The SPECTR Malware was wielded by Affirmative-0020 to target the defense forces of Ukraine

Ukraine CERT-UA alerted about cyber offenses aiming at defense forces with SPECTR malware in a cyber espionage endeavor named SickSync.
Ukraine’s Computer Emergency Response Team (CERT-UA) issued a warning regarding a cyber espionage operation targeting the defense forces within Ukraine. This attack is attributed to the culprit Affirmative-0020, which utilized the SPECTR Malware as part of the SickSync campaign.
The perpetrator Affirmative-0020, also known as Vermin, functions under the jurisdiction of the law enforcement bodies of the temporarily held Luhansk region.
SPECTR Malware has been operational since at least 2019, enabling operators to purloin confidential data and files from the infected system. It leverages the standard synchronization capabilities of the legitimate SyncThing software.
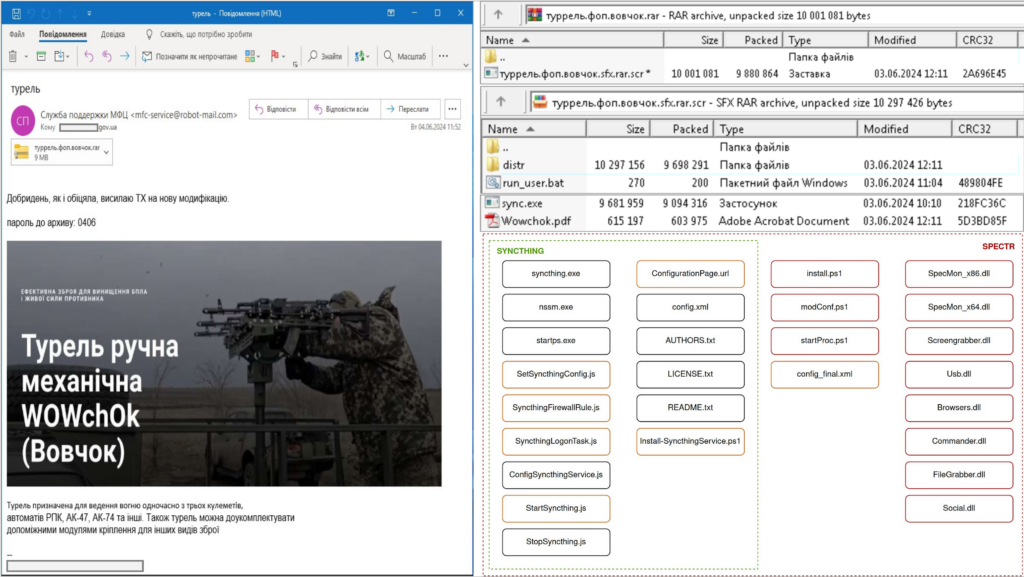
Miscreants disseminated spear-phishing communications with an attachment presented as a password-protected archive labeled “turrel.fop.vovchok.rar”.

The archive contains an additional archive named RARSFX archive (“turrel.fop.ovchok.sfx.rar.scr”) harboring the “Wowchok.pdf” decoy file, the “sync.exe” EXE installer crafted using InnoSetup, and the BAT file ” run_user.bat” utilized for initial launch.
The UA-CERT notes that the “sync.exe” file comprises genuine SyncThing components and SPECTR malware files, along with supplementary libraries and scripts. Attackers tampered with the standard files of SyncThing software to alter directory names, scheduled tasks, disable message display functionalities for users, etc.
The SPECTR information exfiltrator captures screenshots every 10 seconds, retrieves files, extracts data from removable USB drives, and pilfers credentials from web browsers and applications such as Element, Signal, Skype, and Telegram.
“It should be observed that the pilfered information is duplicated into subfolders within the directory %APPDATA%syncSlave_Sync, afterward, employing the standard synchronization capabilities of the genuine software SyncThing, the contents from these directories are transferred to the perpetrator’s device, facilitating the data exfiltration.” as stated in the report from the CERT-UA. The report also includes indicators of cyber threats.
Follow me on Twitter: @securityaffairs and Facebook and Mastodon
(SecurityAffairs – hacking, ThinkPHP)









