Chinese attacker exploits dated ThinkPHP vulnerabilities since October 2023

A Chinese-speaking group has been observed by Akamai exploiting two flaws, known as CVE-2018-20062 and CVE-2019-9082, in apps built on ThinkPHP.
Researchers at Akamai have witnessed a Chinese threat actor taking advantage of two outdated remote code execution vulnerabilities, known as CVE-2018-20062 and CVE-2019-9082, within the ThinkPHP framework.
The ongoing campaign started around October 2023, initially focusing on a small set of clients/companies but has since expanded to a larger scale.
The assaults were traced back to several IP addresses linked to servers hosted on the “Zenlayer” cloud provider (ASN 21859), primarily situated in Hong Kong.
“Hackers are exploiting well-known vulnerabilities, some of which date back several years, and are achieving success in doing so. A prime example of this is the exploitation of ThinkPHP’s remote code execution (RCE) vulnerabilities CVE-2018-20062 and CVE-2019-9082.” stated the analysis shared by Akamai.
In incidents identified on October 17, 2023, threat actors utilized vulnerabilities to direct victim servers to install a disguised shell from a remote server controlled by the attacker, instead of using conventional “proof of concept” commands. Although the initial campaign was short-lived, a similar albeit more extensive campaign has been noted as of April 2024.
The vulnerabilities CVE-2018-20062 and CVE-2019-9082 within the ThinkPHP software have implications on content management frameworks such as NoneCMS and open-source BMS. These vulnerabilities enable attackers to execute code on the server remotely. They are part of a series of exploit variations targeting different components of ThinkPHP, disclosed over multiple years starting from 2018.
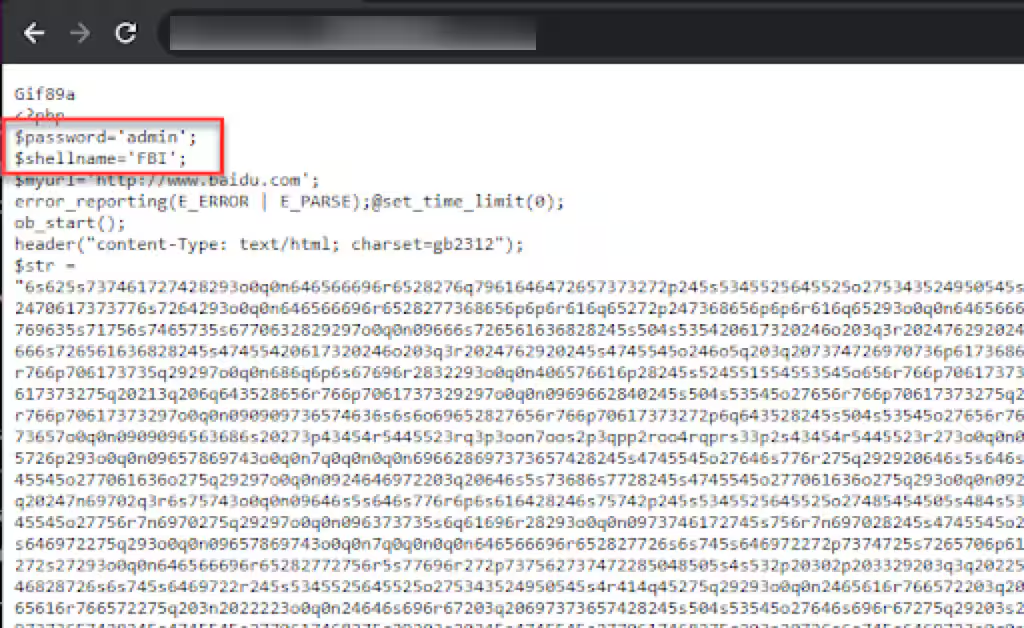
The Akamai-detected attacks leverage the vulnerabilities to fetch a file labeled “public.txt” from a compromised server in China. This downloaded file, dubbed “roeter.php,” is likely a typo for “router.” Inside this file lies a concealed web shell, acting as a backdoor script on the server for remote control. The web shell code is obscured through a basic ROT13 conversion, producing a lengthy HEX string. The assailants made use of a simple password, “admin,” to access the web shell.

“The web shell showcases advanced functionalities, such as browsing the file system, allowing operations like file modification, deletion, and alteration of timestamps for obfuscation purposes.” continues the analysis. “The webshell interface, often referred to as Dama, is in Traditional Chinese. In addition to the mentioned advanced mechanisms, Dama facilitates file uploads to the server and extracts crucial technical system data, including precise OS versions and PHP information, aiding in identifying relevant privilege escalation exploits.
The specialists noted that the Dama web shell is distinct due to the Chinese interface it offers.
Post-infiltration capabilities involve scanning network ports and accessing existing databases and server information. The web shell ensures privilege escalation by circumventing disabled critical PHP functions to execute shell commands on the server. It also leverages the Windows task scheduler to reconfigure WMI and add users with elevated privileges. Akamai researchers observed that despite its vast range of capabilities, the web shell does not support a command-line interface (CLI) for direct execution of OS shell commands.
“This web shell serves as another example of a one-day vulnerability — regardless of their age, attackers persist in targeting and exploiting them, with significant success. This highlights the constant challenge organizations face in identifying vulnerable assets and preserving effective patch management procedures.” concludes the report. “The recent assaults initiated by a Chinese-speaking adversary underline an emerging pattern of attackers employing a fully featured web shell designed for advanced manipulation of victims. Interestingly, not all targeted clients were utilizing ThinkPHP, indicating a potential indiscriminate targeting of diverse systems by the attackers.”
Follow me on Twitter: @securityaffairs and Facebook and Mastodon
(SecurityAffairs – hacking, ThinkPHP)










