8220 Gang used new ScrubCrypt crypter in recent cryptojacking attacks
A
threat
actor
tracked
as
8220
Gang
has
been
spotted
using
a
new
crypter
called
ScrubCrypt
in
cryptojacking
campaigns.
Fortinet
researchers
observed
the
mining
group
8220
Gang
using
a
new
crypter
called
ScrubCrypt
in
cryptojacking
attacks.
“Between
January
and
February
2023,
FortiGuard
Labs
observed
a
payload
targeting
an
exploitable
Oracle
Weblogic
Server
in
a
specific
URI.”
reads
the
analysis
published
by
Fortinet.
“This
payload
extracts
ScrubCrypt,
which
obfuscates
and
encrypts
applications
and
makes
them
able
to
dodge
security
programs.
It
already
has
an
updated
version,
and
the
seller’s
webpage
(Figure
1)
guarantees
that
it
can
bypass
Windows
Defender
and
provide
anti-debug
and
some
bypass
functions.”
The
group
is
known
for
exploiting
publicly
disclosed
vulnerabilities
to
compromise
targets.
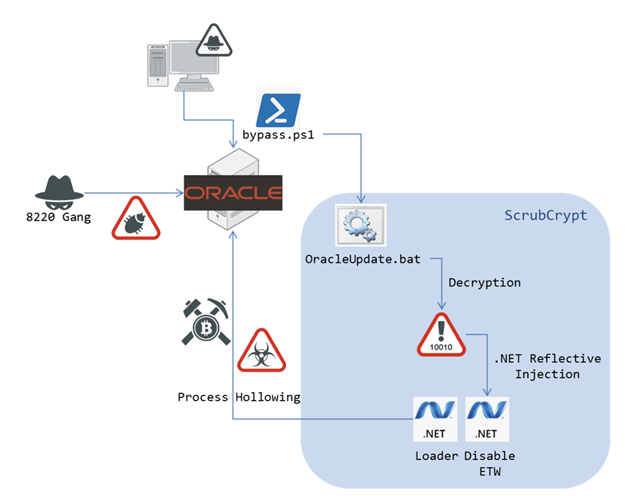
Between
January
and
February,
the
experts
observed
attacks
originating
from
163[.]123[.]142[.]210
and
185[.]17[.]0[.]19
that
targeted
an
HTTP
URI,
“wls-wsat/CoordinatorPortType.”
This
URI
belongs
to
an
Oracle
Weblogic
server.
Upon
successful
exploitation
of
vulnerable
Oracle
WebLogic
servers,
it
will
download
a
PowerShell
script,
named
“bypass.ps1,”
which
contains
the
ScrubCrypt
crypter.
The
PowerShell
script
is
encoded
to
avoid
detection
by
AntiVirus
solutions.
The
ScrubCrypt
crypter
is
available
for
sale
on
hacking
forums,
it
allows
securing
applications
with
a
unique
BAT
packing
method.
The
experts
noticed
that
encrypted
data
at
the
top
can
be
split
into
four
parts
using
backslash
“”.
The
final
two
parts
are
the
key
and
initial
value
for
AES
CBC
decryption.
The
attribution
of
the
attacks
to
the
8220
Gang
is
also
based
on
the
crypto
wallet
address
used
in
the
recent
campaigns
and
the
server
IP
address
used
in
the
Monero
miner.
“The
crypto
wallet
address, 46E9UkTFqALXNh2mSbA7WGDoa2i6h4WVgUgPVdT9ZdtweLRvAhWmbvuY1dhEmfjHbsavKXo3eGf5ZRb4qJzFXLVHGYH4moQ,
and
the
server
IP
address
used
in
Monero
miner
have
all
been
used
by
the
8220
Gang
in
the
past.”
concludes
the
report.
“It’s
why
we
believe
the
whole
attack
was
launched
by
this
threat
actor,
although
the
port
number
used
is
no
longer
8220.”
“8220
Gang
is
a
well-known
miner
group
that
usually
leverages
public
file-sharing
websites
and
targets
system
vulnerabilities
to
infiltrate
a
victim’s
environment.
Within
a
very
short
time,
it
has
evolved
to
use
a
newer
crypter
variant,
“ScrubCrypt.”

Follow
me
on
Twitter:
@securityaffairs
and
Facebook
and
Mastodon
(SecurityAffairs –
hacking,
ScrubCrypt)






%20v1.1.jpg#keepProtocol)

