Researchers
reported
that
Dark
Pink
APT
employed
a
malware
dubbed
KamiKakaBot
against
Southeast
Asian
targets.
In
February
2023,
EclecticIQ
researchers
spotted
multiple
KamiKakaBot
malware
samples
that
were
employed
by
the
Dark
Pink
APT
group
(aka
Saaiwc)
in
attacks
against
government
entities
in
Southeast
Asia
countries.
The
activity
of
the
group
was
first
detailed
by
Group-IB
in
January
2023,
the
group
used
custom
malware
such
as
KamiKakaBot
and
TelePowerBot.
The
Dark
Pink
APT
is
active
in
the
ASEAN
region
and
has
been
active
since
at
least
mid-2021.
The
group
focuses
on
military
and
government
organizations
to
steal
sensitive
information,
including
confidential
data
and
intellectual
property.
The
main
difference
between
the
January
campaign
and
the
attacks
spotted
by
EclecticIQ
is
that
the
threat
actors
have
improved
the
malware’s
obfuscation
routine
to
avoid
detection.
The
researchers
noticed
overlaps
in
malware
delivery
and
adversary
techniques
between
Earth
Yako
and
Dark
Pink
APT
groups,
including
the
use
of
Winword.exe
for
DLL
Hijacking.
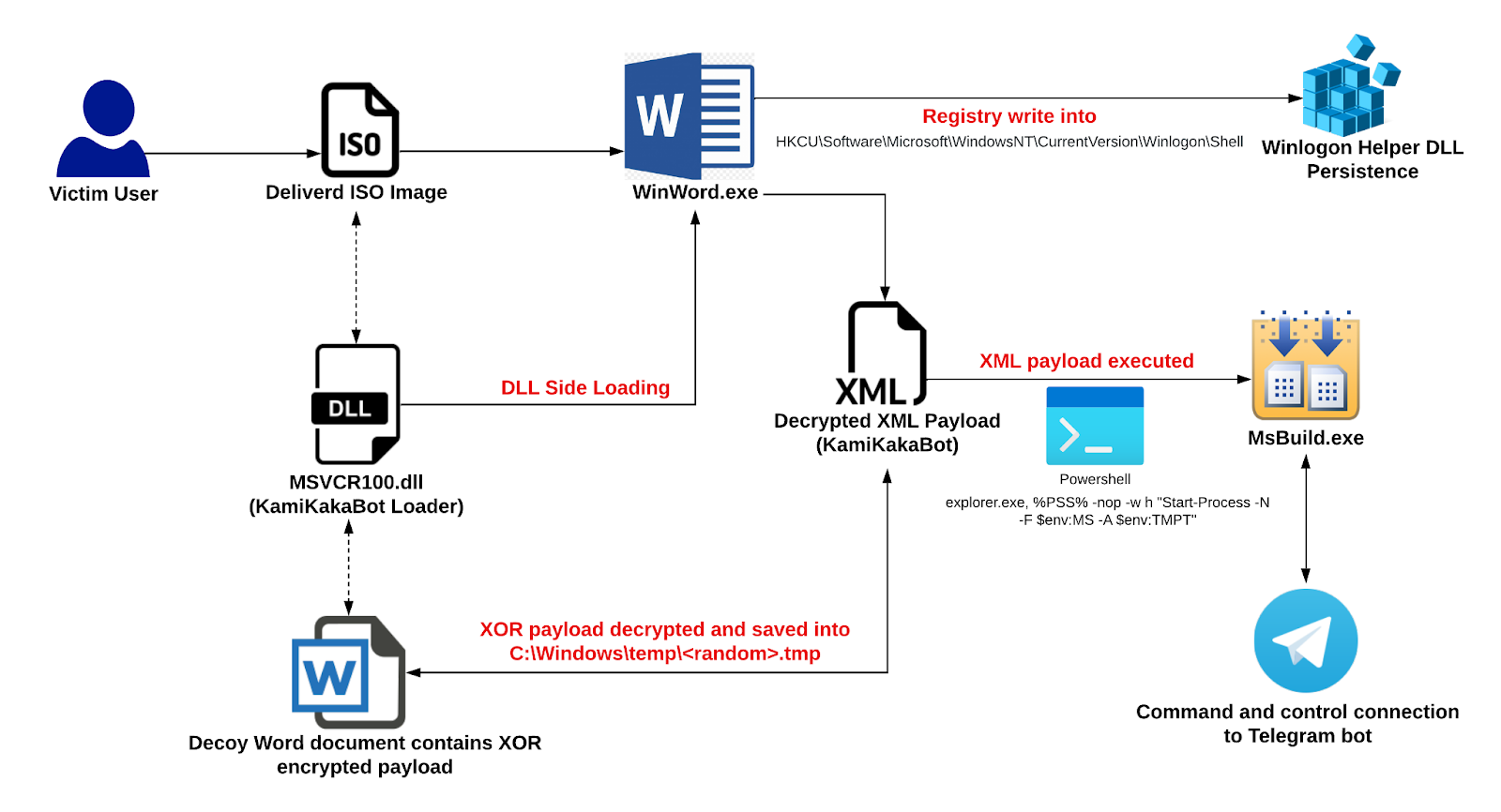
The
KamiKakaBot
malware
spreads
via
phishing
emails
that
contain
a
malicious
ISO
file
as
an
attachment.
