RansomHub procedure is a revamped version of the Knight RaaS

Experts opine that the RansomHub ransomware-as-a-service is an updated version of the Knight ransomware operation.
Those in the cybersecurity field who scrutinized the recently revealed ransomware operation RansomHub suspect it has undergone a rebranding from the Knight ransomware.
Initially spotted in May 2023, Knight, also referred to as Cyclops 2.0, targeted various platforms, such as Windows, Linux, macOS, ESXi, and Android. The perpetrators employed a dual extortion model for their RaaS endeavor.
The Knight ransomware-as-a-service operation ceased in February 2024, and it seems that the source code of the malware was possibly sold to the party that relaunched the RansomHub operation. RansomHub has admitted responsibility for breaching multiple entities, including Change Healthcare, Christie’s, and Frontier Communications.
Analysts at Symantec, a division of Broadcom, identified numerous resemblances between the RansomHub and Knight ransomware lineages, pointing towards a shared ancestry:
- Both are coded in Go and leverage Gobfuscate for concealing.
- They exhibit significant code similarities.
- The command-line guides used by the two malicious programs are almost identical, barring a ‘sleep’ command on RansomHub.
- Both employ a unique obfuscation tactic involving uniquely encoded essential strings.
- The ransom demands from both Knight and RansomHub demonstrate notable similarities, with numerous phrases from Knight’s demand being verbatim in RansomHub’s, implying that the developers likely revised and upgraded the original notice.
- Both malware restart endpoints in safe mode before encryption.
- The sequence and execution methodology of commands align, although RansomHub now uses cmd.exe for execution.
Nonetheless, despite the common origins of the two malware strains, it is improbable that the designers of Knight are now managing RansomHub.
“One primary distinction between the two ransomware strains is the commands executed via cmd.exe. Even though the specific commands might differ, they can be configured either during payload construction or through setup. Despite variations in commands, the sequence and methodology of execution relative to other operations remain consistent.” as stated in the report issued by Symantec.
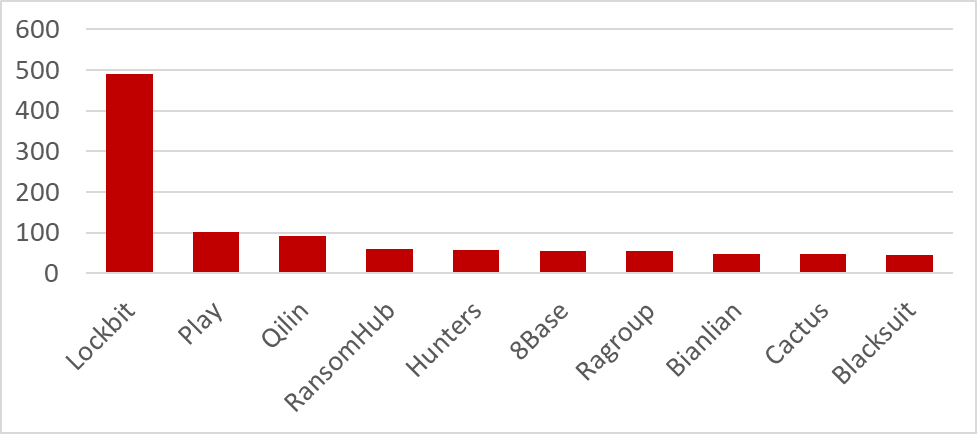
Despite only surfacing in February 2024, RansomHub has expanded swiftly and, in the last three months, has risen to become the fourth most active ransomware entity based on the number of openly claimed attacks.

“RansomHub’s rapid growth might be attributed to the group’s success in luring some significant former affiliates of the Noberus (aka ALPHV, Blackcat) ransomware gang, which disbanded earlier this year. One former Noberus affiliate named Notchy is allegedly collaborating with RansomHub now. Furthermore, tools previously associated with another Noberus affiliate identified as Scattered Spider, were employed in a recent RansomHub breach.” concludes the analysis, which also furnishes Indicators of Compromise. “The rapid establishment of RansomHub’s business indicates that the group may consist of veteran operators with experience and connections within the cyber underworld.”
Connect with me on Twitter: @securityaffairs and Facebook and Mastodon
(SecurityAffairs – hacking, ransomware)










