
Microsoft
office
documents
are
used
worldwide
by
both
corporates
and
home-users
alike.
It’s
different
office
versions,
whether
licensed
or
unlicensed
offers
users
an
easy
way
to
create
and
modify
files.
However,
this
software
is
also
susceptible
to
cyberattacks.
Cybercriminals
often
take
advantage
of
its
vulnerability
and
use
VBA
(Visual
Basic
Application)
macros
as
entry
points
to
gain
access
to
targeted
systems
and
devices.
Over
the
years,
VBA
macros
has
been
a
domineering
threat
for
Office
documents
with
its
ability
to
spread
malware.
And,
this
is
why
Microsoft
has
finally
decided
to
block
VBA
macros
for
files
that
have
‘mark
of
the
web’
(MOTW)
tag.
With
this
change,
whenever
users
open
a
file
downloaded
from
internet,
such
as
email
attachments
which
have
macros,
the
following
message
will
be
displayed:
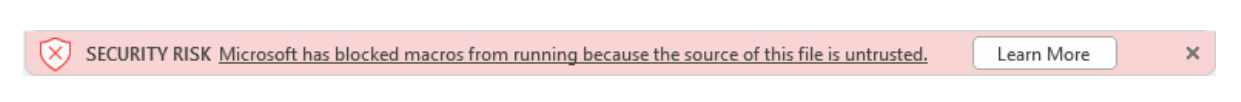
Fig-1. Security
Risk
Warning
As
a
result,
attackers
are
now
forced
to
think
of
alternative
ways
to
reach
their
victims.
And,
here’s
where
Microsoft
Add-ins
come
into
the
picture.
What
is
Microsoft
add-ins?
An
add-in
is
a
software
program
that
expands
the
capabilities
of
main
programs.
It
is
a
term
commonly
used
by
Microsoft
and
other
platforms
which
have
additional
functions
that
can
be
added
to
primary
programs.
Office
add-ins
are
DLL
files
which
have
different
extensions
depending
on
the
application.
Microsoft
Excel
and
Word
have
add-ins
with
the
file
extensions,
‘.xll’ and
‘.wll’ respectively.
For
Word,
the
‘.wll’ add-in
needs
to
be
placed
in
a
specific
location,
specified
by
the
registry
value
HKCUSoftwareMicrosoftOffice16.0WordSecurityTrusted
Locations,
depending
on
the
Office
version.
This
will
ensure
that
‘.wll’ add-in
gets
executed
by
word
application.
For
Excel
add-ins,
whenever
‘.xll’ file
gets
loaded,
it
will
be
opened
by
an
excel
application.
Malicious
XLL
files
Many
threat
actors
have
started
using
XLL
files
as
the
initial
vector.
These
files
are
mainly
shared
as
an
email
attachment.
It
is
associated
with
an
icon
similar
to
other
excel
supported
file
making
it
hard
for
end
users
to
distinguish
between
the
original
excel
file
and
an
add-in
file.
Fig-2. Malicious
DLL
with
.XLL
extension
Upon
opening
such
files,
excel
will
display
a
warning
about
the
malicious
code
in
it.
Fig-3. MS
office
warning
for
Add-in
It
is
possible
for
a
“.dll” (dynamic-link
library)
file
to
be
renamed
as
a
“.xll” (Excel
add-in)
file
and
used
for
malicious
purposes.
The
difference
between
a
regular
DLL
and
an
XLL
file
is
that
XLLs
can
have
certain
exported
functions
which
will
be
called
by
the
Excel
Add-In
manager
if
triggered
by
the
Excel
application.
When
XLL
file
is
launched
by
Excel,
it
will
invoke
the
export
functions
based
on
the
defined
XLL
interface
like
xlAutoOpen and
xlAutoClose
similar
to
the
methods
Auto_Open and
Auto_Close in
VBA
macros.
These
functions
can
be
used
to
load
malicious
code
and
download
malware
payload.
