A
misconfiguration
of
Swiss
real
estate
agency
Neho’s
systems
exposed
sensitive
credentials
to
the
public.
Neho,
a
Switzerland-based
real
estate
agency,
leaked
credentials
recently,
potentially
allowing
threat
actors
to
prey
on
sensitive
data
about
the
company
and
its
clients.
-
A
misconfiguration
of
Swiss
real
estate
agency
Neho’s
systems
exposed
sensitive
credentials
to
the
public. -
Using
leaked
data,
threat
actors
could
potentially
breach
the
company’s
internal
systems
and
hijack
official
communication
channels. -
Real
estate
agencies
handle
sensitive
data,
including
customers’
personally
identifiable
information,
bank
account
details,
and
other
data
highly
valued
by
cybercriminals.
Ensuring
cybersecurity
is
vital. -
Cybernews
reached
out
to
Neho
and
the
company
fixed
the
issue.
The
Cybernews
research
team
discovered
a
misconfiguration
in
the
Neho.ch
website
that
exposed
sensitive
credentials
to
the
public,
potentially
allowing
threat
actors
to
take
over
the
company’s
systems.
The
company’s
website,
which
features
real
estate
classifieds,
receives
monthly
traffic
of
around
120,000
visitors.
With
an
annual
revenue
of
almost
$12
million,
Neho
claims
to
be
the
first
commission-free
real
estate
agency
in
the
country.
Cybernews
reached
out
to
Neho,
and
the
company
secured
access
to
their
systems.
Public
access
to
the
company’s
systems
On
March
18th,
the
Cybernews
research
team
discovered
a
publicly
accessible
environment
file
(.env)
hosted
on
the
official
Neho’s
website.
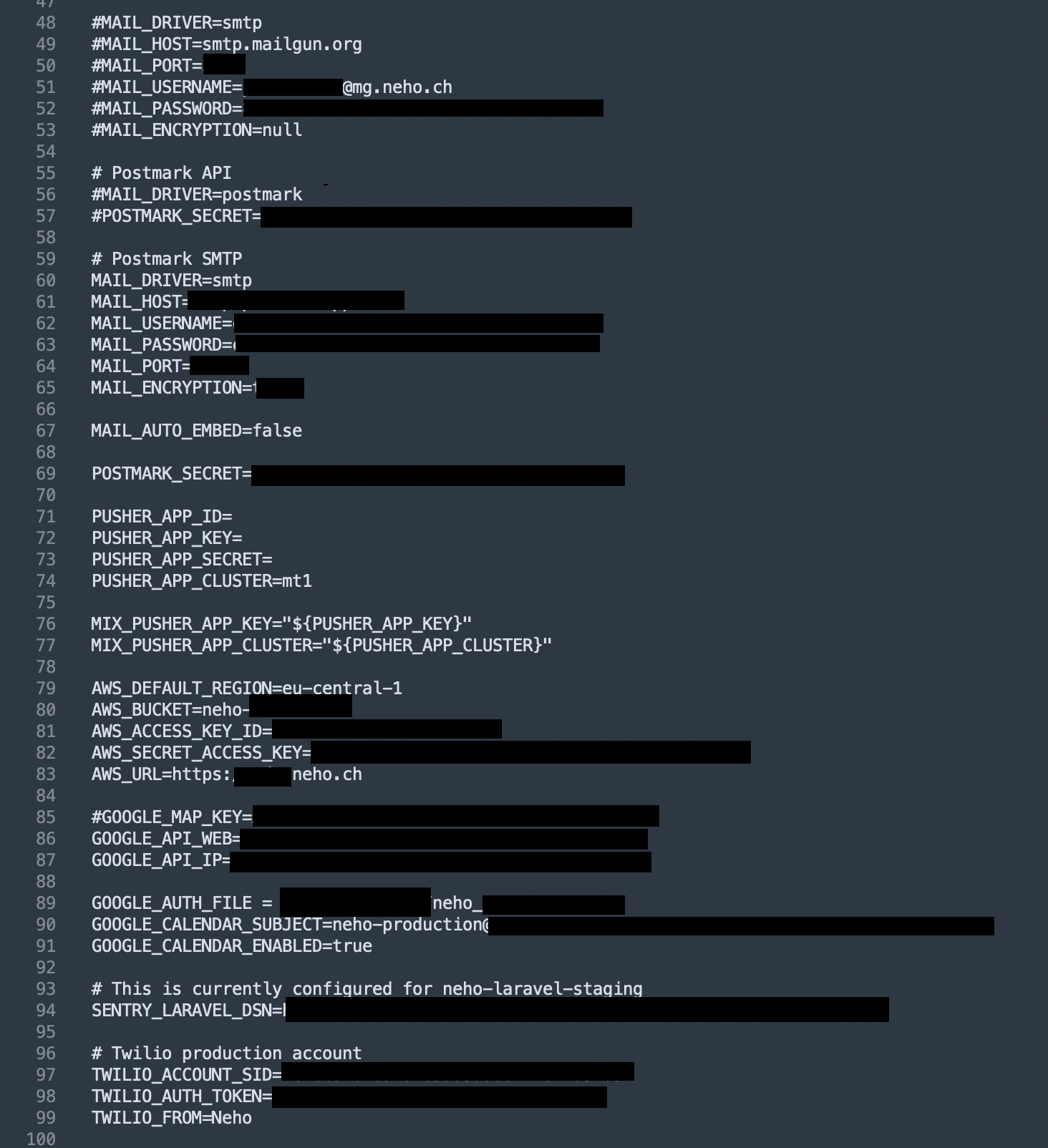
The
file
contained
PostgreSQL
and
Redis
databases
credentials,
including
host,
port,
username,
and
password.

