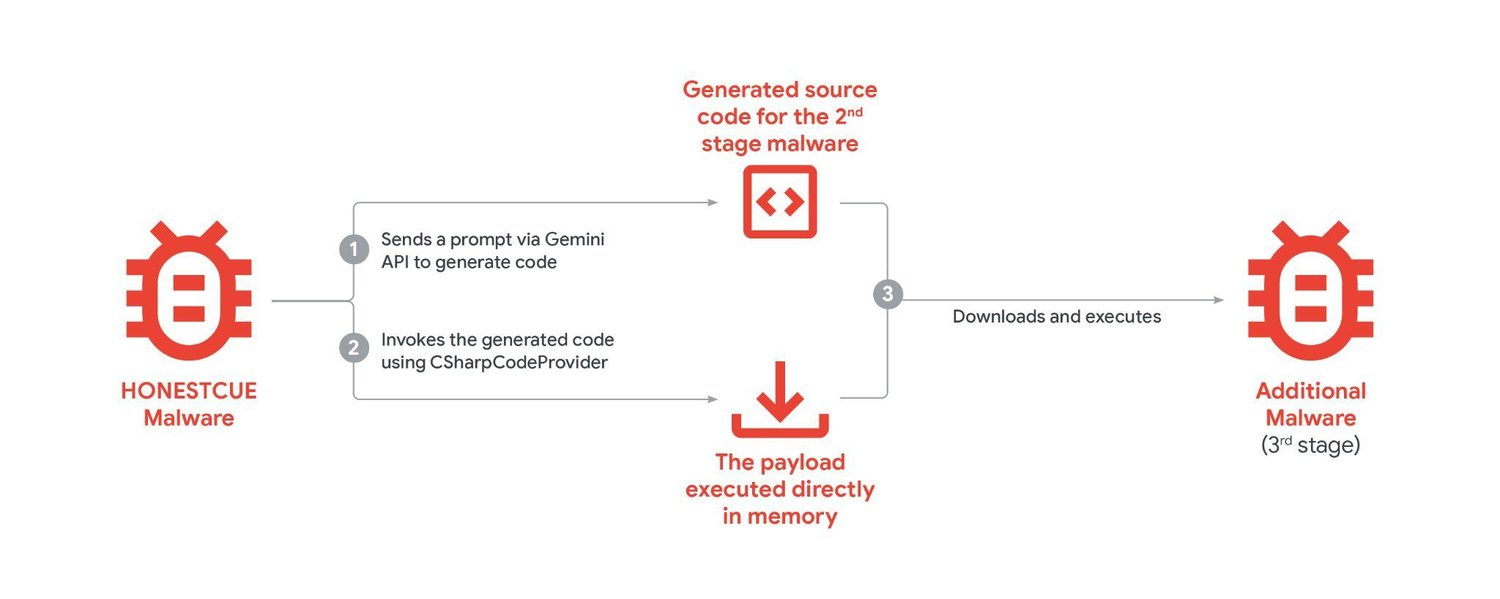
Post‑Quantum Authentication: How Consumer Apps Can Stay Secure in a Quantum‑Ready World?
Quantum is not so distant in the present scenario. That is the uncomfortable truth. In fact, large‑scale quantum machines could unpick the math that props up today’s logins and sessions.
Post‑Quantum Authentication: How Consumer Apps Can Stay Secure in a Quantum‑Ready World?
Quantum is not so distant in the present scenario. That is the uncomfortable truth. In fact, large‑scale quantum machines could unpick the math that props up today’s logins and sessions.
Also, standards bodies have moved first, and industry chatter around quantum‑resistant primitives is no longer niche. It is front‑row, with transition guidance urging teams to start now rather than later.
The market signal is clear. It says that post‑quantum algorithms have crossed from research into formal specifications. NIST finalized core standards and is building a backup bench so nobody is tied to a single math family.
Security leaders read this as permission to begin staged migrations. Procurement reads it as a requirement. The cost of waiting becomes technical debt that piles up quietly.
Why Does Traditional Cryptography Become Vulnerable?
Classical public‑key crypto relies on problems such as factoring and discrete logarithms. They are useful because they are hard for normal computers. A capable quantum computer flips the difficulty table.
Shor’s Algorithm turns what used to be infeasible into polynomial‑time work. That breaks the assumptions under RSA and many elliptic curve schemes that protect keys, handshakes, and signatures on the web.
Risks for Consumer Applications
Consumer platforms live on trust and speed. Fintech flows rely on strong session keys and signatures. Meanwhile, messaging apps need authenticated device bindings. IoT stacks push updates that must stay tamper-evident.
If the crypto layer collapses later, data harvested today can be decrypted then. That harvest‑now‑decrypt‑later angle turns long‑lived secrets and archived traffic into soft targets. Essentially, teams cannot roll that back once exposed.
