
State-sponsored hackers, backed by the regime in North Korea, are believed to be using zero-day exploits to target cybersecurity researchers working in the field of vulnerability research and development.
That’s the warning that was issued by Google’s Threat Analysis Group (TAG) at the end of last week, two-and-a-half years after the group first warned of the phenomenon.
According to Google, the North Korean hackers are using social media accounts to build relationships with targeted researchers, pretending to be interested in collaborating on investigations into vulnerabilities.
In one case, a legitimate security researcher was initially contacted on the site formerly known as Twitter, before conversation switched over to encrypted messaging apps such as Signal, WhatsApp, or Wire.
The North Korea-backed hackers behind the campaign are prepared to spend weeks or months fooling their intended targets into believing that they are fellow vulnerability researchers, establishing trustworthiness and credibility by linking to research on their blogs or Github.
Ultimately, once a degree of trust had been built between the hacker and the targeted researcher, the attacker would send a malicious file.
The malicious file, if opened by the researcher, would first perform checks to determine if it was being analysed in a virtual machine and – if not – send information and screenshots from the target’s computer to the attackers.
TAG says it is aware of “at least one actively exploited zero-day being used to target security researchers in the past several weeks,” adding that it has informed the affected vendor, who is in the process of patching the vulnerability.
Google shared a screenshot of a hacker-controlled Twitter profile used in the attacks, which has since been suspended.
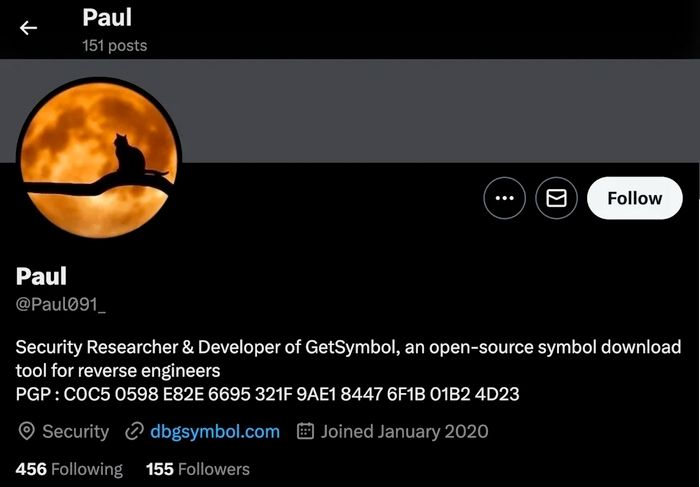
Google’s TAG team says that it has contacted targeted Gmail and Google Workspace users that it knows have been targeted, warning them of the campaign and advising them to ensure they have heightened security on place and that their devices are updated.
In addition, Google says that it has added all the websites and domains it has identified to be used in the attack to its Safe Browsing initiative, protecting users from being exploited. Furthermore, it has shared details of some of the various accounts created by the hackers on Twitter, Wire, and the infosec.exchange Mastodon instance.





