New Netskope Report Exposes Increasing Use of Cloud Apps to Spread Malware

A new report from Netskope detailing the top techniques used by cybercriminals to attack organizations found that cloud apps are increasingly being used by threat actors, representing 19% of all clicks on spearphishing links. The report also shed light on the attackers’ targets according to their financial or geopolitical motivations.
This Cloud and Threat report from Netskope, which is a U.S.-based company specializing in Secure Access Service Edge, reflected the first three quarters of 2023.
Jump to:
Top techniques used by cyberattackers
The most common tactics and techniques deployed by attackers to compromise systems, execute malicious code and communicate with the infected system are split into four categories by Netskope: initial access, malicious payloads execution, command and control and exfiltration.
Initial access
The easiest way for an attacker to access a targeted system is via its users; this is especially true if the targeted organization has patched all systems communicating with the internet and is therefore not subject to common vulnerabilities exploitation. Social engineering is the most popular method used by attackers to target organizations, whether it is by email (spearphishing), voice (vishing), SMS (smishing) or via social networks.
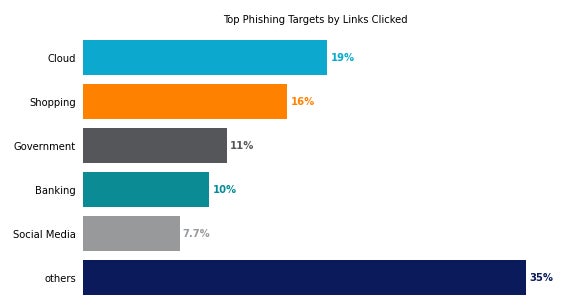
Netskope analyzed the phishing links users clicked on and concluded that users most frequently clicked on phishing links related to cloud apps (19%), followed by e-commerce websites (16%) such as Amazon, eBay or less popular shopping sites (Figure A).
Figure A
According to Netskope, one third of the phishing operations targeting cloud apps focused on Microsoft products. Netskope recently reported that Microsoft OneDrive is the most popular cloud app used in enterprises, so it is not a surprise that attackers leverage this target a lot, alongside Microsoft Teams, SharePoint and Outlook (Figure B).
Figure B

The second and third most-targeted apps are from Adobe (11%) and Google (8.8%).
Attackers still commonly use emails to target users, yet the success rate of those spearphishing operations is low. For starters, organizations often employ advanced anti-phishing filters to intercept phishing emails before they reach the users. Secondly, organizations try to raise awareness about those attack campaigns and educate their users to spot spearphishing emails. In reaction to these defenses, attackers deploy various alternative strategies to reach their targets.
- Search Engine Optimization: Oftentimes, attackers create web pages built around specific sets of keywords that are not common on the internet, so they can easily deploy SEO techniques to ensure their page comes in first in search engines’ results.
- Social media platforms and messaging apps: Attackers leverage popular social media platforms (e.g., Facebook) or messaging apps (e.g., WhatsApp) to reach targets with various baits.
- Voicemail and text messages: Attackers target users with voicemail (vishing) or SMS (smishing) to spread phishing links. This method has the benefit of targeting mobile phones, which are often less protected than computers.
- Personal email boxes: Attackers target users’ personal email accounts, which are often used on the same systems the victims use for work and might lead to sensitive information access.
When it comes to using attached files for phishing, 90% of the attacks use PDF files because it is a common format used in enterprises. Ray Canzanese, director of Netskope Threat Labs, told TechRepublic via email, that, “PDFs are popular among attackers because they are so commonly used for invoices, bills and other important correspondence. Adversaries create fake invoices and send them to their victims. Often, the only indicators that it is malicious are the URL or phone number it contains, and adversaries use obfuscation techniques to hide that from security solutions. These PDFs are created at such high volume and with so many variants that it is currently difficult for some security solutions to keep up. As with any adversary trends, security solutions will catch up and attackers will pivot to a new set of phishing techniques.”
Malicious payloads execution
Malicious payloads can be executed by unsuspecting users with the effect of providing the attacker with remote access to systems within the organization to operate more malicious activities, such as deploying ransomware or stealing information.
