Researchers
detected
a
cyberespionage
campaign
in
Libya
that
employs
a
new
custom,
modular
backdoor
dubbed
Stealth
Soldier.
Experts
at
the
Check
Point
Research
team
uncovered
a
series
of
highly-targeted
espionage
attacks
in
Libya
that
employ
a
new
custom
modular
backdoor
dubbed
Stealth
Soldier.
Stealth
Soldier is
surveillance
software
that
allows
operators
to
spy
on
the
victims
and
exfiltrate
collected
data.
The
researchers
noticed
that
the
Stealth
Soldier
infrastructure
has
some
overlaps
with
infrastructure
the The
Eye
on
the
Nile, a
campaign
that
targeted
journalists
and
human
rights
activists
in
Egypt
in
2019.
The
experts
suspect
that
the
recent
attack
could
be
linked
to
the
same
threat
actor.
The
newest
version
of
the
malware
(Version
9)
was
likely
employed
in
February
2023,
while
the
oldest
version
discovered
by
the
researchers
(Version
6)
dates
back
to
October
2022.
“Stealth
Soldier malware
is
an
undocumented
backdoor
that
primarily
operates
surveillance
functions
such
as
file
exfiltration,
screen
and
microphone
recording,
keystroke
logging
and
stealing
browser
information.”
reads
the
report
published
by
Check
Point.
Some
of
the
C2
domains
used
by
the
attacker
masquerade
as
sites
belonging
to
the
Libyan
Foreign
Affairs
Ministry.
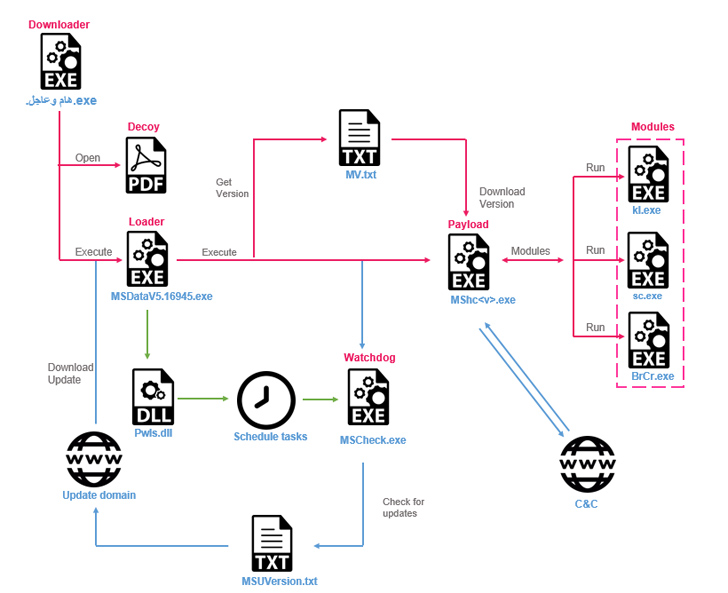
The
infection
chain
commences
with
the
execution
of
the
downloader
delivered
via
social
engineering
attacks.
The
experts
explained
that
the
infection
chain
is
complex
and
involves
six
files
downloaded
from
the
C&C
server.
Below
are
the
main
files
used
in
the
infection
chain:
-
Loader
(MSDataV5.16945.exe)
–
Downloads
PowerPlus,
an
internal
module
to
run
PowerShell
commands,
and
uses
it
to
create
persistence
for
the
watchdog.
Runs
Stealth
Soldier’s
final
payload. -
Watchdog
(MSCheck.exe)
–
Periodically
checks
for
an
updated
version
of
the
Loader
and
runs
it.
Persistent
using
Schedule
Task
and
the
Registry
Run
key. -
Payload
(MShc.txt)
–
Collects
data,
receives
commands
from
the
C&C
server,
and
executes
modules.
The
downloader
fetch
and
opens
a
decoy
empty
PDF
file
from
the
C2,
then
downloads
a
loader
from
filecloud.
The
loader
downloads
a
.NET
module
called
PowerPlus
and
executes
PowerShell
code.
PowerPlus
is
used
to
run
two
commands,
one
of
them
to
maintain
persistence
and
the
other
for
querying
details
about
the
task
into
a
file
named
DRSch.
The
process
involves
the
use
of
a
watchdog
as
an
update
mechanism.
In
the
last
stage
of
the
infection
chain,
the
malware
decrypts
the
payload
before
running
it
as
a
shellcode,
which
loads
the
payload
and
passes
the
execution
to
its
main
logic.
The
malware
supports
different
types
of
commands,
some
of
them
are
in
the
form
of
plugins
that
are
downloaded
from
the
C2.
Other
commands
are
modules
inside
the
malware-
“The
investigation
suggests
that
the
attackers
behind
this
campaign
are
politically
motivated
and
are
utilizing
the
Stealth
Soldier
malware
and
a
significant
network
of
phishing
domains
to
conduct
surveillance
and
espionage
operations
against
Libyan
and
Egyptian
targets.”
Check
Point
concludes.
“Given
the
modularity
of
the
malware
and
the
use
of
multiple
stages
of
infection,
it
is
likely
that
the
attackers
will
continue
to
evolve
their
tactics
and
techniques
and
deploy
new
versions
of
this
malware
in
the
near
future.
Finally,
our
analysis
revealed
a
connection
to
the
previously
exposed
“Eye
on
the
Nile”
campaign.”
Follow
me
on
Twitter: @securityaffairs and Facebook and Mastodon
(SecurityAffairs – hacking, Stealth
Soldier)







