Telecommunication
providers
in
the
Middle
East
are
the
subject
of
new
cyber
attacks
that
commenced
in
the
first
quarter
of
2023.
The
intrusion
set
has
been
attributed
to
a
Chinese
cyber
espionage
actor
associated
with
a
long-running
campaign
dubbed
Operation
Soft
Cell
based
on
tooling
overlaps.
“The
initial
attack
phase
involves
infiltrating
Internet-facing
Microsoft
Exchange
servers
to
deploy
web
shells
used
for
command
execution,”
researchers
from
SentinelOne
and
QGroup
said
in
a
new
technical
report
shared
with
The
Hacker
News.
“Once
a
foothold
is
established,
the
attackers
conduct
a
variety
of
reconnaissance,
credential
theft,
lateral
movement,
and
data
exfiltration
activities.”
Operation
Soft
Cell,
according
to
Cybereason,
refers
to
malicious
activities
undertaken
by
China-affiliated
actors
targeting
telecommunications
providers
since
at
least
2012.
The
Soft
Cell
threat
actor,
also
tracked
by
Microsoft
as
Gallium,
is
known
to
target
unpatched
internet-facing
services
and
use
tools
like
Mimikatz
to
obtain
credentials
that
allows
for
lateral
movement
across
the
targeted
networks.
Also
put
to
use
by
the
adversarial
collective
is
a
“difficult-to-detect”
backdoor
codenamed
PingPull
in
its
espionage
attacks
directed
against
companies
operating
in
Southeast
Asia,
Europe,
Africa,
and
the
Middle
East.
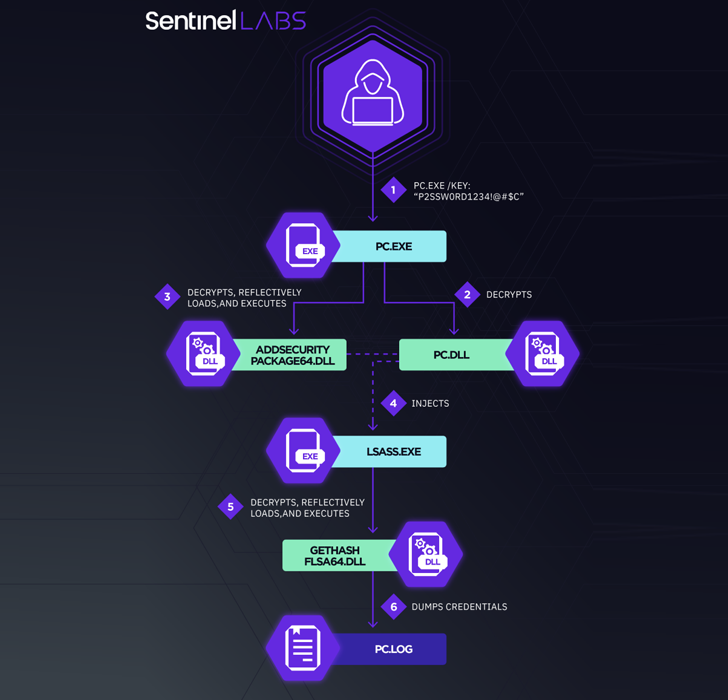
Central
to
the
latest
campaign
is
the
deployment
of
a
custom
variant
of
Mimikatz
referred
to
as
mim221,
which
packs
in
new
anti-detection
features.
“The
use
of
special-purpose
modules
that
implement
a
range
of
advanced
techniques
shows
the
threat
actors’
dedication
to
advancing
its
toolset
towards
maximum
stealth,”
the
researchers
said,
adding
it
“highlights
the
continuous
maintenance
and
further
development
of
the
Chinese
espionage
malware
arsenal.”
The
attacks
ultimately
proved
to
be
unsuccessful,
with
the
breaches
detected
and
blocked
before
any
implants
could
be
deployed
on
the
target
networks.
Prior
research
into
Gallium
suggests
tactical
similarities
[PDF]
with
multiple
Chinese
nation-state
groups
such
as
APT10
(aka
Bronze
Riverside,
Potassium,
or
Stone
Panda),
APT27
(aka
Bronze
Union,
Emissary
Panda,
or
Lucky
Mouse),
and
APT41
(aka
Barium,
Bronze
Atlas,
or
Wicked
Panda).
WEBINAR
Discover
the
Hidden
Dangers
of
Third-Party
SaaS
Apps
Are
you
aware
of
the
risks
associated
with
third-party
app
access
to
your
company’s
SaaS
apps?
Join
our
webinar
to
learn
about
the
types
of
permissions
being
granted
and
how
to
minimize
risk.
This
once
again
points
to
signs
of
closed-source
tool-sharing
between
Chinese
state-sponsored
threat
actors,
not
to
mention
the
possibility
of
a
“digital
quartermaster”
responsible
for
maintaining
and
distributing
the
toolset.
The
findings
come
amid
revelations
that
various
other
hacking
groups,
including
BackdoorDiplomacy
and
WIP26,
have
set
their
sights
on
telecom
service
providers
in
the
Middle
East
region.
“Chinese
cyber
espionage
threat
actors
are
known
to
have
a
strategic
interest
in
the
Middle
East,”
the
researchers
concluded.
“These
threat
actors
will
almost
certainly
continue
exploring
and
upgrading
their
tools
with
new
techniques
for
evading
detection,
including
integrating
and
modifying
publicly
available
code.”