Pwn2Own Vancouver 2024 Day 1 – team Synacktiv hacked a Tesla

Participants earned $732,500 on the first day of the Pwn2Own Vancouver 2024 hacking competition, a team demonstrated a Tesla hack.
Participants earned $732,000 on the first day of the Pwn2Own Vancouver 2024 hacking competition for demonstrating 19 unique zero-days, announced Trend Micro’s Zero Day Initiative (ZDI). The experts successfully demonstrated exploits against a Tesla car, Linux and Windows operating systems, and more.
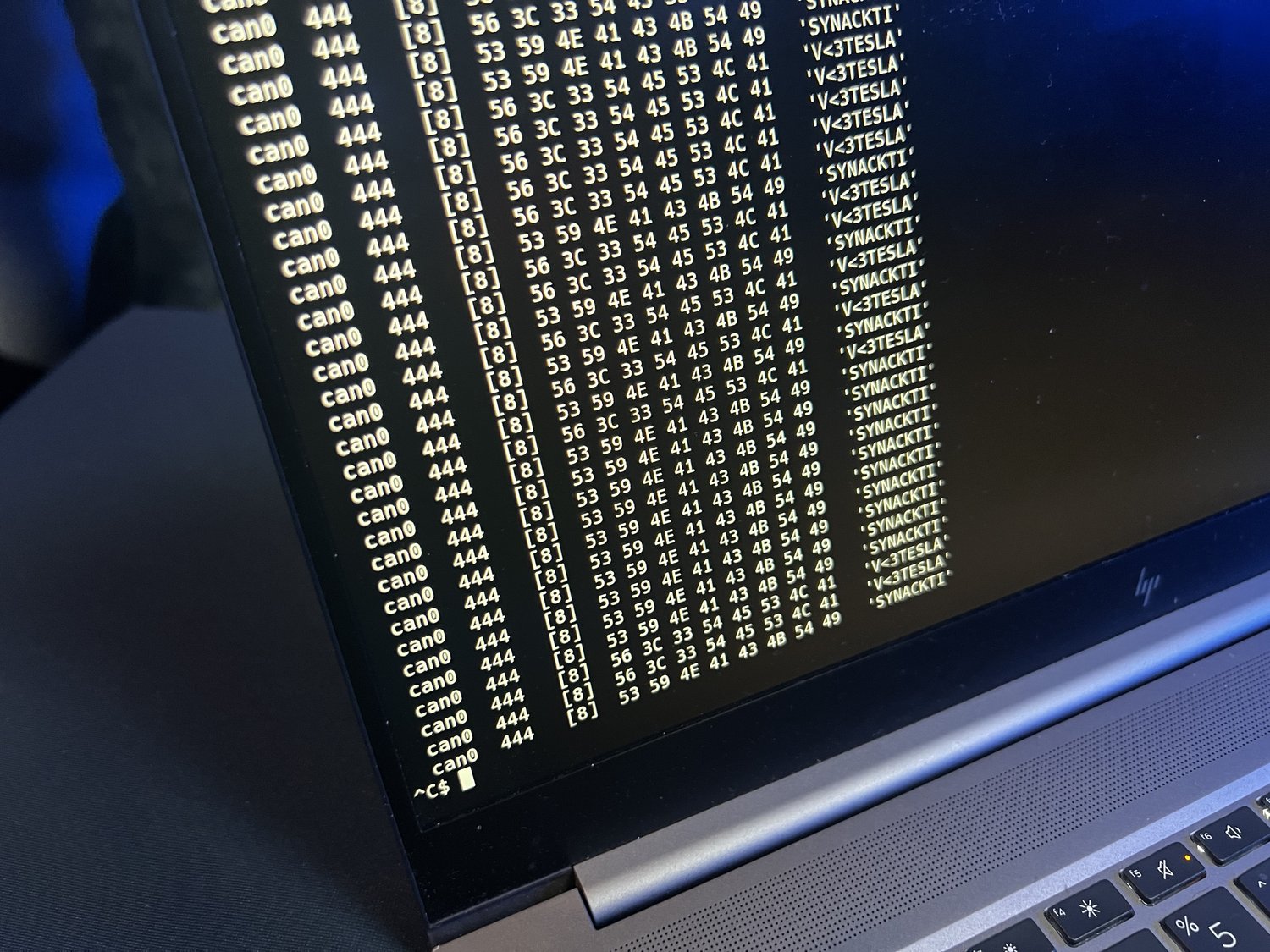
The team Synacktiv earned $200,000 for demonstrating an integer overflow exploit against a Tesla car, the experts targeted the electronic control unit (ECU) with CAN bus control. The team also won a new Tesla Model 3.

In past editions of the hacking competition, the same team already demonstrated exploits against Tesla. In January the Synacktiv Team (@Synacktiv) compromised the Tesla infotainment system on the second day of the Pwn2Own Automotive 2024 hacking competition. The bug hunters chained two vulnerabilities to hack the Tesla infotainment system, they earned $100,000 and 10 Master of Pwn Points.
The researchers Gwangun Jung (@pr0ln) and Junoh Lee (@bbbig12) from cyber security firm Theori (@theori_io) chained an uninitiallized variable bug, a UAF, and a heap-based buffer overflow to achieve a VMware Workstation escape and execute code as SYSTEM on the host Windows OS. The team earned $130,000 and won 13 Master of Pwn points.
The researcher Manfred Paul (@_manfp) chained an integer underflow bug and a PAC bypass in Apple Safari to achive remote code execution on the popular browser. He earned $60,000 and 6 Master of Pwn points.
Bruno PUJOS and Corentin BAYET from software reverse engineering & vulnerability discovery company REverse Tactics (@Reverse_Tactics) chained a buffer overflow and a Windows UAF bypass in Oracle VirtualBox to escape the guest OS and execute code as SYSTEM on the host OS. The team earned $90,000 and 9 Master of Pwn points.
The complete list of results for the first day of the Pwn2Own Vancouver 2024 hacking competition is available here:
https://www.zerodayinitiative.com/blog/2024/3/20/pwn2own-vancouver-2024-day-one-results
Follow me on Twitter: @securityaffairs and Facebook and Mastodon
(SecurityAffairs – hacking, Pwn2Own Vancouver 2024)