Infy Returns: Iran-linked hacking group shows renewed activity
Infy Returns: Iran-linked hacking group shows renewed activity

Researchers report renewed activity by Iran-linked Infy (Prince of Persia), showing the hacking group remains active and dangerous after years of silence.
SafeBreach researchers have spotted renewed activity from the Iran-linked APT group Infy, also known as Prince of Persia, nearly five years after its last known campaigns in Europe. SafeBreach warns the group remains active, larger in scale than previously thought, and still poses a serious threat.
Iranian Infy is a suspected Iranian-linked cyber espionage group that has been active since at least 2004; It is known for long-running spying campaigns against governments and organizations.
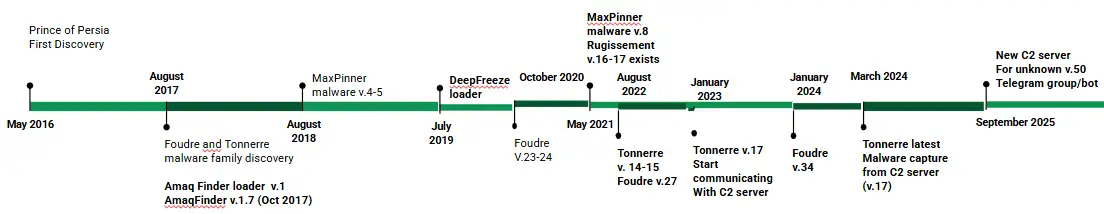
Prince of Persia (also known as Infy) is an advanced persistent threat (APT) group believed to be linked to the Iranian government. First exposed in 2016, it targeted Iranian dissidents, civil society members, journalists, and diplomats, rather than pursuing financial gain. The group used sophisticated techniques, including website compromises and malware such as Foudre and Tonnerre, deployed in stages to profile and selectively spy on victims.
After a takedown by Palo Alto Networks, the group temporarily lost access to most victims but demonstrated unusual capabilities, such as traffic manipulation inside Iran, reinforcing state-level ties. Although public activity seemed to stop around 2022, researchers continued tracking the group using long-term indicators. This sustained monitoring revealed that Prince of Persia never fully disappeared, but instead adapted its tools and infrastructure to operate more stealthily under the radar.
Recent research shows the Iranian-linked Prince of Persia (Infy) group remains highly active and more capable than previously thought. Over the past three years, SafeBreach uncovered multiple campaigns using many malware variants and C2 servers. At least three Tonnerre variants run in parallel, including a new v50 seen in September 2025 with a previously unknown DGA. For the first time since 2016, Tonnerre v50 redirects victims to a Telegram group and bot, likely replacing older FTP-based data exfiltration. Analysts also found new and unknown malware families, spying tools targeting Telegram, and evidence of continuous testing infrastructure. Despite defenses, victim data could still be retrieved from both old and new C2 servers.
SafeBreach researchers found that the Prince of Persia APT actively hid its operations by frequently changing C2 servers, deleting malware from low-value victims, and upgrading tools in place. New findings reveal updated Foudre and Tonnerre variants, a redesigned C2 structure, and the use of Telegram bots for command and data exfiltration. Infrastructure, malware features, IP evidence, and Persian identifiers strongly reinforce attribution to an Iran-linked threat group active since at least 2017.
“Most of the victims were located in Iran, but there were some across Europe and countries like Iraq, Turkey, India, and Canada. While we have chosen not to publish the data here due to privacy concerns, we are more than willing to share the data with authorized law enforcement agencies.” reads the report published by SafeBreach.
SafeBreach Labs has tracked the Iran-linked Prince of Persia group since 2019 and maintained visibility even after it appeared dormant in 2022. The research reveals continued development of its Foudre and Tonnerre malware families, new infection vectors, and evolving C2 infrastructures. Foudre v34 now spreads via malicious Excel files with embedded executables, evading antivirus detection and using a new two-stage DGA algorithm. Tonnerre v17 shares a similar DGA and shows careful timing tied to real-world events.
The group operates complex C2 server structures to manage upgrades, validate domains, exfiltrate data, and separate real victims from attacker test systems. Researchers also uncovered techniques used to erase infections and migrate victims between C2 servers to cover tracks. Newer variants integrate Telegram for command-and-control, while older malware such as Amaq News Finder, MaxPinner, Deep Freeze, and Rugissement highlight a long-running, adaptable toolset. Overall, the findings show a persistent, highly organized espionage operation with continuous innovation.
“Despite the appearance of having gone dark in 2022, Prince of Persia threat actors have done quite the opposite. Our ongoing research campaign into this prolific and elusive group has highlighted critical details about their activities, C2 servers, and identified malware variants in the last three years.” concludes the report. “This threat group is still active, relevant, and dangerous.”
Follow me on Twitter: @securityaffairs and Facebook and Mastodon
(SecurityAffairs – hacking, Infy)