Technical
Analysis:
It
begins
with a file
named
“BankStatement-1674745402.xll”,
which
is
a
64
bit
DLL file.
This
file
contains one
export
function
in
it
with
a
name
“xlAutoOpen”
as
shown
in
fig
4.
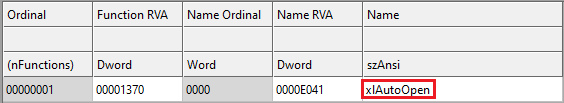
Fig-4. DLL
Export
Function
We
have
executed
this
DLL
file
explicitly
using
“rundll32.exe”
with
the
parameters,
“C:WindowsSysWOW64rundll32.exe
C:UsersuserDesktop9009859256BankStatement-1674745402.xll,
xlAutoOpen”.
In
fig
5,
we
can
see
process
execution
flow.
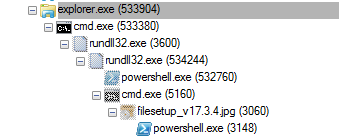
Fig-5. Process
Flow
of
Execution
The
export
function
has
a
code
(shown
in
fig
6)
that
uses
the
strcat
function
to
generate
different
strings
that
are
having
link
and
commands
for
execution.
The
below
function
creates
a
link “http[:]//160[.]119[.]253[.]36/filesetup_v17.3.4.zip” and
it
tries
to
connect
to
this
link
to
download
the
zip
file
and
saved
as
a
“mypictures.zip”.
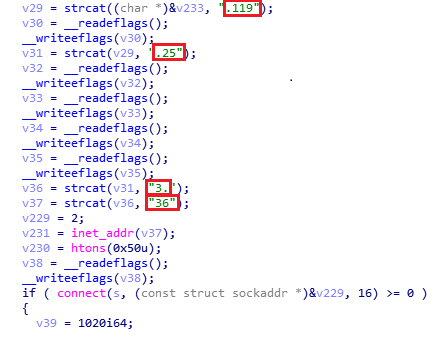
Fig-6. Code
for
generation
of
Link
and
connection
After
this,
PowerShell
is
used
to
unzip
this
zip
file
into
the
%Temp%
folder
with
the
below-mentioned
command,
“powershell.exe
Expand-Archive
–Path
“C:UsersuserAppDataLocalTempmypictures.zip”
-DestinationPath
“C:UsersuserAppDataLocalTemp””
After
unzipping
we
get
“filesetup_v17.3.4”
named
folder
in
the
%Temp%
folder
which
has
the
“Resources”
folder
and
“filesetup_v17.3.4.jpg”
file
inside.
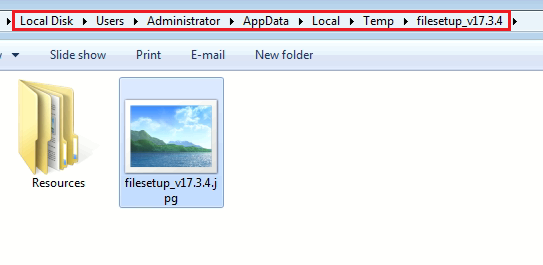
Fig-7. filesetup_v17.3.4 folder
into
Temp
Resources
folder
has
multiple
XML
files
containing
dummy
data.
Attackers
purposely
put
that
data
to
make
the
analysis
gruelling.
The
“filesetup_v17.3.4.jpg”
is
not
an
image
file
format
file.
It
is
nothing
but
a
32-bit
PE
File
written
in
.NET
language
and
it
looks
like
an
Inno
Setup
Module
installer.
An
Inno
Setup
is
a
free
and
popular
installer
framework
used
to
create
installers
for
Windows
applications.
It
provides
a
scripting
language
that
allows
developers
to
customize
the
installation
process,
including
the
creation
of
shortcuts,
registry
entries,
and
other
system
configuration.
