PureCrypter Malware Targets Government Entities in Asia-Pacific and North America

Government
entities
in
Asia-Pacific
and
North
America
are
being
targeted
by
an
unknown
threat
actor
with
an
off-the-shelf
malware
downloader
known
as
PureCrypter
to
deliver
an
array
of
information
stealers
and
ransomware.
“The
PureCrypter
campaign
uses
the
domain
of
a
compromised
non-profit
organization
as
a
command-and-control
(C2)
to
deliver
a
secondary
payload,”
Menlo
Security
researcher
Abhay
Yadav
said.
The
different
types
of
malware
propagated
using
PureCrypter
include
RedLine
Stealer,
Agent
Tesla,
Eternity,
Blackmoon
(aka
KRBanker),
and
Philadelphia
ransomware.
First
documented
in
June
2022,
PureCrypter
is
advertised
for
sale
by
its
author
for
$59
for
one-month
access
(or
$245
for
a
one-off
lifetime
purchase)
and
is
capable
of
distributing
a
multitude
of
malware.
In
December
2022,
PureCoder
–
the
developer
behind
the
program
–
expanded
the
slate
of
offerings
to
include
a
logger
and
information
stealer
known
as
PureLogs,
which
is
designed
to
siphon
data
from
web
browsers,
crypto
wallets,
and
email
clients.
It
costs
$99
a
year
(or
$199
for
lifetime
access).
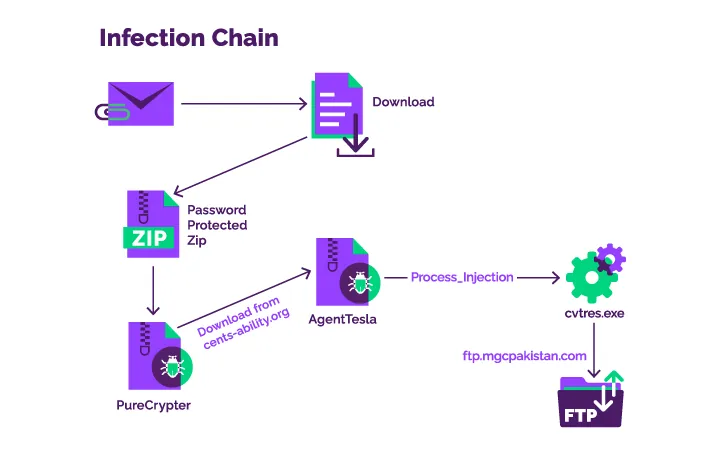
The
infection
sequence
detailed
by
Menlo
Security
commences
with
a
phishing
email
containing
a
Discord
URL
that
points
to
the
first-stage
component,
a
password-protected
ZIP
archive
that,
in
turn,
loads
the
PureCrypter
malware.
The
loader,
for
its
part,
reaches
out
to
the
website
of
the
breached
non-profit
entity
to
fetch
the
secondary
payload,
which
is
a
.NET-based
keylogger
named
Agent
Tesla.
The
backdoor
then
establishes
a
connection
to
an
FTP
server
located
in
Pakistan
to
exfiltrate
the
harvested
data,
indicating
that
compromised
credentials
may
have
been
used
to
perform
the
activity.