The
ISO
image
file
contains
a
WinWord.exe
which
is
legitimately
signed
by
Microsoft,
which
is
used
to
launch
DLL
side-loading
attack,
a
loader
(MSVCR100.dll),
and
a
decoy
Microsoft
Word
document.
Upon
clicking
on
WinWord.exe,
the
loader
is
executed
in
the
memory
of
WinWord.exe.
The
malware
gain
persistence
via
a
registry
key
into
HKCUSoftwareMicrosoftWindows
NTCurrentVersionWinlogonShell
used
to
abuse
features
of
Winlogon
(Windows
component).
“The
ISO
file
also
contains
a
decoy
Word
document
that
has
an
XOR-encrypted
section.
The
KamiKakaBot
loader
uses
this
section
to
decrypt
the
XOR-encrypted
content
from
the
decoy
file
then
writes
the
decrypted
XML
KamiKakaBot
payload
into
the
disk
(C:Windowstemp)
and
executes
it
via
a
living-off-the-land
binary
called
MsBuild.exe.”
reads
the
analysis
published
by
EclecticIQ.
The
attackers
employed
different
lures
in
each
decoy
Word
document
to
trick
their
victims
into
opening
the
attachment.
“Before
the
execution
of
the
decrypted
XML
payload,
KamiKakaBot
loader
writes
a
registry
key
into
HKCUSoftwareMicrosoftWindows
NTCurrentVersionWinlogonShell
to
abuse
features
of
Winlogon
(Windows
component)
for
establishing
persistent
access.”
KamiKakaBot
can
steal
data
stored
in
popular
web
browsers,
including
Chrome,
MS
Edge,
and
Firefox.
Then
the
stolen
data
is
sent
to
the
attackers’
Telegram
bot
channel
in
a
compressed
ZIP
format.
The
malware
also
supports
an
update
mechanism
and
can
perform
remote
code
execution
on
the
targeted
device.
The
C2
communication
relies
on
a
Telegram
bot
controlled
by
the
threat
actor.

The
experts
believe
the
Dark
Pink
APT
group
is
likely
a
cyber
espionage
threat
actor
that
focuses
on
the
relationship
between
ASEAN
and
European
nations
to
create
phishing
lures.
“The
result
of
the
analysis
showed
that
the
threat
actors
are
still
utilizing
the
same
adversary
tactics,
techniques,
and
procedures
(TTPs)
to
deliver
and
execute
the
KamiKakaBot
malware,
with
only
small
changes
made
to
the
obfuscation
routine
to
increase
the
infection
rate
and
evade
anti-malware
solutions.”
concludes
the
report.
“Based
on
the
TTPs
used
in
this
campaign,
EclecticIQ
researchers
strongly
believe
that
the
Dark
Pink
APT
group
is
very
likely
a
cyber
espionage-motivated
threat
actor
that
specifically
exploits
relations
between
ASEAN
and
European
nations
to
create
phishing
lures
during
the
February
2023
campaign.”
Follow
me
on
Twitter:
@securityaffairs
and
Facebook
and
Mastodon
(SecurityAffairs –
hacking,
Dark
Pink
APT)