Attackers now use cloud storage apps a bit more (55%) than web storage (45%) on average for the first quarters of 2023 (Figure C).
Figure C
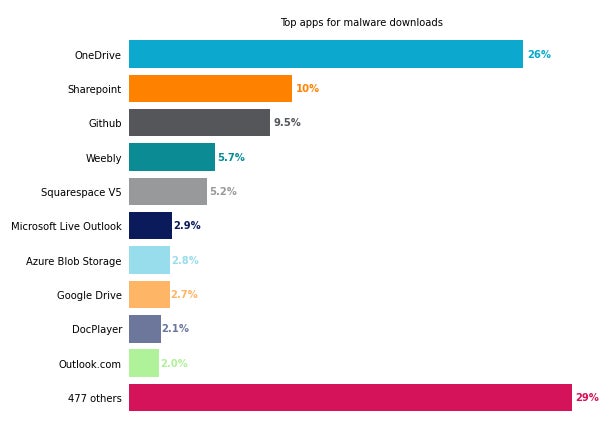
Microsoft OneDrive represents more than a quarter of the overall usage of cloud storage apps to host malware (26%), ahead of SharePoint (10%) and GitHub (9.5%).
Malware communications and data exfiltration
Attackers mostly use the HTTP (67%) and HTTPS (52%) protocols for communications between their malicious payloads and their command and control servers; these two protocols are generally fully allowed for users, as they are the main vector for browsing the internet and are not filtered by firewalls.
Far behind HTTP and HTTPS, the Domain Name System protocol is used in 5.5% of malware communications. The DNS protocol, which is never blocked and filtered in organizations, is not as stealthy as HTTP and HTTPS when transmitting data. Also, DNS makes it harder for attackers to blend with legitimate traffic from the organization and can transmit less data at a time than HTTP or HTTPS.
Most prevalent threat actors and their motivations
WizardSpider is the most prevalent threat actor
The most prevalent threat actor as observed by Netskope is Wizard Spider, who also goes by the aliases of UNC1878, TEMP.MixMaster or Grim Spider. Wizard Spider is responsible for the TrickBot malware, which originally was a banking trojan but evolved to a complex malware that also deployed additional third-parties’ malware such as ransomware.
Regarding possible affiliation, Canzanese told TechRepublic that “nearly every major cybercrime group today uses an affiliate model where anyone can become an affiliate and use the group’s tools against targets of their choosing. Wizard Spider is no different, with affiliates using their TrickBot malware and multiple ransomware families.”
Threat actors’ primary motivations and targets
According to Netskope’s report, most threat actors motivated by financial gain originate from Russia and Ukraine; those threat actors have mostly spread ransomware rather than any other kind of malware.
On the geopolitical side, Netskope observed that the biggest threats come from China, led by menuPass (also known as APT10, Stone Panda or Red Apollo) and Aquatic Panda.
The most targeted industries vary between financially-motivated actors and geopolitical ones, with financial services and healthcare being the most targeted by geopolitical actors.
Australia and North America are the two most-targeted regions for financial crime as compared to geopolitical targeting. When we asked Canzanese why Australia and North America were targeted, he replied, “If asked a different way, the answer perhaps becomes more readily apparent: Why is the relative percentage of geopolitical adversary group activity higher in the rest of the world? Such activity mirrors broader political, economic, military or social conflicts. So the higher percentage of geopolitical adversary activity in the rest of the world appears to be the result of active conflicts and the broader geopolitical climate in those regions.”
How to mitigate these cloud security threats
Companies should take these steps to mitigate such cloud security threats:
- Deploy email security solutions that can analyze attached files and links to detect phishing and malware.
- Educate users on how to detect phishing and social engineering schemes that might put them or the company at risk. In particular, users should not download any content from the internet, even if stored on cloud apps, that does not originate from a trusted contact.
- Keep all software and operating systems up to date and patched in order to avoid being compromised by a common vulnerability.
Disclosure: I work for Trend Micro, but the views expressed in this article are mine.











