Who’s Behind the Botnet-Based Service BHProxies? – Krebs on Security
A
security
firm
has
discovered
that
a
six-year-old
crafty
botnet
known
as
Mylobot
appears
to
be
powering
a
residential
proxy
service
called
BHProxies,
which
offers
paying
customers
the
ability
to
route
their
web
traffic
anonymously
through
compromised
computers.
Here’s
a
closer
look
at
Mylobot,
and
a
deep
dive
into
who
may
be
responsible
for
operating
the
BHProxies
service.

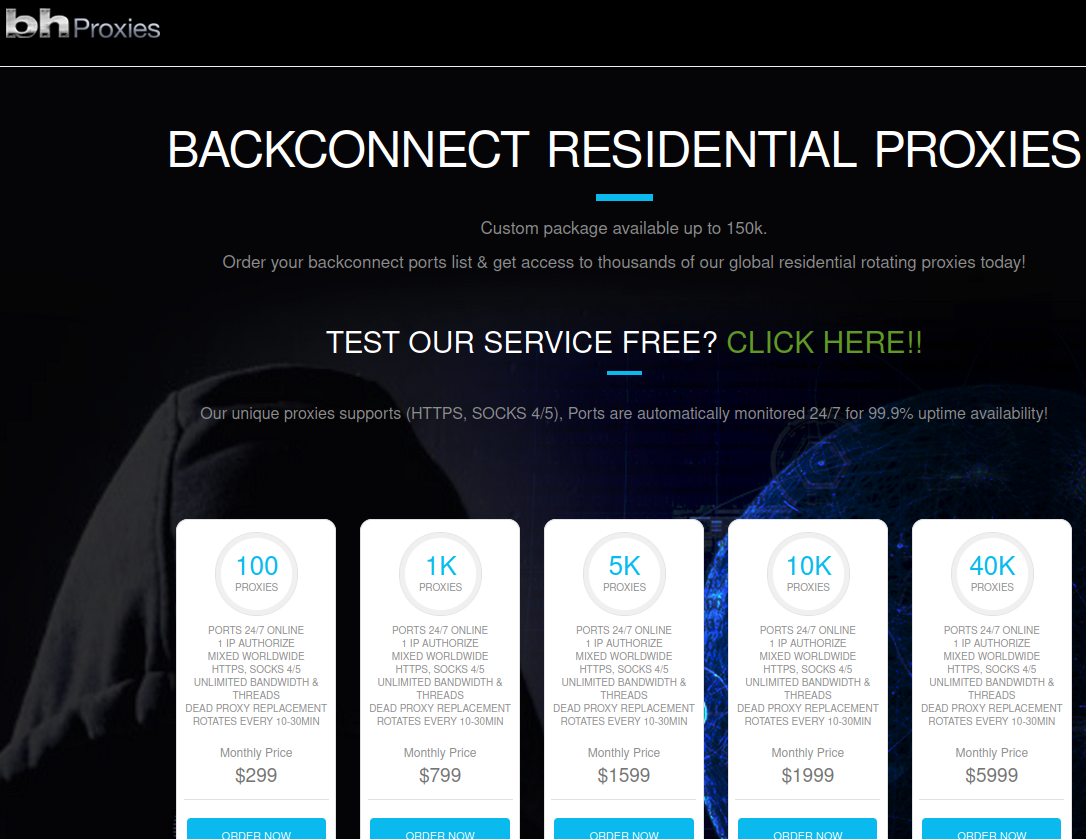
The
BHProxies
website.
First
identified
in
2017
by
the
security
firm
Deep
Instinct,
Mylobot
employs
a
number
of
fairly
sophisticated
methods
to
remain
undetected
on
infected
hosts,
such
as
running
exclusively
in
the
computer’s
temporary
memory,
and
waiting
14
days
before
attempting
to
contact
the
botnet’s
command
and
control
servers.
Last
year,
researchers
at
Minerva
Labs
spotted
the
botnet
being
used
to
blast
out
sextortion
scams.
But
according
to
a
new
report
from
BitSight,
the
Mylobot
botnet’s
main
functionality
has
always
been
about
transforming
the
infected
system
into
a
proxy.
The
Mylobot
malware
includes
more
than
1,000
hard-coded
and
encrypted
domain
names,
any
one
of
which
can
be
registered
and
used
as
control
networks
for
the
infected
hosts.
BitSight
researchers
found
significant
overlap
in
the
Internet
addresses
used
by
those
domains
and
a
domain
called
BHproxies[.]com.
BHProxies
sells
access
to
“residential
proxy”
networks,
which
allow
someone
to
rent
a
residential
IP
address
to
use
as
a
relay
for
their
Internet
communications,
providing
anonymity
and
the
advantage
of
being
perceived
as
a
residential
user
surfing
the
web.
The
service
is
currently
advertising
access
to
more
than
150,000
devices
globally.
“At
this
point,
we
cannot
prove
that
BHProxies
is
linked
to
Mylobot,
but
we
have
a
strong
suspicion,”
wrote
BitSight’s
Stanislas
Arnoud.
To
test
their
hypothesis,
BitSight
obtained
50
proxies
from
BHProxies.
