YoroTrooper Stealing Credentials and Information from Government and Energy Organizations
A
previously
undocumented
threat
actor
dubbed
YoroTrooper
has
been
targeting
government,
energy,
and
international
organizations
across
Europe
as
part
of
a
cyber
espionage
campaign
that
has
been
active
since
at
least
June
2022.
“Information
stolen
from
successful
compromises
include
credentials
from
multiple
applications,
browser
histories
and
cookies,
system
information
and
screenshots,”
Cisco
Talos
researchers
Asheer
Malhotra
and
Vitor
Ventura
said
in
a
Tuesday
analysis.
Prominent
countries
targeted
include
Azerbaijan,
Tajikistan,
Kyrgyzstan,
Turkmenistan,
and
other
Commonwealth
of
Independent
States
(CIS)
nations.
The
threat
actor
is
believed
to
be
Russian-speaking
owing
to
the
victimology
patterns
and
the
presence
of
Cyrillic
snippets
in
some
of
the
implants.
That
said,
the
YoroTrooper
intrusion
set
has
been
found
to
exhibit
tactical
overlaps
with
the
PoetRAT
team
that
was
documented
in
2020
as
leveraging
coronavirus-themed
baits
to
strike
government
and
energy
sectors
in
Azerbaijan.
YoroTrooper’s
data
gathering
goals
are
realized
through
a
combination
of
commodity
and
open
source
stealer
malware
such
as
Ave
Maria
(aka
Warzone
RAT),
LodaRAT,
Meterpreter,
and
Stink,
with
the
infection
chains
using
malicious
shortcut
files
(LNKs)
and
decoy
documents
wrapped
in
ZIP
or
RAR
archives
that
are
propagated
via
spear-phishing.
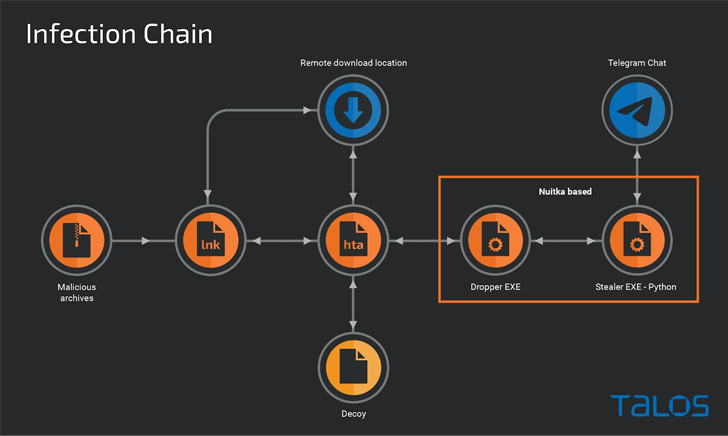
The
LNK
files
function
as
simple
downloaders
to
execute
an
HTA
file
retrieved
from
a
remote
server,
which
is
then
used
to
display
a
lure
PDF
document,
while
stealthily
launching
a
dropper
to
deliver
a
custom
stealer
that
uses
Telegram
as
an
exfiltration
channel.
WEBINAR
Discover
the
Hidden
Dangers
of
Third-Party
SaaS
Apps
Are
you
aware
of
the
risks
associated
with
third-party
app
access
to
your
company’s
SaaS
apps?
Join
our
webinar
to
learn
about
the
types
of
permissions
being
granted
and
how
to
minimize
risk.
The
use
of
LodaRAT
is
notable
as
it
indicates
that
the
malware
is
being
employed
by
multiple
operators
despite
its
attribution
to
another
group
called
Kasablanka,
which
has
also
been
observed
distributing
Ave
Maria
in
recent
campaigns
targeting
Russia.
Other
auxiliary
tools
deployed
by
YoroTrooper
consist
of
reverse
shells
and
a
C-based
custom
keylogger
that’s
capable
of
recording
keystrokes
and
saving
them
to
a
file
on
disk.
“It
is
worth
noting
that
while
this
campaign
began
with
the
distribution
of
commodity
malware
such
as
Ave
Maria
and
LodaRAT,
it
has
evolved
significantly
to
include
Python-based
malware,”
the
researchers
said.
“This
highlights
an
increase
in
the
efforts
the
threat
actor
is
putting
in,
likely
derived
from
successful
breaches
during
the
course
of
the
campaign.”