What Does Post‑Quantum Authentication Involve?
Post‑quantum cryptography swaps vulnerable math for constructions designed to resist quantum attacks.
Lattices
Hash‑based signatures
Code‑based schemes.
In authentication, these primitives protect the same checkpoints we already know. These include credential creation, assertion signing, and key establishment for TLS and WebAuthn backends. The workflow can look familiar while the crypto under the hood changes. That is helpful for lower migration friction.
Current Standards and Industry Momentum
NIST has published three principal standards that are ready for use.
ML‑KEM for key establishment
ML‑DSA and SLH‑DSA for signatures.
Also, a backup KEM, HQC, has been selected to diversify risk. Hence, you must start inventory, plan the cutover, and phase out vulnerable algorithms on a timeline rather than in a fire drill. It is a managed transition with public guidance.
Nicegram comes up in conversations about consumer messaging and identity because communities move fast and expect simple, secure logins without security theater.
The takeaway is not about a single brand, but a pattern. Users carry credentials across devices. They expect a recovery that does not feel like a maze. Post‑quantum plans must keep that feel while swapping the cryptography underneath.
Integrating Quantum‑Resistant Methods Into Authentication
It is possible to integrate quantum-resistant methods into authentication for better security. This is possible through multiple ways:
1. Hybrid Security Models
Most teams will not flip a switch, but will run hybrids. Classical plus post‑quantum in the same handshake or signature flow. If one side fails in the future, the other holds. This is already visible in standards work and vendor experiments.
The pattern keeps compatibility during rollout while cutting future risk. It buys time without kicking the can down the road.
2. Impact on Passwordless Systems and Passkeys
Passwordless is not excluded here. In fact, passkeys and FIDO2 (Fast IDentity Online 2) rely on signature algorithms and protocol identifiers that are evolving to support PQC (Post-Quantum Cryptography) options.
The standards ecosystem has begun registering post‑quantum algorithms so authenticators and servers can negotiate them. Guidance is aligning with assurance levels, clarifying when synced or device‑bound passkeys meet stronger requirements. Basically, the net effect is momentum.
The following are the implementation focus points:
Map where authenticator attestation and assertion signatures are verified, then test PQC support in those components.
Pilot hybrid credentials in low‑risk cohorts before broad rollout to consumer traffic.
Challenges and Considerations
Post-quantum authentication comes with a few challenges. Hence, it is important to consider the following factors:
1. Performance and Compatibility Issues
New algorithms are bigger, keys get heavier, and signatures grow. That affects network payloads, database storage, and cold‑start paths.
Meanwhile, mobile clients care about compute and battery. Also, edge devices care about flash and RAM. The engineering answer is not to delay. It is to benchmark representative journeys with PQC in place and tune. NIST notes migration will require updates across products, protocols, and inventories.
2. Adoption Barriers for Consumer Apps
Ecosystem fragmentation slows change. For instance, browsers and OSes roll out support on staggered schedules. SDKs hide details, but not always quickly. Security policies chase fast-moving standards.
Even so, assurance guidance around passkeys has matured, pushing synced variants toward AAL2 and device‑bound toward AAL3 when implemented as specified. That clarity helps regulated teams move without second‑guessing.
Classical vs Post‑Quantum Considerations
Dimension
Classical Public‑Key (RSA, ECC)
Post‑Quantum Approaches (ML‑KEM, ML‑DSA, SLH‑DSA, HQC)
Security premise
Hardness of factoring and discrete logs
Lattices, hash‑based, or code‑based hardness assumptions
Quantum exposure
Broken in polynomial time by Shor’s Algorithm if a large quantum computer arrives
Designed to resist known quantum attacks per the NIST selection process
Key and signature sizes
Smaller and mature
Larger on average, impacts bandwidth and storage
Standardization status
Longstanding FIPS and IETF use
Finalized core FIPS in 2024, backup KEM selection in 2025
Migration path
Legacy installed base is broad
Inventory, hybrid rollout, phased deprecation plan
Authentication Is Uncompromisable!
The window for pretending this authentication requirement is far away has closed. In fact, the work is straightforward. Inventory where public‑key crypto lives.
So, decide where to start, add PQC in a hybrid form, and measure the hit on size and latency. Also, make sure the platform support is mature. Then, rinse and improve. The goal is dull reliability, and users should not notice. Rather, they should only feel that sign‑in still works and stays safe.
*** This is a Security Bloggers Network syndicated blog from MojoAuth – Advanced Authentication & Identity Solutions authored by MojoAuth – Advanced Authentication & Identity Solutions. Read the original post at: https://mojoauth.com/blog/post-quantum-authentication-consumer-app-security