Deploying Yeti gazes Ukraine exploiting WinRAR weak point to distribute COOKBOX Malware

Russia-linked threat actor Deploying Yeti is focusing on Ukraine with a deceptive operation to spread the PowerShell malware COOKBOX.
Phishing attempts by a Russia-related threat actor Deploying Yeti (also known as UAC-0149) aimed at Ukraine were uncovered by Cloudflare researchers. Details of the ongoing efforts to prevent and hinder this threat endeavor were shared in a published report.
Following the commencement of Russia’s invasion of Ukraine on February 24, 2022, Ukraine enforced a temporary halt on evictions and cutting off utility services for unsettled debts. The moratorium concluded in January 2024, leaving many individuals in significant debt and under financial strain. Taking advantage of this situation, the Deploying Yeti campaign utilized debt-related bait to deceive targets into accessing malicious links enclosed in the messages. Once the files were opened, the PowerShell malware COOKBOX infiltrated the targeted system, thereby enabling the attackers to introduce additional payloads and take control of the system.
The threat actors exploited the vulnerability in WinRAR known as CVE-2023-38831 to introduce malware into the targets’ systems.
Cloudflare pointed out that the tactics, tools, and procedures (TTPs) used by Deploying Yeti closely resemble those documented by Ukraine CERT while scrutinizing the UAC-0149 cluster.
UAC-0149 focused on Ukrainian defense organizations with COOKBOX malware since at least late 2023.
“The threat actor utilizes dynamic DNS (DDNS) for their infrastructure and maximizes cloud-based platforms for hosting malicious content and for malware command and control (C2).” according to the report released by Cloudflare. “Our scrutiny of Deploying Yeti TTPs implies that this is presumably a threat group aligned with Russia. The actor seems to mainly aim at Ukrainian military entities.”
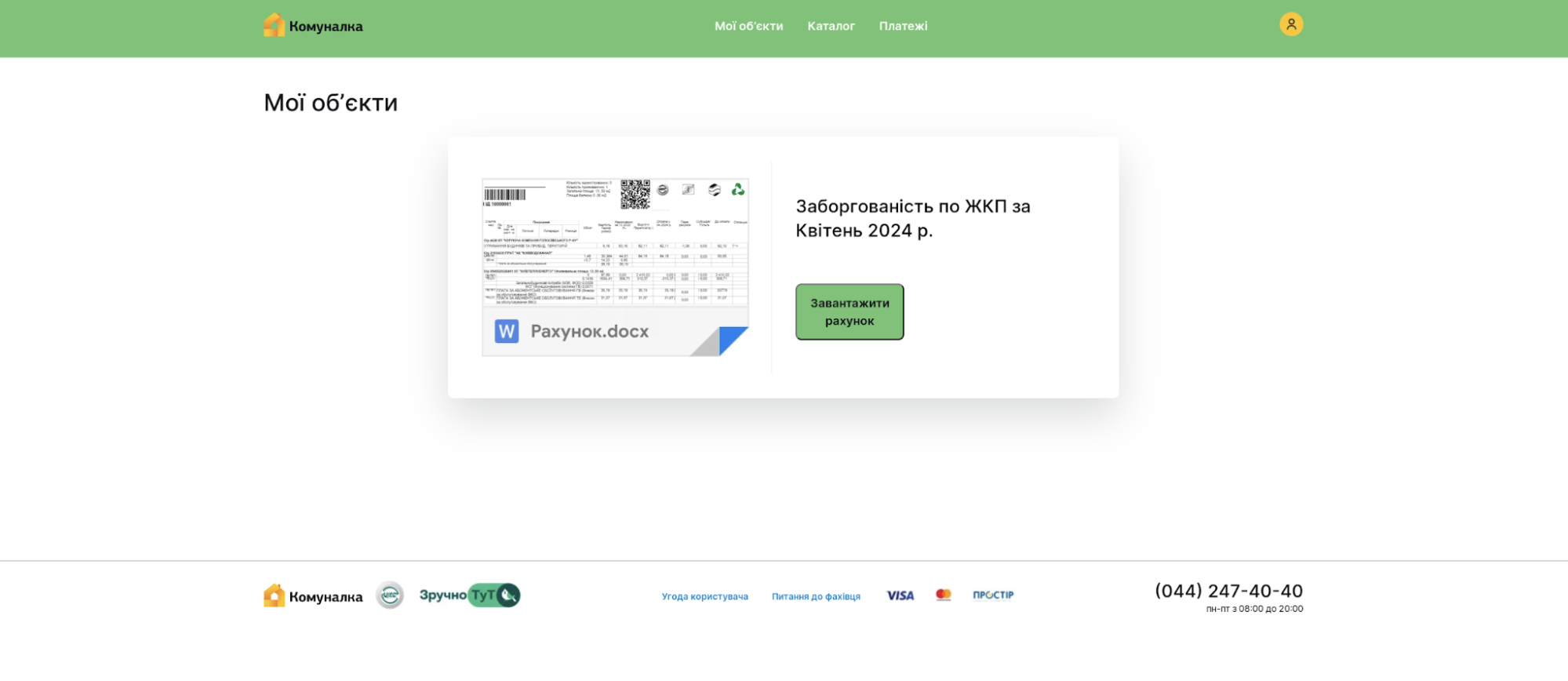
Malicious actors steered users towards a counterfeit version of the communal housing website Kyiv Komunalka (https://www.komunalka.ua) operated on a GitHub page controlled by the actors (hxxps[:]//komunalka[.]github[.]io). Komunalka serves as an online payment processor for essential services in the Kyiv area.
Deploying Yeti most likely led users to this website via phishing emails or encrypted Signal messages. Upon reaching the fabricated site, a prominent green button prompted individuals to download a file named “Рахунок.docx” (“Invoice.docx”), which turned out to be a malevolent archive titled “Заборгованість по ЖКП.rar” (“Debt for housing and utility services.rar”).

When the RAR file is launched, the COOKBOX malware is activated by the CVE-2023-38831 exploit.
Contained within the RAR archive are multiple files, one of which includes the Unicode character “U+201F,” interpreted as whitespace on Windows operating systems. This character can obfuscate file extensions by introducing an abundance of whitespace, disguising a malicious CMD file (“Рахунок на оплату.pdf[unicode character U+201F].cmd”) as a PDF document. The archive also features a harmless PDF file with an identical name but without the Unicode character. Upon unzipping the archive, the directory name matches the benign PDF’s name. This naming alignment capitalizes on the WinRAR vulnerability CVE-2023-38831, causing the malicious CMD file to execute when the victim tries to access the benign PDF.
“The CMD file contains the Deploying Yeti PowerShell malware known as COOKBOX. The malware is structured to remain persistently on a host, acting as an entry point in the compromised device. Upon installation, this version of COOKBOX will communicate with the DDNS domain postdock[.]serveftp[.]com for C2, expecting PowerShell cmdlets to be executed by the malware.” states the report. “Alongside COOKBOX, several disguise documents are opened, containing hidden tracking links utilizing the Canary Tokens service.”
For the latest updates, connect with me on Twitter: @securityaffairs, Facebook, and Mastodon
(SecurityAffairs – hacking, Deploying Yeti)







