Christie’s data breach impacted 45,798 individuals

Auction house Christie’s disclosed that the data breach caused by the recent ransomware attack affected 45,000 individuals.
Christie’s auction house revealed a security breach at the end of May following a ransomware threat from the group RansomHub. This cyber incident, which occurred in early May, rendered the auction house’s website inaccessible after the attack.
As reported by BBC, Christie’s encountered difficulties in selling valuable items worth around $840 million due to the cyberattack. Notably, the spring auctions involved items such as a $35 million Vincent van Gogh painting and rare wines, among other valuables. The cyber incident led to delays in some of the sales.
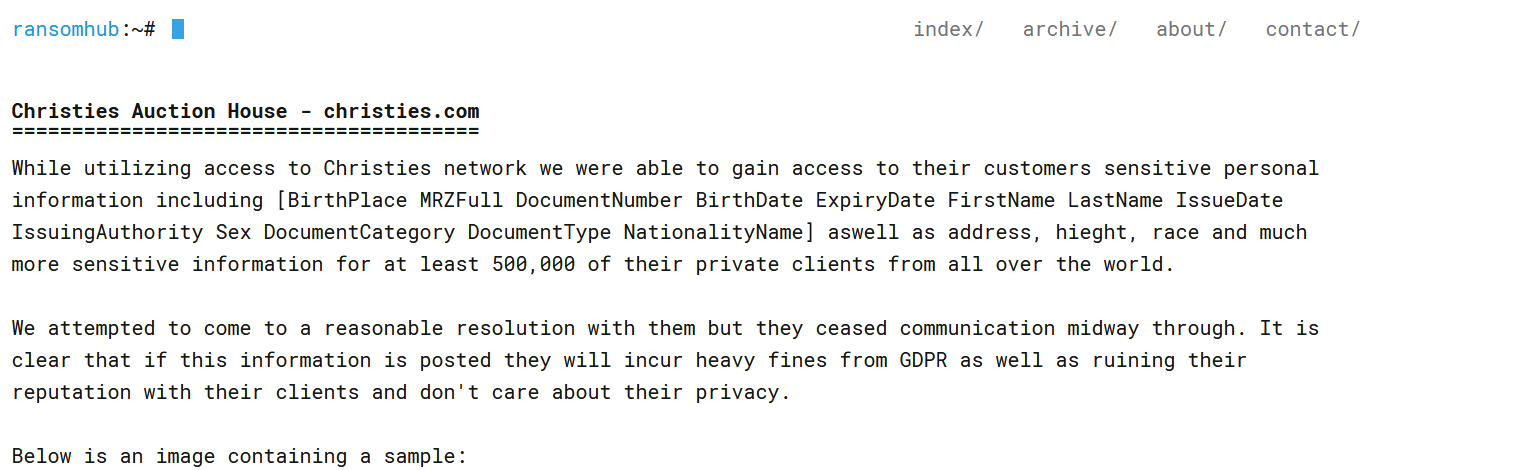
RansomHub took credit for the attack and listed the company on its Tor leak site. The group claimed to have obtained 2GB of sensitive data, including personal details of at least 500,000 Christie’s customers.
According to the group, “Utilizing access to Christies network, we were able to obtain their clients’ confidential personal data including [BirthPlace MRZFull DocumentNumber BirthDate ExpiryDate FirstName LastName IssueDate IssuingAuthority Sex DocumentCategory DocumentType NationalityName], along with addresses, heights, races, and other sensitive information for over 500,000 clients worldwide.”.

The group threatened to release the stolen data if the ransom was not paid by Sunday, June 2,024.
The gang attempted to negotiate the ransom with the auction house without success. They hinted that Christie could face substantial fines under GDPR once the stolen data is made public.
The auction house promptly informed privacy authorities and law enforcement about the breach.
As detailed in Christie’s Individual Notification Letter shared with the Maine Attorney General, the hackers accessed files containing personal data like names, driver’s license numbers, and non-driver identification serials. This incident affected 45,798 individuals.
“We discovered a cybersecurity incident affecting some of our systems on May 9, 2024. Upon learning of the event, we took immediate measures to secure our environment, launched an investigation, and engaged external cybersecurity specialists. We also alerted law enforcement and continue to cooperate with their inquiries. The investigation revealed unauthorized access by an external entity to some of our systems and files on May 8-9, 2024, during which certain files were copied.” according to the letter. “Following the investigation on May 30, 2024, we meticulously reviewed the files to identify impacted individuals and promptly notified them.”.
The company is providing identity protection and fraud monitoring services for one year.
Follow me on Twitter: @securityaffairs and Facebook and Mastodon
(SecurityAffairs – hacking, data breach)










