Researchers
discovered
that
the
Clop
ransomware
gang
was
looking
for
a
zero-day
exploit
in
the
MOVEit
Transfer
since
2021.
Kroll
security
experts
discovered
that
the
Clop
ransomware
gang
was
looking
for
a
zero-day
exploit
in
the
MOVEit
Transfer
since
2021.
Kroll
investigated
the
exploitation
attempts
for
the
MOVEit
Transfer
vulnerability
and
discovered
that
Clop
threat
actors
were
likely
experimenting
with
how
to
exploit
this
issue
as
far
back
as
2021.
The
discovery
demonstrates
the
level
of
sophistication
of
this
specific
ransomware
gang
and
its
important
capabilities.
The
threat
actors
were
planning
and
organizing
attacks
on
a
large
scale
by
exploiting
flaws
like
MOVEit
Transfer
of
GoAnywhere
MFT.
The
experts
speculate
the
Clop
group
potentially
had
an
exploit
for
the
MOVEit
Transfer
vulnerability
prior
to
the GoAnywhere
MFT
secure
file
transfer
tool
exploitation that
took
place
in
February
2023.
Kroll
observed
exploitation
attempts
for
the
MOVEit
Transfer
vulnerability
on
or
around
May
27
and
28,
2023,
a
few
days
before
Progress
Software
publicly
disclosed
the
issue
on
May
31,
2023.
This
time
frame
coincided
with
the
observation
of
Memorial
Day
weekend
in
the
U.S.,
a
circumstance
that
suggests
that
threat
actors
planned
to
to
launch the
attacks
during
holiday
weekends.
Between
May
27
and
May
28,
the
experts
observed
an
automated
exploitation
attack
chain
aimed
at
the
deployment
of
the
human2.aspx
web
shell.
“Kroll’s
review
of
Microsoft
Internet
Information
Services
(IIS)
logs
of
impacted
clients
found
evidence
of
similar
activity
occurring
in
multiple
client
environments
last
year
(April
2022)
and
in
some
cases
as
early
as
July
2021.”
reads
the
analysis
published
by
the
security
firm.
“Kroll
observed
activity
consistent
with
MOVEit
Transfer
exploitation
that
collectively
occurred
on
April
27,
2022;
May
15–16,
2023;
and
May
22,
2023,
indicating
that
actors
were
testing
access
to
organizations
via
likely
automated
means
and
pulling
back
information
from
the
MOVEit
Transfer
servers
to
identify
which
organization
they
were
accessing.”
The
attackers
employed
an
automated
system
to
run
multiple
commands
against
the
organizations
in
less
than
24
seconds.

The
threat
actors
were
also
testing
how
to
collect
and
extract
sensitive
data
from
compromised
MOVEit
Transfer
servers
as
far
back
as
April
2022.
The
commands
sent
to
the
device
in
July
2021
appeared
to
be
run
over
a
longer
amount
of
time,
suggesting
that
attackers
were
using
a
manual
process.
“It
appears
that
the
Clop
threat
actors
may
have
been
experimenting
with
ways
to
exploit
the
MOVEit
Transfer
vulnerability
for
quite
some
time
prior
to
the
recent
mass
exfiltration
event.
Kroll
observed
a
similar
fact
pattern
across
multiple
MOVEit
Transfer
cases,
and
in
some
instances,
the
activity
occurred
across
multiple
organizations
within
seconds
or
minutes
of
each
other.”
concludes
Kroll.
“Kroll
assesses
with
high
confidence
that
the
MOVEit
Transfer
exploit
as
it
exists
today:
-
Was
available
and
being
used/tested
in
April
2022 -
Was
available
and
being
used/tested
in
July
2021″
This
week,
the
Clop
ransomware
group
claimed
to
have
compromised
hundreds
of
companies
worldwide
by
exploiting
a
vulnerability
in MOVEit
Transfer software.
Over
the
weekend,
the Clop
ransomware gang
(aka Lace
Tempest)
was
credited
by
Microsoft
for
the
recent
campaign
that
exploits
a
zero-day
vulnerability,
tracked
as CVE-2023-34362,
in
the MOVEit
Transfer platform.
On
Wednesday,
the
Clop
ransomware
gang
published
an
extortion
note
on
its
dark
web
leak
site
claiming
to
have
information
on
hundreds
of
businesses.
