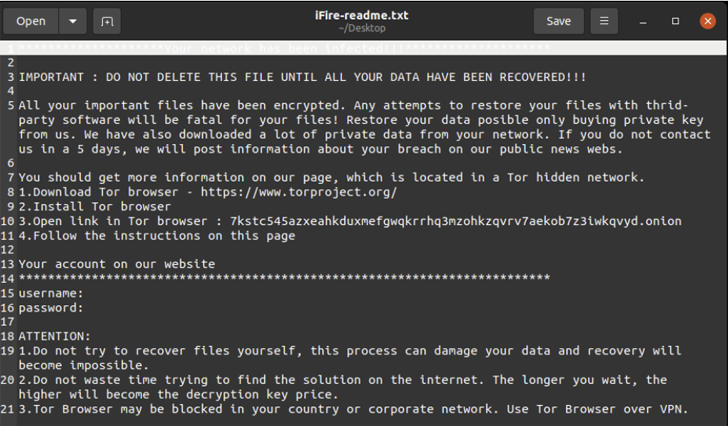
IceFire Ransomware Exploits IBM Aspera Faspex to Attack Linux-Powered Enterprise Networks

A
previously
known
Windows-based
ransomware
strain
known
as
IceFire
has
expanded
its
focus
to
target
Linux
enterprise
networks
belonging
to
several
media
and
entertainment
sector
organizations
across
the
world.
The
intrusions
entail
the
exploitation
of
a
recently
disclosed
deserialization
vulnerability
in
IBM
Aspera
Faspex
file-sharing
software
(CVE-2022-47986,
CVSS
score:
9.8),
according
to
cybersecurity
company
SentinelOne.
“This
strategic
shift
is
a
significant
move
that
aligns
them
with
other
ransomware
groups
that
also
target
Linux
systems,”
Alex
Delamotte,
senior
threat
researcher
at
SentinelOne,
said
in
a
report
shared
with
The
Hacker
News.
A
majority
of
the
attacks
observed
by
SentinelOne
have
been
directed
against
companies
located
in
Turkey,
Iran,
Pakistan,
and
the
U.A.E.,
countries
that
are
not
typically
targeted
by
organized
ransomware
crews.
IceFire
was
first
detected
in
March
2022
by
the
MalwareHunterTeam,
but
it
wasn’t
until
August
2022
that
victims
were
publicized
via
its
dark
web
leak
site,
according
to
GuidePoint
Security,
Malwarebytes,
and
NCC
Group.
The
ransomware
binary
targeting
Linux
is
a
2.18
MB
64-bit
ELF
file
that’s
installed
on
CentOS
hosts
running
a
vulnerable
version
of
IBM
Aspera
Faspex
file
server
software.
It’s
also
capable
of
avoiding
encrypting
certain
paths
so
that
the
infected
machine
continues
to
be
operational.
WEBINAR
Discover
the
Hidden
Dangers
of
Third-Party
SaaS
Apps
Are
you
aware
of
the
risks
associated
with
third-party
app
access
to
your
company’s
SaaS
apps?
Join
our
webinar
to
learn
about
the
types
of
permissions
being
granted
and
how
to
minimize
risk.
“In
comparison
to
Windows,
Linux
is
more
difficult
to
deploy
ransomware
against–particularly
at
scale,”
Delamotte
said.
“Many
Linux
systems
are
servers:
typical
infection
vectors
like
phishing
or
drive-by
download
are
less
effective.
To
overcome
this,
actors
turn
to
exploiting
application
vulnerabilities.”
The
development
comes
as
Fortinet
FortiGuard
Labs
disclosed
a
new
LockBit
ransomware
campaign
employing
“evasive
tradecraft”
to
avoid
detection
through
.IMG
containers
that
bypass
Mark
of
The
Web
(MotW)
protections.