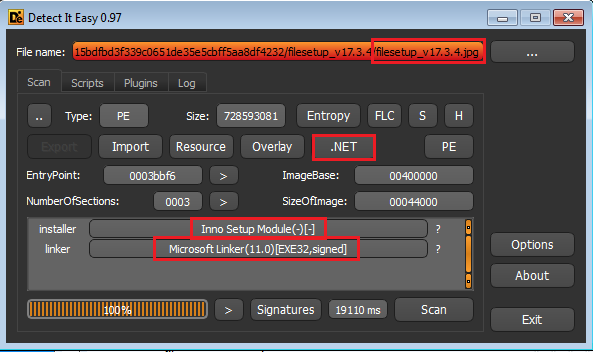
Fig-8. “filesetup_v17.3.4.jpg” file
info
in
Die
tool
This
.NET
file
has
213
methods
in
it
(shown
in
fig
9)
which
are
highly
obfuscated.
We
can
de-obfuscate
using de4dot obfuscators.
To
avoid
reversing
a
.NET
application,
the
author
has
implemented
multiple
methods
to
make
it
more
difficult
for
any
researcher
to
understand
the
code
and
logic
of
the
application.
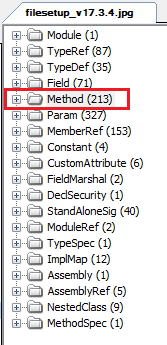
Fig-9. “.NET
Methods
Count”
This
“filesetup_v17.3.4.jpg”
file
executed
using
below
mentioned
command,
“cmd.exe
/c
start
C:UsersuserAppDataLocalTempfilesetup_v17.3.4filesetup_v17.3.4.jpg”
This
file
uses
a
few
anti-debugging
techniques
at
the
start
of
the
execution
which
are
mentioned
as
below,
1.
OllyDbg
is
a
popular
debugger
tool
that
can
be
used
to
analyze
and
modify
running
programs,
including
.NET
applications.
One
technique
for
detecting
and
preventing
debugging
using
OllyDbg
involves
checking
for
the
presence
of
a
specific
string
that
is
associated
with
the
debugger.
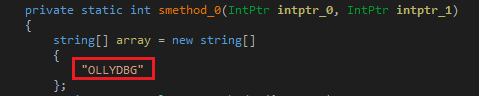
Fig-10. OLLDBG
Tool
Check
2.
Debugger
registry
check
which
is
used
to
determine
if
a
debugger
is
attached
to
the
process
and
take
appropriate
action
if
one
is
found.
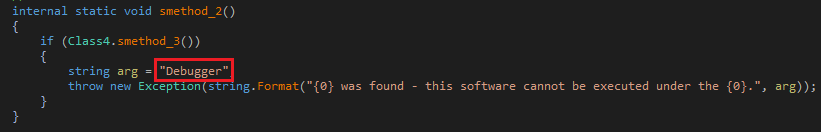
Fig-11. Debugger
registry
check
3.
IsDebuggerPresent
function
is
used
to
detect
if
a
debugger
is
attached
to
the
process
or
not.
4.
CheckRemoteDebuggerPresent
function
is
used
to
detect
if
a
debugger
is
attached
to
the
current
process
or
a
remote
process
or
not.
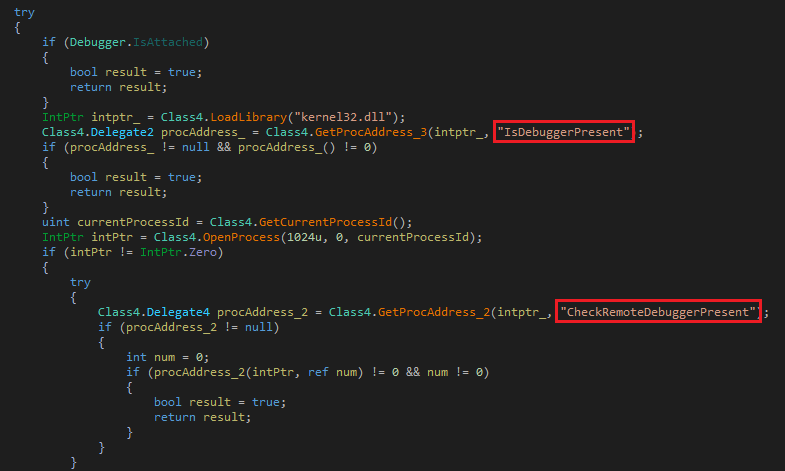
Fig-12.