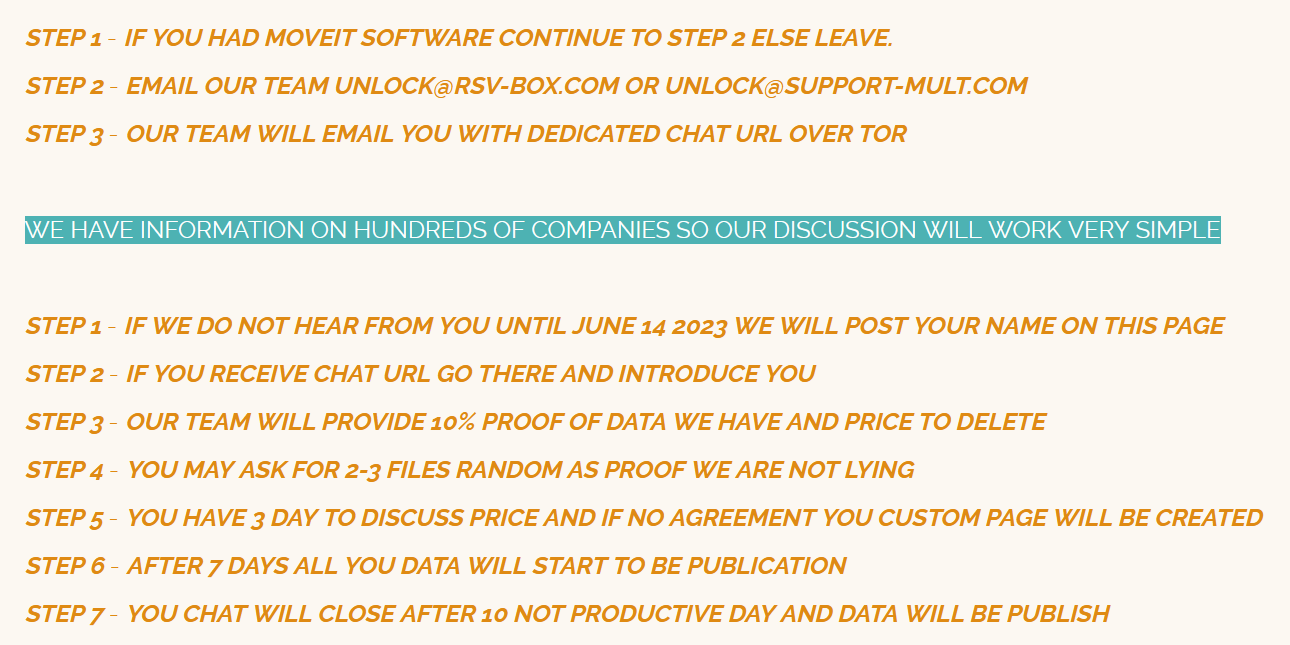
“WE
HAVE
INFORMATION
ON
HUNDREDS
OF
COMPANIES
SO
OUR
DISCUSSION
WILL
WORK
VERY
SIMPLE.”
reads
the
message
published
by
the
gang.

The
gang
is
urging
victim
organizations
to
contact
them
before
their
name
will
be
added
to
the
list
of
victims
on
the
leak
site.
The
group
has
fixed
the
deadline
on
June
14.
At
this
time
it
not
possible
to
determine
the
exact
number
of
organizations
that
were
breached
by
the
gang
by
exploiting
the
MOVEit
Transfer
vulnerability.
By
May
31,
Rapid7
experts
discovered approximately
2,500
instances of
MOVEit
Transfer
publicly
accessible
on
the
internet,
with
a
significant
portion
located
in
the
United
States.
One
of
the
organizations
that
was
hacked
by
exploiting
the
above
issue
is
the
payroll
provider
Zellis.
The
bad
news
is
that
as
a
result
of
the
cyber
attack
on
the
payroll
provider
Zellis,
the
personal
data
of
employees
at
the
BBC
and
British
Airways has
been
compromised and
exposed.
One
of
Zellis’s
customers,
the
British
health
and
beauty
retailer
and pharmacy chain
Boots
also
confirmed
to
have
been
impacted
by
the
attack.
The
company
has
yet
to
determine
the
number
of
impacted
employees.
Another
impacted
firm
is
the
airline
Aer
Lingus,
which
confirmed
that
“some
of
our
current
and
former
employee
data”
has
been
disclosed.
This
isn’t
the
first
time
that Clop
ransomware gang
carry
out
hacking
campaign
on
a
large
scale
by
exploiting
a
zero-day
vulnerability.
In
February,
the
Clop
ransomware
group claimed to
have
stolen
sensitive
data
from
over
130
organizations
by
exploiting
a
zero-day
vulnerability
(CVE-2023-0669)
in
Fortra’s GoAnywhere
MFT secure
file
transfer
tool.
Follow
me
on
Twitter: @securityaffairs and Facebook and Mastodon
(SecurityAffairs – hacking, Clop
ransomware)







