Phishing,
the
theft
of
users’
credentials
or
sensitive
data
using
social
engineering,
has
been
a
significant
threat
since
the
early
days
of
the
internet
–
and
continues
to
plague
organizations
today,
accounting
for
more
than
30%
of
all
known
breaches.
And
with
the
mass
migration
to
remote
working
during
the
pandemic,
hackers
have
ramped
up
their
efforts
to
steal
login
credentials
as
they
take
advantage
of
the
chaos
and
lack
of
in-person
user
verification.
This
has
led
to
the
revival
of
the
old-school
technique
of
vishing,
which,
like
phishing
online,
involves
using
social
engineering
over
the
phone
to
steal
sensitive
information.
Vishing
attacks
have
been
on
the
rise
as
a
result,
with
69%
of
companies
experiencing
them
in
2021,
up
from
54%
in
2020.
These
attacks
often
take
the
form
of
job
or
tech
support
scams
and
can
be
incredibly
convincing.
In
August
2020,
the
FBI
along
with
the
CISA
issued
a
warning
regarding
remote
users
being
targeted
by
attackers
spoofing
organizations’
business
numbers
and
impersonating
the
IT
service
desk.
Vishing
bypassing
2FA
One
of
the
most
concerning
aspects
of
vishing
is
the
attackers’
ability
to
bypass
two-factor
authentication
(2FA)
security
measures.
2FA
is
a
popular
form
of
multi-factor
authentication
that
requires
users
to
provide
two
types
of
information:
a
password
and
a
one-time
code
sent
via
SMS.
Attackers
achieve
this
by
impersonating
a
support
representative
and
requesting
the
victim’s
2FA
code
over
the
phone.
If
the
victim
provides
the
code,
the
attacker
can
gain
full
access
to
their
account,
potentially
leading
to
financial
or
personal
information
being
compromised.
Attackers
impersonating
as
help
desk
support
A
common
instance
is
when
individuals
receive
a
pop-up
alert
claiming
that
their
device
has
been
breached
or
infected
with
malware
and
that
professional
phone
support
is
required
to
fix
the
problem.
Alternatively,
victims
may
receive
a
call
from
an
alleged
tech
support
representative
from
a
reputable
software
provider,
claiming
that
malware
has
been
detected
on
their
machine.
The
attacker
will
try
to
convince
the
user
to
download
remote
access
software
under
the
pretext
of
corporate
IT
help
desk
representatives.
This
is
the
final
phase
of
the
scam,
after
which
it’s
checkmate
for
the
unsuspecting
victims
and
a
potential
payday
for
the
attackers.
Attackers
impersonating
the
help
desk
is
clearly
working:
in
July
2020,
Twitter
experienced
a
major
security
breach
when
hackers
used
a
vishing
scam
to
successfully
access
dozens
of
high-profile
accounts,
including
those
of
Barack
Obama,
Joe
Biden,
Jeff
Bezos,
and
Elon
Musk.
The
attackers
used
these
accounts
to
tweet
a
bitcoin
scam,
resulting
in
the
swift
theft
of
over
$100,000.
Unlike
traditional
scams,
these
attacks
target
carefully
selected
individuals
by
gathering
extensive
information
about
them
from
social
media
and
other
public
sources.
This
information
is
then
used
to
identify
employees
who
are
most
likely
to
cooperate
and
have
access
to
the
desired
resources,
at
which
point
attackers
are
primed
and
ready
to
wreak
havoc.
A
twist
as
attackers
call
the
help
desk
&
impersonate
end-users
Social
engineering
attacks
are
carefully
fabricated
with
collected
data
and
can
be
used
to
impersonate
an
end-user
on
a
call
to
the
help
desk.
An
experienced
attacker
can
easily
acquire
answers
to
security
questions
from
various
sources,
especially
knowing
end-users
put
too
much
personal
information
on
social
media
and
the
web.
