Remote Desktop Protocol (RDP) was developed by Microsoft to allow users, administrators, and others to connect to remote computers over a network connection using a handy graphical user interface (GUI). The tools required for this come as standard on Microsoft Windows; to initiate and set up an RDP connection, all the tools required to do that are present by default. This is why RDP is used extensively throughout networks by users and administrators to access remote machines.
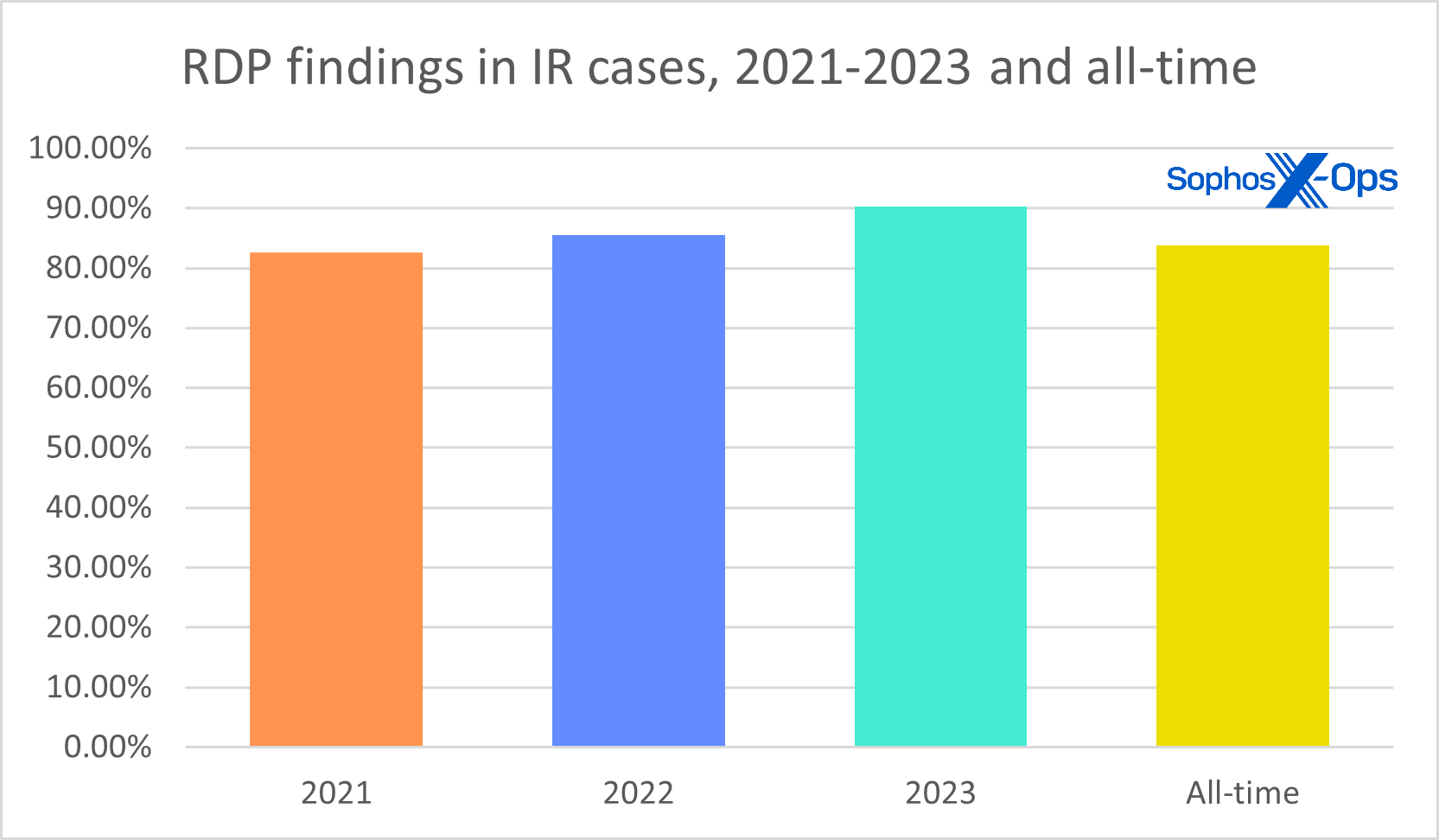
Unfortunately, it’s also commonly abused by ransomware groups – so commonly, in fact, that in our regular Active Adversary Reports our editors are forced to treat RDP differently in graphics so other findings are even visible. And RDP abuse is on the rise, as we see in Figure 1 — numbers from the past few years of incident-response data as collected by the Active Adversary Report team. In the edition of the report we’ll be releasing next month, you’ll see that RDP has now cracked the 90 percent mark – that is, nine out of ten IR cases include RDP abuse.
Figure 1: A first look at the full Active Adversary dataset from 2023 shows that RDP abuse is getting worse
Today, to provide context and advice for administrators and responders looking to deal with RDP, we’re publishing an entire package of resources – videos, companion articles with additional information, and a constellation of additional scripts and information on our GitHub repository. We’re doing this both to share our Active Adversary team’s research beyond the usual long-form reports we issue, and to provide what we hope is a useful set of resources for handling one of infosec’s more annoying chronic ailments.
From an attacker’s point of view, targeting RDP is a natural choice. Most significantly, it’s a Microsoft-provided tool (so, a living-off-the-land binary, or LOLBin) that blends in with typical user and administrative behavior. Its usage alone isn’t apt to draw attention if no one’s keeping an eye out for it, and an attacker need not bring in additional tools that may be detected by EDR or other anti-intrusion tools. RDP also has a relatively pleasant graphical user interface that lowers the skill barrier for attackers to browse files for exfiltration, and to install and use various applications.
Attackers also know that RDP is commonly misconfigured or misused within an environment, both on servers and occasionally on endpoints themselves. The next article in this RDP collection looks at just how common such exposure is, and whether measures such as switching off RDP’s usual 3389 port makes a difference. (Spoiler: No.)
Rounding out the dismal RDP picture, we see self-owns such as lack of segregation, use of weak credentials, disabling (by administrators) of potential protections such as NLA (network-level authentication), and flagrant disregard for best practices such as least privilege. On the brighter side, there are useful, sturdy queries that can give great insight into precisely how RDP is in use on your network… if you know where to look.
So, to provide context and advice for administrators and responders looking to deal with RDP, we’re starting with an entire package of resources – six videos, six companion articles with additional information, and a constellation of additional scripts and information on our GitHub – with more to be added over time as events dictate.
Remote Desktop Protocol: The Series
Part 1: Remote Desktop Protocol: Introduction ([you are here], video)
Part 2: Remote Desktop Protocol: Exposed RDP (is dangerous) (post, video)
Part 3: RDP: Queries for Investigation (post, video)
Part 4: RDP Time Zone Bias (post, video)
Part 5: Executing the External RDP Query (post, video)
Part 6: Executing the 4624_4625 Login Query (post, video)
GitHub query repository: SophosRapidResponse/OSQuery
Transcript repository: sophoslabs/video-transcripts
YouTube playlist: Remote Desktop Protocol: The Series