environment
file
|
Image
by
Cybernews
Exposure
of
these
credentials
is
particularly
dangerous
as
it
grants
threat
actors
access
to
the
content
of
the
databases.
Given
that
the
databases
are
connected
to
the
internet,
it
makes
it
easier
for
attackers
to
access
them.
Among
the
leaked
data,
researchers
found Amazon
Web
Services (AWS)
Bucket
credentials
–
key
ID
and
secret.
Judging
by
the
name
–
‘neho-media’,
the
bucket
most
likely
stored
images.
While,
for
legal
reasons,
researchers
cannot
define
the
exact
content
of
the
bucket,
there’s
a
possibility
that
it
might
also
contain
sensitive
files
related
to
the
agency’s
customers
or
properties.
Researchers
also
stumbled
upon
Elasticsearch
AWS
credentials.
Typically,
these
instances
serve
as
potential
treasure
troves,
housing
crucial
information
such
as
customer
records,
payment
data,
and
a
myriad
of
other
invaluable
details.
Credentials
leaked
included:
-
PostgreSQL
database
host,
port,
name,
and
password -
Redis
database
host,
port,
and
password -
Mailgun
host,
username,
and
password -
Postmark
API
and
SMTP
credentials -
AWS
Bucket
access
key
ID
and
secret -
Twilio
Account
credentials -
Aircall
API
and
tokens -
Elastic
search
AWS
credentials -
Google
Client
ID
and
Secret -
Facebook
Client
ID
and
secret -
Trustpilot
API
key
and
secret -
Pricehubble
credentials -
Movu.ch
token -
Canny
ID,
keys
and
tokens -
TravelTime
API
Corporate
communication
channels
at
risk
Another
piece
of
sensitive
information
observed
was
the
application
programming
interface
(API)
and
Simple
Mail
Transfer
Protocol
(SMTP)
credentials
for
Postmark
email-sending
services.
By
exploiting
these
credentials,
a
malicious
actor
could
use
the
company’s
official
email
to
deploy
phishing
campaigns
and
send
spam.
Among
leaked
credentials,
researchers
also
found
the
host,
username,
and
password
for
Mailgun
email
services
used
by
the
company.
If
these
credentials
were
to
fall
into
the
hands
of
malicious
actors,
it
could
enable
them
to
read
and
send
emails.
This
poses
a
significant
threat
as
it
opens
the
door
for
phishing
attacks
to
be
initiated
using
a
legitimate
Neho
email
address.
The
leaked
data
shows
that
the
company
has
been
using
Aircall,
a
cloud-based
call
center
software,
and Twilio,
a
communication
tool
for
making
and
receiving
phone
calls
and
text
messages.

environment
file
|
Image
by
Cybernews
These
communication
channels
between
the
company
and
clients
were
at
risk.
The
publicly
accessible
environment
file
exposed
the
Aircall
API
and
tokens,
as
well
as
the
Twilio
credentials,
enabling
threat
actors
to
hijack
them.
The
file
also
contained
Facebook
App
ID
with
a
secret
key,
and
Google’s
Client
ID
and
secret
key.
Leaking
these
credentials
is
a
cause
of
concern,
as
threat
actors
could
use
them
to
either
hijack
the
company’s
Facebook
and
Google
applications
or
request
user
data.
Additionally,
the
API
key
and
secret
used
to
access
Trustpilot,
a
review
platform,
were
exposed.
These
credentials
could
potentially
grant
access
to
Neho’s
account
on
the
platform,
enabling
malicious
actors
to
edit
or
delete
data
related
to
Neho,
and
damaging
its
reputation.
A
number
of
less
critical
credentials
were
also
exposed,
including
Pricehubble
credentials,
Movu.ch
token,
Canny
ID,
keys
and
tokens,
and
TravelTime
API.

environment
file
|
Image
by
Cybernews
What’s
at
stake?
The
type
and
volume
of
data
exposed
by
the
company
enable
threat
actors
to
launch
a
multitude
of
attacks
on
both
the
website
itself
and
its
users
with
relative
ease.
Cyberattacks
on
real
estate
agencies
are
hazardous,
as
the
companies
are
usually
entrusted
with
a
significant
amount
of
sensitive
data,
encompassing
crucial
personal
identifiable
information
(PII)
of
customers,
as
well
as
their
bank
account
details.
This
data
holds
immense
appeal
for
cybercriminals.
Using
Neho’s
leaked
data,
a
malicious
actor
might
have
completely
taken
over
the
company’s
internal
systems
and
used
privilege
escalation
and
lateral
movement
for
further
exploitation.
Threat
actors
could
leverage
the
data
present
in
the
databases
to
initiate
a
range
of
malicious
activities,
including
phishing
attacks,
fraudulent
marketing
campaigns,
and
identity
fraud.
Apart
from
the
risks
of
ransom
and
data
theft,
attackers
may
also
opt
to
duplicate
private
datasets
to
facilitate
further
intrusions.
The
company’s
response
In
their
official
statement,
the
company
stated
that
they
removed
the
exposed
environment
file
“immediately.”
“We
would
like
to
stress
that
we
often
rotate
our
keys
and
that
the
file
was,
for
the
most
part,
holding
obsolete
data
alongside
inactive
services
that
we
don’t
use
anymore,”
claimed
the
company.
Are
you
interested
to
know
how
to
avoid
the
risks?
Give
a
look
at
the
original
post
at
https://cybernews.com/security/neho-real-estate-agency-data-leak/
About
the
author:
Paulina
Okunytė,
Journalist
at
CyberNews
Follow
me
on
Twitter: @securityaffairs and Facebook and Mastodon
(SecurityAffairs – hacking, Neho)










