Lumen disrupts AISURU and Kimwolf botnet by blocking over 550 C2 servers
Lumen disrupts AISURU and Kimwolf botnet by blocking over 550 C2 servers

Lumen’s Black Lotus Labs blocked over 550 C2 servers tied to the AISURU/Kimwolf botnet used for DDoS attacks and proxy abuse.
Lumen’s Black Lotus Labs disrupted over 550 command-and-control servers linked to the AISURU and Kimwolf botnet, a major network used for DDoS attacks and proxy abuse.
Acting as a DDoS-for-hire service, Aisuru avoids government and military targets, but broadband providers faced serious disruptions from attacks exceeding 1.5Tb/sec from infected customer devices.
Like other TurboMirai botnets, Aisuru incorporates additional dedicated DDoS attack capabilities and multi-use functions, enabling operators to carry out other illicit activities, including credential stuffing, artificial intelligence (AI)-driven web scraping, spamming, and phishing.
Attacks use UDP, TCP, and GRE floods with medium-sized packets and randomized ports/flags. Over 1Tb/sec traffic from compromised CPEs disrupts broadband, and 4gpps+ floods have caused router line card failures.
Kimwolf is a newly discovered Android botnet linked to the Aisuru botnet that has infected over 1.8 million devices and issued more than 1.7 billion DDoS attack commands, according to XLab.
The Kimwol Android botnet primarily targets TV boxes, compiled using the NDK and equipped with DDoS, proxy forwarding, reverse shell, and file management functions. It encrypts sensitive data with a simple Stack XOR, uses DNS over TLS to hide communication, and authenticates C2 commands with elliptic curve digital signatures. Recent versions even incorporate EtherHiding to resist takedowns via blockchain domains.
Kimwolf follows a naming pattern of “niggabox + v[number]”; versions v4 and v5 have been tracked. By taking over one C2 domain, researchers observed around 2.7 million IPs interacting over three days, indicating a likely infection scale exceeding 1.8 million devices. Its infrastructure spans multiple C2s, global time zones, and versions, making it hard to estimate the total number of infections.
The botnet borrows the code from the Aisuru family, however, operators redesigned it to evade detection. Its primary function is traffic proxying, though it can execute massive DDoS attacks, as seen in a three-day period issuing 1.7 billion commands between November 19 and 22.
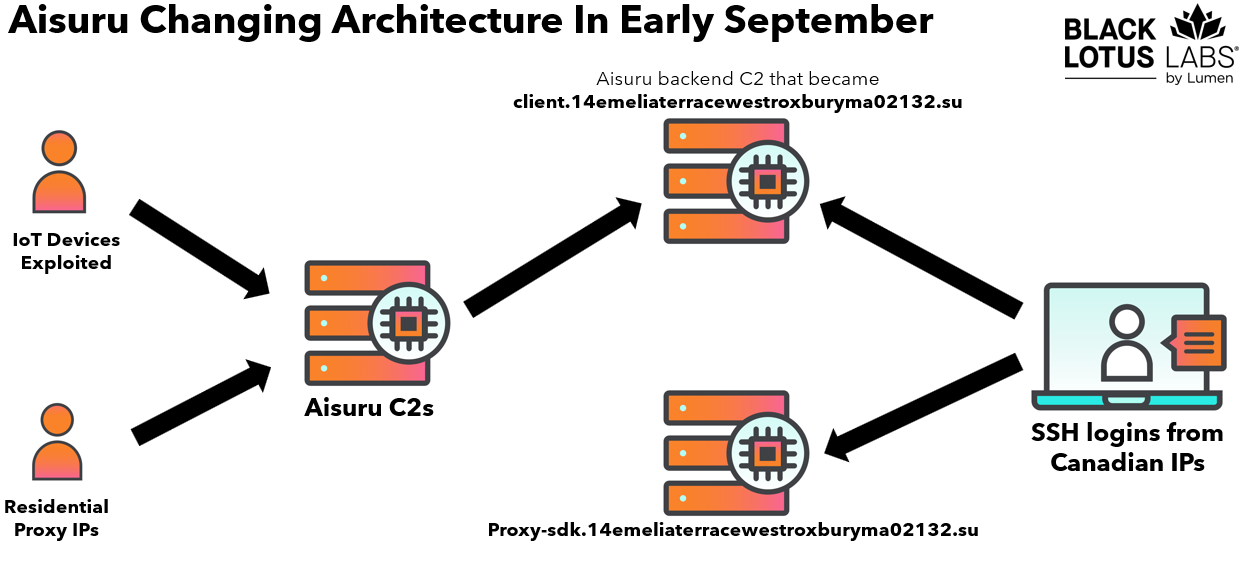
Lumen saw bot traffic to AISURU C2 servers surge from 50,000 to 200,000 daily in September 2025. After confirming a new botnet, it blocked traffic and null-routed over 550 C2 nodes.
Analyzing the botnet command-and-control infrastructure and residential proxy traffic, the researchers identified connections to Canadian IP addresses and shared their findings with law enforcement.
“The Canadian IPs in question were using SSH to access 194.46.59[.]169, which resolved to proxy-sdk.14emeliaterracewestroxburyma02132[.]su. In short order, we would learn that the Aisuru backend C2 we were tracking adopted the domain name client.14emeliaterracewestroxburyma02132[.]su, a similarity that further tied these servers together” reads the report published by Lumen.

In early October, researchers identified infrastructure changes that marked the emergence of a new botnet, Kimwolf. Kimwolf grew explosively, adding hundreds of thousands of bots within weeks, largely by exploiting vulnerable residential proxy services. By mid-October, the botnet reached about 800,000 infected devices and actively scanned proxy networks to fuel its growth.
Black Lotus Labs began disrupting the Kimwolf botnet in October by quickly null-routing its command-and-control servers. Although the operators adapted and restored operations within hours, Lumen continued blocking new infrastructure as it appeared. By tracking malware servers and working with industry partners, Lumen took a proactive approach to limit the botnet’s strength. Over four months, the team null-routed more than 550 Aisuru/Kimwolf servers and fed indicators into its security products to protect customers, pledging to continue disruption efforts.

“To date, we have null-routed over 550 Aisuru/Kimwolf servers in 4 months as part of our efforts to combat this botnet, leading its operators to some distress, as noted in Xlabs’ post, showing the actors addressing Lumen with profanity in one DDoS payload” concludes the report.
Follow me on Twitter: @securityaffairs and Facebook and Mastodon
(SecurityAffairs – hacking, malware)