IsDebuggerPresent
and
CheckRemoteDebuggerPresent
Functions
Racoon
Stealer
V2
is
a
type
of
malware
that
is
designed
to
steal
sensitive
information
from
infected
systems.
It
is
capable
of
stealing
various
types
of
files,
including
.ttf
and
.xml
files,
and
storing
them
on
the
infected
system.
However,
if
the
CNC
(command
and
control)
server
is
not
operational,
the
malware
may
be
unable
to
send
the
stolen
information
to
the
server
for
exfiltration.
In
this
scenario,
the
stolen
.ttf
and
.xml
files
may
remain
on
the
infected
system
until
the
CNC
server
becomes
available.
This
can
potentially
expose
sensitive
information
to
the
attacker,
as
they
may
still
be
able
to
access
the
stolen
files
on
the
compromised
system.
Quick
Heal
Protection:
Quick
heal
security
labs
has
been
actively
hunting
for
these
types
of
files
to
ensure
that
all
Quick
Heal
customers
are
protected
with
the
following
detections.
- Downldr.XllfmAgent.S29349494
- Downldr.XllDanot.S29357788
- Trojan.GenericRl.S24740760
- Trojan.RacoonStealerCiR
Conclusion:
In
conclusion,
Microsoft
Add-Ins
can
present
a
potential
threat
vector
for
malware
like
Raccoon
Stealer
V2.
These
types
of
malware
are
designed
to
steal
sensitive
information
from
infected
systems,
and
use
Microsoft
Add-Ins
as
a
means
of
delivering
the
malware
to
target
systems.
To
mitigate
this
risk,
organizations
should
implement
best
practices
for
endpoint
security,
such
as
keeping
software
up
to
date,
implementing
strong
antivirus
and
anti-malware
solutions,
enabling
firewalls
and
other
network
security
measures,
as
well
as
educating
users
on
the
steps
for
identifying
and
avoiding
social
engineering
attacks.
By
taking
these
measures,
organizations
can
significantly
reduce
the
risk
of
malware
attacks
and
data
theft
through
Microsoft
Add-Ins
and
other
potential
attack
vectors.
IOCs:
IP:
160.119.253.242
160.119.253.36
45.93.201.114
URL:
http[:]//160[.]119[.]253[.]36/filesetup_v17.3.4.zip
Malicious
DLL
File:
ab06eca36c9e011a149ea1625b8ad3629907b2a418ce10fe039870a3d9928bb0
9a652f77b9fba07d04e4021d3f533791bdedf4284fbbc007b4c55fea94a46635
6f74060f131c9034f55349cdeb2b5ebbd73582e6ac9da11c9310892bfdfeba36
5dfa56596b133d080b770e11783b1763da445dc2fef57fe060c87e7b73012308
2d9e90155343ba8f8f8e16c80b1dc62227f607c2ba277491c6f8f384bf5e0499
16522212c1b951ffab57e8f8fa288295cca5d9600e83b74551601246841cae91
0ec2bb5aad17efc7e1e1d8371b04684957684fec8e73df62bd41320bbf517b13
4da00e7d529be457c914b085d66f012c070bf6e3f85675303aa41a7689c08c75
Malicious
ZIP
File:
59d2403b99c95a057e43dd25e3d58b66331d130b52c19d2919e7966023ede5f6
Subject
Matter
Expert:
Anjali
Raut,
Akshay
Gaikwad











