German and South Korean Agencies Warn of Kimsuky’s Expanding Cyber Attack Tactics
German
and
South
Korean
government
agencies
have
warned
about
cyber
attacks
mounted
by
a
threat
actor
tracked
as
Kimsuky
using
rogue
browser
extensions
to
steal
users’
Gmail
inboxes.
The
joint
advisory
comes
from
Germany’s
domestic
intelligence
apparatus,
the
Federal
Office
for
the
Protection
of
the
Constitution
(BfV),
and
South
Korea’s
National
Intelligence
Service
of
the
Republic
of
Korea
(NIS).
The
intrusions
are
designed
to
strike
“experts
on
the
Korean
Peninsula
and
North
Korea
issues”
through
spear-phishing
campaigns,
the
agencies
noted.
Kimsuky,
also
known
Black
Banshee,
Thallium,
and
Velvet
Chollima,
refers
to
a
subordinate
element
within
North
Korea’s
Reconnaissance
General
Bureau
and
is
known
to
“collect
strategic
intelligence
on
geopolitical
events
and
negotiations
affecting
the
DPRK’s
interests.”
Primary
targets
of
interest
include
entities
in
the
U.S.
and
South
Korea,
particularly
singling
out
individuals
working
within
the
government,
military,
manufacturing,
academic,
and
think
tank
organizations.
“This
threat
actor’s
activities
include
collecting
financial,
personal,
and
client
data
specifically
from
academic,
manufacturing,
and
national
security
industries
in
South
Korea,”
Google-owned
threat
intelligence
firm
Mandiant
disclosed
last
year.
Recent
attacks
orchestrated
by
the
group
suggest
an
expansion
of
its
cyber
activity
to
encompass
Android
malware
strains
such
as
FastFire,
FastSpy,
FastViewer,
and
RambleOn.
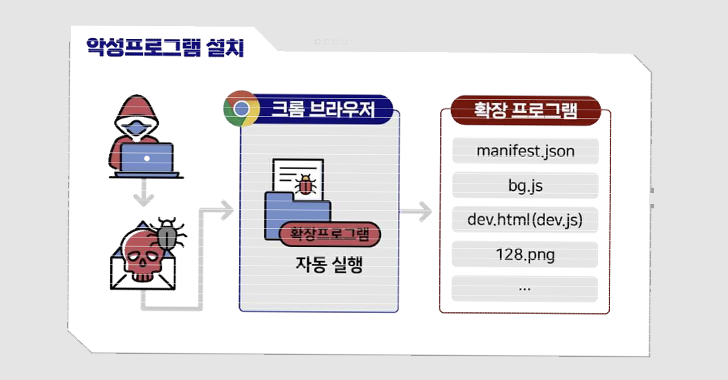
The
use
of
Chromium-based
browser
extensions
for
cyber
espionage
purposes
is
not
new
for
Kimsuky,
which
has
previously
used
similar
techniques
as
part
of
campaigns
tracked
as
Stolen
Pencil
and
SharpTongue.
The
SharpTongue
operation
also
overlaps
with
the
latest
effort
in
that
the
latter
is
also
capable
of
stealing
a
victim’s
email
content
using
the
rogue
add-on,
which,
in
turn,
leverages
the
browser’s
DevTools
API
to
perform
the
function.
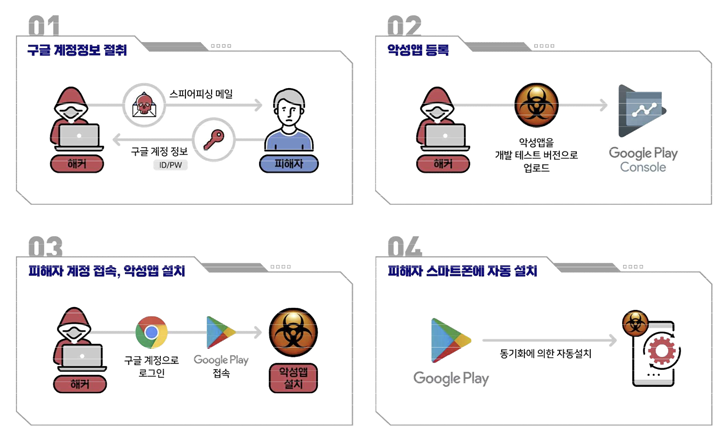
But
in
an
escalation
of
Kimsuky’s
mobile
attacks,
the
threat
actor
has
been
observed
logging
into
victims’
Google
accounts
using
credentials
already
obtained
in
advance
through
phishing
tactics
and
then
installing
a
malicious
app
on
the
devices
linked
to
the
accounts.
“The
attacker
logs
in
with
the
victim’s
Google
account
on
the
PC,
accesses
the
Google
Play
Store,
and
requests
the
installation
of
a
malicious
app,”
the
agencies
explained.
“At
this
time,
the
target’s
smartphone
linked
with
the
Google
account
is
selected
as
the
device
to
install
the
malicious
app
on.”
It’s
suspected
that
the
apps,
which
embed
FastFire
and
FastViewer,
are
distributed
using
a
Google
Play
feature
known
as
“internal
testing”
that
allows
third-party
developers
to
distribute
their
apps
to
a
“small
set
of
trusted
testers.”
WEBINAR
Discover
the
Hidden
Dangers
of
Third-Party
SaaS
Apps
Are
you
aware
of
the
risks
associated
with
third-party
app
access
to
your
company’s
SaaS
apps?
Join
our
webinar
to
learn
about
the
types
of
permissions
being
granted
and
how
to
minimize
risk.
A
point
worth
mentioning
here
is
that
these
internal
app
tests,
which
are
carried
out
prior
to
releasing
the
app
to
production,
cannot
exceed
100
users
per
app,
indicating
that
the
campaign
is
extremely
targeted
in
nature.
Both
the
malware-laced
apps
come
with
capabilities
to
harvest
a
wide
range
of
sensitive
information
by
abusing
Android’s
accessibility
services.
The
apps’
APK
package
names
are
listed
below
–
-
com.viewer.fastsecure
(FastFire) -
com.tf.thinkdroid.secviewer
(FastViewer)
The
disclosure
comes
as
the
North
Korean
advanced
persistent
threat
(APT)
actor
dubbed
ScarCruft
has
been
linked
to
different
attack
vectors
that
are
employed
to
deliver
PowerShell-based
backdoors
onto
compromised
hosts.