Recently
emerged
HardBit
ransomware
gang
adjusts
their
demands
so
the
insurance
company
would
cover
the
ransom
cost.
The
HardBit
ransomware
group
first
appeared
on
the
threat
landscape
in
October
2022,
but
unlike
other
ransomware
operations,
it
doesn’t
use
a
double
extortion
model
at
this
time.
The
gang
threatens
victims
of
further
attacks
if
their
ransom
demands
are
not
met.
Once
infected
the
network
of
an
organization,
the
HardBit
ransomware
group
instructs
victims
to
contact
them
by
email
or
via
the
Tox
instant
messaging
platform.
The
group
made
the
headline
because
it
seeks
to
negotiate
with
victims
to
reach
a
settlement.
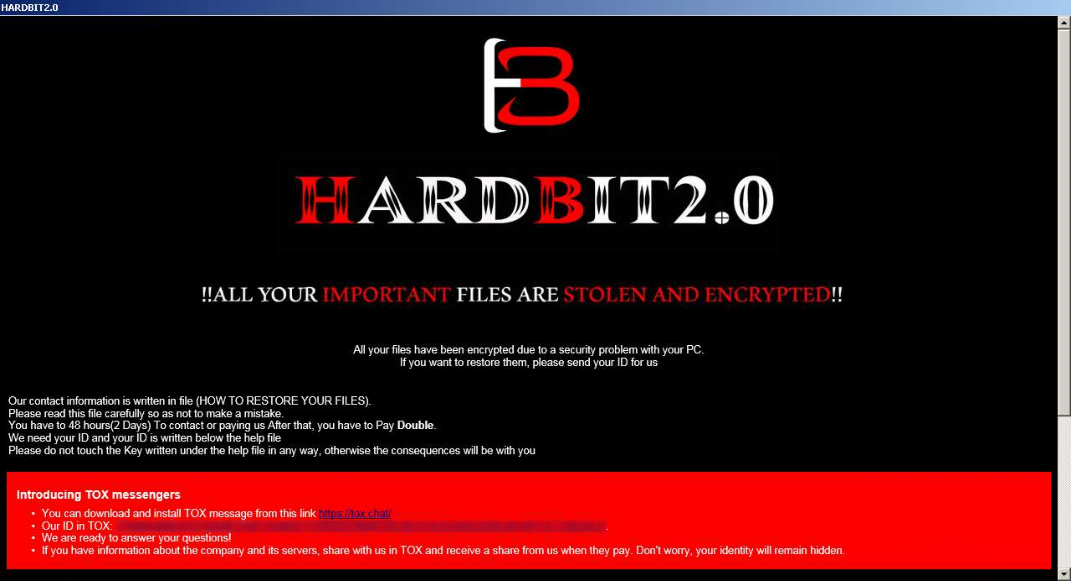
"Very important! For those who have cyber insurance against ransomware attacks. Insurance companies require you to keep your insurance information secret, this is to never pay the maximum amount specified in the contract or to pay nothing at all, disrupting negotiations. The insurance company will try to derail negotiations in any way they can so that they can later argue that you will be denied coverage because your insurance does not cover the ransom amount. For example your company is insured for 10 million dollars, while negotiating with your insurance agent about the ransom he will offer us the lowest possible amount, for example 100 thousand dollars, we will refuse the paltry amount and ask for example the amount of 15 million dollars, the insurance agent will never offer us the top threshold of your insurance of 10 million dollars. He will do anything to derail negotiations and refuse to pay us out completely and leave you alone with your problem. If you told us anonymously that your company was insured for $10 million and other important details regarding insurance coverage, we would not demand more than $10 million in correspondence with the insurance agent. That way you would have avoided a leak and decrypted your information. But since the sneaky insurance agent purposely negotiates so as not to pay for the insurance claim, only the insurance company wins in this situation. To avoid all this and get the money on the insurance, be sure to inform us anonymously about the availability and terms of insurance coverage, it benefits both you and us, but it does not benefit the insurance company. Poor multimillionaire insurers will not starve and will not become poorer from the payment of the maximum amount specified in the contract, because everyone knows that the contract is more expensive than money, so let them fulfill the conditions prescribed in your insurance contract, thanks to our interaction." reads the ransom note.
It
requests
the
victims
to
share
details
of
their
cyber
insurance
policies
so
that
the
cost
of
the
ransom
can
be
completely
covered
by
the
insurer
company.
By
revealing
the
exact
insurance
amount
to
the
ransomware
group,
crooks
can
prevent
the
insurance
company
should
negotiate
lower
ransom
payments.
Clearly,
clients
of
insurers
are
contractually
obliged
not
to
disclose
this
amount
to
the
ransomware
gangs.
“Rather
than
specifying
an
amount
of
bitcoin
requested
within
this
ransom
note,
the
group
seeks
to
negotiate
with
victims
to
reach
a
settlement.
Notably,
as
part
of
these
negotiations,
victims
with
cyber
insurance
policies
are
also
encouraged
to
share
details
with
HardBit
so
that
their
demands
can
be
adjusted
to
fall
within
the
policy.”
reads
the
post
published
by
Varonis.
In
order
to
make
it
impossible
for
the
victims
to
recover
the
encrypted
files,
the
ransomware
deletes
the
Volume
Shadow
Copy
Service
(VSS)
using
the
Service
Control
Manager
and
the
Windows
backup
utility
catalog
along
with
any
shadow
copies.
The
researchers
noticed
that
the
malware
encrypts
many
files,
potentially
causing
errors
when
Windows
is
restarted.
To
avoid
problems
at
the
successive
startup,
the
malware
edits
the
boot
configuration
to
enable
the
“ignore
any
failures”
option
and
disable
the
recovery
option.
To
prevent
Windows
Defender
Antivirus
from
blocking
the
ransomware
process,
it
makes
several
Windows
Registry
changes
to
disable
many
Windows
Defender
features
(i.e.
tamper
protection,
anti-spyware
capabilities,
real-time
behavioral
monitoring,
real-time
on-access
(file)
protection,
and
real-time
process
scanning).
The
ransomware
achieves
persistence
by
copying
a
version
to
the
victim’s
“Startup”
folder,
if
not
already
present.
The
executable
filename
mimics
the
legitimate
service
host
executable
file,
svchost.exe,
to
avoid
detection.
The
report
from
Varonis also
includes
indicators
of
compromise
(IoCs)
that
help
detect
the
malware.
Follow
me
on
Twitter:
@securityaffairs
and
Facebook
and
Mastodon
(SecurityAffairs –
hacking,
HardBit
ransomware)