A
sophisticated
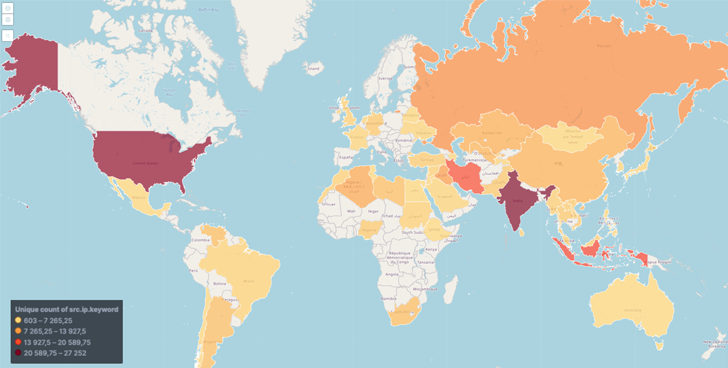
botnet
known
as
MyloBot
has
compromised
thousands
of
systems,
with
most
of
them
located
in
India,
the
U.S.,
Indonesia,
and
Iran.
That’s
according
to
new
findings
from
BitSight,
which
said
it’s
“currently
seeing
more
than
50,000
unique
infected
systems
every
day,”
down
from
a
high
of
250,000
unique
hosts
in
2020.
Furthermore,
an
analysis
of
MyloBot’s
infrastructure
has
found
connections
to
a
residential
proxy
service
called
BHProxies,
indicating
that
the
compromised
machines
are
being
used
by
the
latter.
MyloBot,
which
emerged
on
the
threat
landscape
in
2017,
was
first
documented
by
Deep
Instinct
in
2018,
calling
out
its
anti-analysis
techniques
and
its
ability
to
function
as
a
downloader.
“What
makes
Mylobot
dangerous
is
its
ability
to
download
and
execute
any
type
of
payload
after
it
infects
a
host,”
Lumen’s
Black
Lotus
Labs
said
in
November
2018.
“This
means
at
any
time
it
could
download
any
other
type
of
malware
the
attacker
desires.”
Last
year,
the
malware
was
observed
sending
extortion
emails
from
hacked
endpoints
as
part
of
a
financially
motivated
campaign
seeking
over
$2,700
in
Bitcoin.
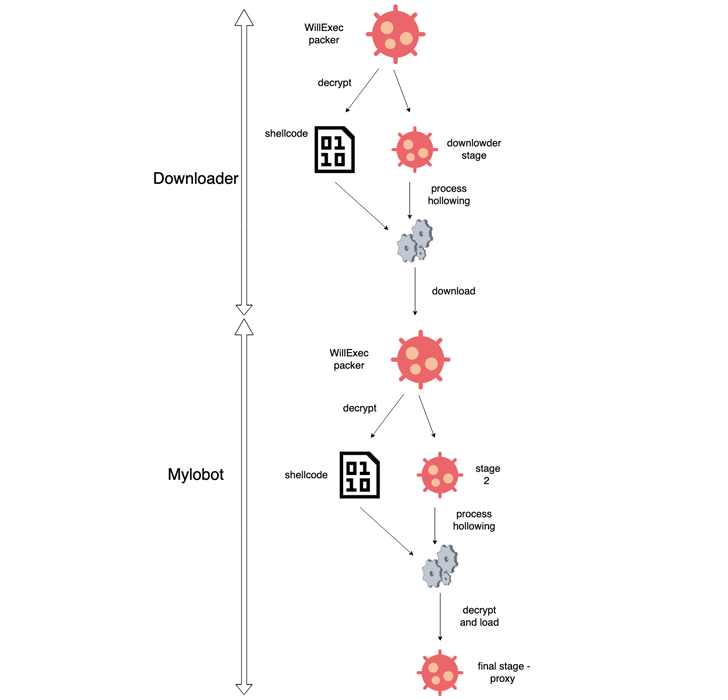
MyloBot
is
known
to
employ
a
multi-stage
sequence
to
unpack
and
launch
the
bot
malware.
Notably,
it
also
sits
idle
for
14
days
before
attempting
to
contact
the
command-and-control
(C2)
server
to
sidestep
detection.
The
primary
function
of
the
botnet
is
to
establish
a
connection
to
a
hard-coded
C2
domain
embedded
within
the
malware
and
await
further
instructions.
“When
Mylobot
receives
an
instruction
from
the
C2,
it
transforms
the
infected
computer
into
a
proxy,”
BitSight
said.
“The
infected
machine
will
be
able
to
handle
many
connections
and
relay
traffic
sent
through
the
command-and-control
server.”
Subsequent
iterations
of
the
malware
have
leveraged
a
downloader
that,
in
turn,
contacts
a
C2
server,
which
responds
with
an
encrypted
message
containing
a
link
to
retrieve
the
MyloBot
payload.
The
evidence
that
MyloBot
could
be
a
part
of
something
bigger
stems
from
a
reverse
DNS
lookup
of
one
of
the
IP
addresses
associated
with
the
botnet’s
C2
infrastructure
has
revealed
ties
to
a
domain
named
“clients.bhproxies[.]com.”
The
Boston-based
cybersecurity
company
said
it
began
sinkholing
MyloBot
in
November
2018
and
that
it
continues
to
see
the
botnet
evolve
over
time.
this
article
interesting?
Follow
us
on
and
to
read
more
exclusive
content
we
post.