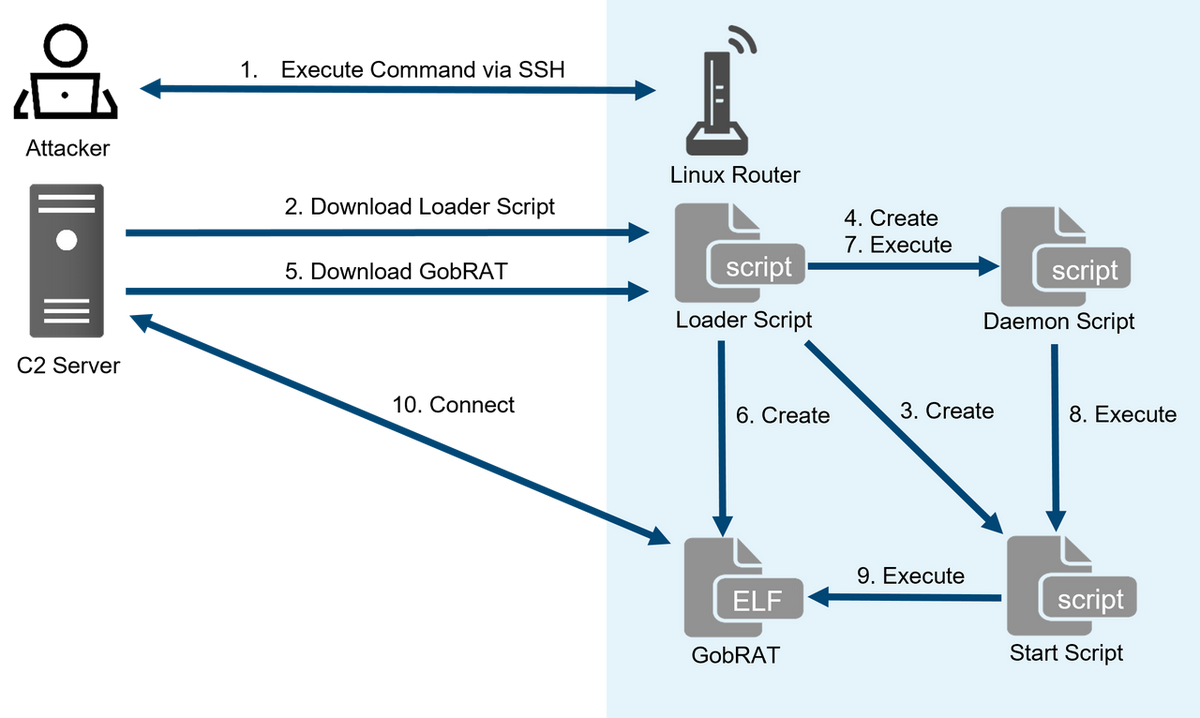
A
new
Golang
remote
access
trojan
(RAT),
tracked
as GobRAT,
is
targeting
Linux
routers
in
Japan,
the
JPCERT
Coordination
Center
warns.
JPCERT/CC
is
warning
of
cyberattacks
against
Linux
routers
in
Japan
that
have
been
infected
with
a
new
Golang
remote
access
trojan
(RAT)
called GobRAT.
Threat
actors
are
targeting
Linux
routers
with
publicly
exposed
WEBUI
to
execute
malicious
scripts
to
deploy
the
GobRAT
malware.
“Initially,
the
attacker
targets
a
router
whose
WEBUI
is
open
to
the
public,
executes
scripts
possibly
by
using
vulnerabilities,
and
finally
infects
the
GobRAT.”
reads
the
alert
published
by
the
JPCERT
Coordination
Center
(JPCERT/CC).
Loader
Script acts
as
a
loader,
it
supports
multiple
functions
for
downloading
and
deploying
the
GobRAT.
The
experts
noticed
an
SSH
public
key,
likely
used
as
a
backdoor,
which
is
hard-coded
in
the
script.
The
Loader
Script maintains
persistence
via
crontab
because
GobRAT
does
not
support
such
a
function.
The
Loader
Script includes
multiple
functions,
such
as
disabling
Firewall,
downloading
GobRAT
for
the
target
machine’s
architecture,
creating Start
Script and
making
it
persistent,
creating
and
running the
Daemon
Script,
and
registering
a
SSH
public
key
in
/root/.ssh/authorized_keys.
The
RAT
communicates
with
C2
server
via
TLS
and
can
execute
various
commands.
The
Japan
CERT
reported
that
the
RAT
is
packed
with
UPX
version
4
series.
The
researchers
observed
samples
for
multiple
architectures,
including
ARM,
MIPS,
x86,
and
x86-64.
Upon
starting
up,
the
GobRAT
checks
IP
address
and
MAC
address
of
itself,
uptime
by
uptime
command,
network
communication
status
by
/proc/net/dev.
The
malware
supports
22
commands,
the
researchers
have
identified
the
following
commands:
-
Obtain
machine
Information -
Execute
reverse
shell -
Read/write
files -
Configure
new
C2
and
protocol -
Start
socks5 -
Execute
file
in
/zone/frpc -
Attempt
to
login
to
sshd,
Telnet,
Redis,
MySQL,
PostgreSQL
services
running
on
another
machine
“In
recent
years,
different
types
of
malware
using
Go
language
have
been
confirmed,
and
the
GobRAT
malware
confirmed
this
time
uses
gob,
which
can
only
be
handled
by
Go
language,
for
communication.”
concludes
the
alert
that
also
provides
indicators
of
compromise.
“Please
continuously
beware
of
malware
that
infects
routers,
not
limited
to
GobRAT,
since
they
are
difficult
to
detect.”
Follow
me
on
Twitter: @securityaffairs and Facebook and Mastodon
(SecurityAffairs – hacking, malware)