sources
of
information
related
to
cyber
threats.
In
this
regard,
ML
algorithms
can
aid
in
the
detection
of
security
threats
by
identifying
patterns
and
anomalies
that
may
otherwise
go
unnoticed.
Consequently,
the
ability
and
flexibility
of
a
solution
to
incorporate
different
log
sources
should
be
a
key
requirement
for
threat
detection
capabilities. -
Automated
analysis
of
anomalous
behavior:
AI
enables
a
much-required
health
monitoring
of
network
activity
by
utilising
the
analysis
of
normal
network
traffic
as
a
baseline.
With
the
help
of
automated
correlation
and
clustering,
outliers
and
unusual
behavior
can
be
detected,
reducing
the
need
for
manual
detection
engineering
and
threat
hunting.
Key
questions
to
be
answered
include
“what
is
the
activity
of
other
clients
in
the
network?”
and
“is
a
client’s
behavior
in
line
with
its
own
previous
activities?”
These
approaches
allow
for
the
detection
of
unusual
behaviors
like
domain-generated
algorithms
(DGA)
domains,
volume-based
irregularities
in
network
connections,
and
unusual
communication
patterns
(e.g.,
lateral
movement)
in
the
network.
Therefore,
comparing
a
client’s
current
behavior
with
that
of
its
peers
serves
as
a
suitable
baseline
for
identifying
subtle
anomalies. -
Detect
unknown
attacks
in
real-time:
Whileit
is
relatively
easy
to
directly
detect
known
bad
indicators
(specific
IP
addresses,
domains
etc.),
many
attacks
can
go
undetected
when
these
indicators
are
not
present.
If
that
is
the
case,
statistics,
time
and
correlation-based
detections
are
of
enormous
value
to
detect
unknown
attack
patterns
in
an
automated
manner.
By
incorporating
algorithmic
approaches,
traditional
security
solutions
based
on
signatures
and
indicators
of
compromise
(IoC)
can
be
enhanced
to
become
more
self-sufficient
and
less
reliant
on
known
malware
indicators. -
Self-learning
detection
capabilities:
ML-driven
solutions
learn
from
past
events
in
order
to
continuously
improve
their
threat
detection
capabilities,
threat
scoring,
clustering
and
network
visualisations.
This
may
involve
training
the
algorithms
themselves
or
adjusting
how
information
is
presented
based
on
feedback
from
analysts. -
Enhance
Incident
Response:By
learning
from
an
analyst’s
past
incident
response
activities,
ML
can
automate
certain
aspects
of
the
incident
response
process,
minimizing
the
time
and
resources
required
to
address
a
security
breach.
This
can
involve
using
algorithms
to
analyze
text
and
evidence,
identifying
root
causes
and
attack
patterns.
Example
of
an
ML-driven
Network
Security
Solution
When
it
comes
to
ML-driven
Network
Detection
&
Response
(NDR)
solutions
that
incorporate
the
outlined
benefits,
ExeonTrace
stands
out
as
a
leading
network
security
solution
in
Europe.
Based
on
award-winning
ML
algorithms,
which
incorporate
a
decade
of
academic
research,
ExeonTrace
provides
organizations
with
advanced
ML
threat
detection
capabilities,
complete
network
visibility,
flexible
log
source
integration
and
big
data
analytics.
In
addition,
the
algorithms
rely
on
metadata
analysis
instead
of
actual
payloads
which
makes
them
unaffected
by
encryption,
completely
hardware-free
and
compatible
with
most
cybersecurity
infrastructures.
As
a
result,
ExeonTrace
is
able
to
process
raw
log
data
into
powerful
graph
databases,
which
are
then
analyzed
by
supervised
and
unsupervised
ML-models.
Through
correlation
and
event
fusion,
the
algorithms
can
accurately
pinpoint
high-fidelity
anomalies
and
subtle
cues
of
malicious
behavior,
even
when
dealing
with
novel
or
emerging
cyber
threats
that
may
lack
established
signatures
or
known
malicious
indicators.
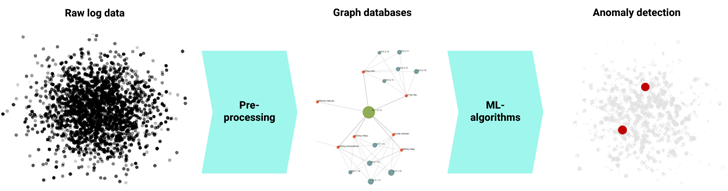 |
|
Security Analytics Pipeline: Detection of network anomalies through ML |
Conclusion
As
the
threat
of
cyber
attacks
becomes
increasingly
complex,
organizations
must
go
beyond
traditional
security
measures
to
protect
their
networks.
As
a
result,
many
companies
are
now
turning
to
Machine
Learning
(ML)
and
predictive
analytics
to
strengthen
their
security
defenses.
In
this
regard,
ML-driven
Network
Detection
&
Response
(NDR)
solutions,
such
as
ExeonTrace,
are
designed
to
help
organizations
stay
ahead
of
the
ever-evolving
threat
landscape.
By
utilizing
advanced
ML
algorithms
that
analyze
network
traffic
and
application
logs,
ExeonTrace
offers
organizations
quick
detection
and
response
to
even
the
most
sophisticated
cyberattacks.
 |
|
ExeonTrace Platform: Network visibility |
Book
a
free
demo
to
discover
how
ExeonTrace
leverages
ML
algorithms
to
make
your
organisation
more
cyber
resilient
–
quickly,
reliable
and
completely
hardware-free.
this
article
interesting?
Follow
us
on
and
to
read
more
exclusive
content
we
post.