PlugX Trojan Disguised as Legitimate Windows Debugger Tool in Latest Attacks
The
PlugX
remote
access
trojan
has
been
observed
masquerading
as
an
open
source
Windows
debugger
tool
called
x64dbg
in
an
attempt
to
circumvent
security
protections
and
gain
control
of
a
target
system.
“This
file
is
a
legitimate
open-source
debugger
tool
for
Windows
that
is
generally
used
to
examine
kernel-mode
and
user-mode
code,
crash
dumps,
or
CPU
registers,”
Trend
Micro
researchers
Buddy
Tancio,
Jed
Valderama,
and
Catherine
Loveria
said
in
a
report
published
last
week.
PlugX,
also
known
as
Korplug,
is
a
post-exploitation
modular
implant,
which,
among
other
things,
is
known
for
its
multiple
functionalities
such
as
data
exfiltration
and
its
ability
to
use
the
compromised
machine
for
nefarious
purposes.
Although
first
documented
a
decade
ago
in
2012,
early
samples
of
the
malware
date
as
far
as
February
2008,
according
to
a
Trend
Micro
report
at
the
time.
Over
the
years,
PlugX
has
been
used
by
threat
actors
with
a
Chinese
nexus
as
well
as
cybercrime
groups.
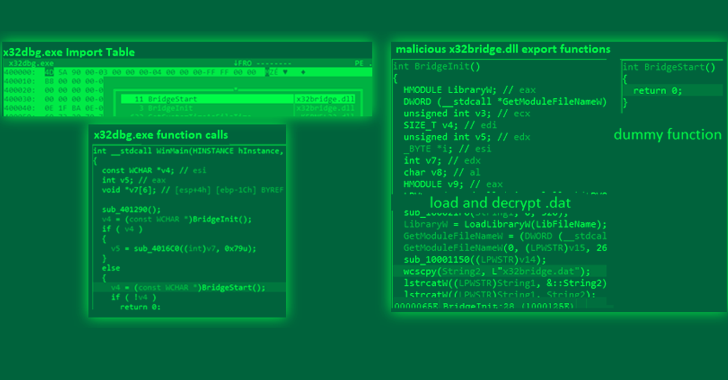
One
of
the
key
methods
the
malware
employs
is
a
technique
DLL
side-loading
to
load
a
malicious
DLL
from
a
digitally
signed
software
application,
in
this
case
the
x64dbg
debugging
tool
(x32dbg.exe).
It’s
worth
noting
here
that
DLL
side-loading
attacks
leverage
the
DLL
search
order
mechanism
in
Windows
to
plant
and
then
invoke
a
legitimate
application
that
executes
a
rogue
payload.
“Being
a
legitimate
application,
x32dbg.exe’s
valid
digital
signature
can
confuse
some
security
tools,
enabling
threat
actors
to
fly
under
the
radar,
maintain
persistence,
escalate
privileges,
and
bypass
file
execution
restrictions,”
the
researchers
said.
The
hijacking
of
x64dbg
to
load
PlugX
was
disclosed
last
month
by
Palo
Alto
Networks
Unit
42,
which
discovered
a
new
variant
of
the
malware
that
hides
malicious
files
on
removable
USB
devices
to
propagate
the
infection
to
other
Windows
hosts.
Persistence
is
achieved
via
Windows
Registry
modifications
and
the
creation
of
scheduled
tasks
to
ensure
continued
access
even
after
system
restarts.
Trend
Micro’s
analysis
of
the
attack
chain
also
revealed
the
use
of
x32dbg.exe
to
deploy
a
backdoor,
a
UDP
shell
client
that
collects
system
information
and
awaits
additional
instructions
from
a
remote
server.
“Despite
advances
in
security
technology,
attackers
continue
to
use
[DLL
side-loading]
since
it
exploits
a
fundamental
trust
in
legitimate
applications,”
the
researchers
said.
“This
technique
will
remain
viable
for
attackers
to
deliver
malware
and
gain
access
to
sensitive
information
as
long
as
systems
and
applications
continue
to
trust
and
load
dynamic
libraries.”