Microsoft
said
that
LAPSUS$,
a
known
threat
group,
calls
on
a
targeted
organization’s
help
desk
and
attempts
to
convince
support
personnel
to
reset
a
privileged
account’s
credentials.
The
group
would
use
previously
gathered
information,
have
an
English-speaking
caller
speak
with
the
help
desk.
They
would
be
able
to
answer
common
recovery
prompts
such
as
“first
street
you
lived
on”
or
“mother’s
maiden
name”
from
data
collected
to
convince
help
desk
personnel
of
authenticity.
In
another
attempt
to
reach
the
help
desk,
slack
was
used.
Electronic
Arts
had
780GB
of
source
code
downloaded
by
hackers
presumed
to
also
be
LAPSUS$.
The
threat
actors
used
the
authentication
cookies
to
impersonate
an
already-logged-in
employee’s
account
and
access
EA’s
Slack
channel,
then
convinced
an
IT
support
employee
into
granting
them
access
to
the
company’s
internal
network.
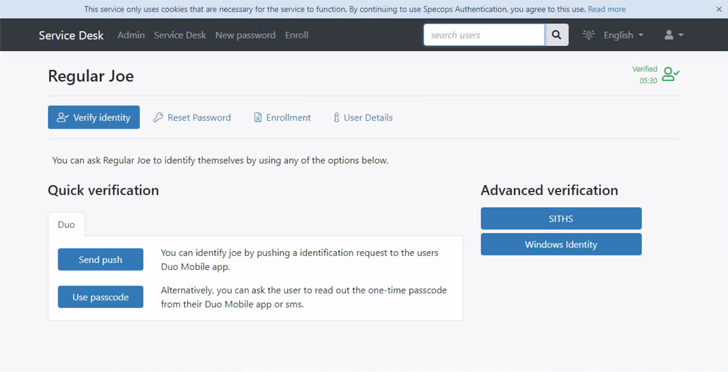
How
can
your
Help
Desk
know
who’s
really
calling
Verifying
user
identity
in
the
vishing
age
is
more
important
than
ever.
With
the
rise
of
cyber-attacks
and
social
engineering,
it’s
crucial
for
organizations
to
have
security
measures
in
place
to
safeguard
their
employees,
protect
their
sensitive
information,
and
prevent
unauthorized
access.
One
effective
way
to
safeguard
against
these
types
of
attacks
is
to
implement
a
secure
service
desk
solution,
which
allows
for
the
verification
of
user
accounts
with
existing
data
beyond
just
knowledge-based
authentication.
This
can
be
achieved
by
sending
a
one-time
code
to
the
mobile
number
associated
with
the
user’s
account
or
using
existing
authentication
services
to
verify
callers.
Enforcing
user
authentication
is
another
key
aspect
of
Specops
Secure
Service
Desk.
This
ensures
that
information
and
password
resets
are
only
offered
to
authorized
users,
which
is
essential
for
protecting
high-security
accounts
and
adhering
to
regulatory
requirements.
With
a
Secure
Service
Desk,
you
can
remove
the
opportunity
for
user
impersonation
by
requiring
verification
with
something
the
user
has
and
not
just
relying
on
something
the
user
–
or
an
attacker
–
may
know.
In
addition
to
verifying
and
enforcing
user
authentication,
a
secure
service
desk
also
allows
for
the
secure
reset
or
unlocking
of
user
accounts.
This
is
done
only
after
the
user
has
been
successfully
verified
and
can
be
combined
with
a
self-service
password
reset
tool
to
assist
with
account
unlocks
and
the
password
reset
process.
With
vishing
scams
showing
no
signs
of
slowing
down,
investing
in
Specops
Secure
Service
Desk
solution
could
be
a
critical
step
for
organizations
looking
to
protect
their
people
from
even
the
subtlest
of
social
engineering
attempts.
By
instilling
a
comprehensive
and
effective
way
to
verify
user
identity,
enforce
user
authentication,
and
reset
or
unlock
user
accounts,
would-be
victims
can
rest
assured
that
they’ll
always
know
who’s
really
calling.