The
researchers
were
able
to
use
48
of
those
50
proxies
to
browse
to
a
website
they
controlled
—
allowing
them
to
record
the
true
IP
addresses
of
each
proxy
device.
“Among
these
48
recovered
residential
proxies
IP
addresses,
28
(58.3%)
of
those
were
already
present
in
our
sinkhole
systems,
associated
with
the
Mylobot
malware
family,”
Arnoud
continued.
“This
number
is
probably
higher,
but
we
don’t
have
a
full
visibility
of
the
botnet.
This
gave
us
clear
evidence
that
Mylobot
infected
computers
are
used
by
the
BHProxies
service.”
BitSight
said
it
is
currently
seeing
more
than
50,000
unique
Mylobot
infected
systems
every
day,
and
that
India
appears
to
be
the
most
targeted
country,
followed
by
the
United
States,
Indonesia
and
Iran.
“We
believe
we
are
only
seeing
part
of
the
full
botnet,
which
may
lead
to
more
than
150,000
infected
computers
as
advertised
by
BHProxies’
operators,”
Arnoud
wrote.
WHO’S
BEHIND
BHPROXIES?
The
website
BHProxies[.]com
has
been
advertised
for
nearly
a
decade
on
the
forum
Black
Hat
World
by
the
user
BHProxies.
BHProxies
has
authored
129
posts
on
Black
Hat
World
since
2012,
and
their
last
post
on
the
forum
was
in
December
2022.
BHProxies
initially
was
fairly
active
on
Black
Hat
World
between
May
and
November
2012,
after
which
it
suddenly
ceased
all
activity.
The
account
didn’t
resume
posting
on
the
forum
until
April
2014.
According
to
cyber
intelligence
firm
Intel
471,
the
user
BHProxies
also
used
the
handle
“hassan_isabad_subar”
and
marketed
various
software
tools,
including
“Subar’s
free
email
creator”
and
“Subar’s
free
proxy
scraper.”
Intel
471’s
data
shows
that
hassan_isabad_subar
registered
on
the
forum
using
the
email
address
jesus.fn.christ@gmail.com. In
a
June
2012
private
message
exchange
with
a
website
developer
on
Black
Hat
World,
hassan_isabad_subar
confided
that
they
were
working
at
the
time
to
develop
two
websites,
including
the
now-defunct
customscrabblejewelry.com.
DomainTools.com
reports
that
customscrabblejewelry.com
was
registered
in
2012
to
a
Teresa
Shotliff
in
Chesterland,
Ohio.
A
search
on
jesus.fn.christ@gmail.com
at
Constella
Intelligence,
a
company
that
tracks
compromised
databases,
shows
this
email
address
is
tied
to
an
account
at
the
fundraising
platform
omaze.com,
for
a
Brian
Shotliff
from
Chesterland,
Ohio.
Reached
via
LinkedIn,
Mr.
Shotliff
said
he
sold
his
BHProxies
account
to
another
Black
Hat
World
forum
user
from
Egypt
back
in
2014.
Shotliff
shared
an
April
2014
password
reset
email
from
Black
Hat
World,
which
shows
he
forwarded
the
plaintext
password
to
the
email
address
legendboy2050@yahoo.com.
He
also
shared
a
PayPal
receipt
and
snippets
of
Facebook
Messenger
logs
showing
conversations
in
March
2014
with
legendboy2050@yahoo.com.
Constella
Intelligence
confirmed
that
legendboy2050@yahoo.com
was
indeed
another
email
address
tied
to
the
hassan_isabad_subar/BHProxies
identity
on
Black
Hat
World.
Constella
also
connects
legendboy2050
to
Facebook
and
Instagram
accounts
for
one
Abdala
Tawfik
from
Cairo.
This
user’s
Facebook
page
says
Tawfik
also
uses
the
name
Abdalla
Khafagy.
Tawfik’s
Instagram
account
says
he
is
a
former
operations
manager
at
the
social
media
network
TikTok,
as
well
as
a
former
director
at
Crypto.com.
Abdalla
Khafagy’s
LinkedIn
profile
says
he
was
“global
director
of
community”
at
Crypto.com
for
about
a
year
ending
in
January
2022.
Before
that,
the
resume
says
he
was
operations
manager
of
TikTok’s
Middle
East
and
North
Africa
region
for
approximately
seven
months
ending
in
April
2020.
Khafagy’s
LinkedIn
profile
says
he
is
currently
founder
of
LewkLabs,
a
Dubai-based
“blockchain-powered,
SocialFi
content
monetization
platform”
that
last
year
reported
funding
of
$3.26
million
from
private
investors.
The
only
experience
listed
for
Khafagy
prior
to
the
TikTok
job
is
labeled
“Marketing”
at
“Confidential,”
from
February
2014
to
October
2019.
Reached
via
LinkedIn,
Mr.
Khafagy
told
KrebsOnSecurity
that
he
had
a
Black
Hat
World
account
at
some
point,
but
that
he
didn’t
recall
ever
having
used
an
account
by
the
name
BHProxies
or
hassan_isabad_subar.
Khafagy
said
he
couldn’t
remember
the
name
of
the
account
he
had
on
the
forum.
“I
had
an
account
that
was
simply
hacked
from
me
shortly
after
and
I
never
bothered
about
it
because
it
wasn’t
mine
in
the
first
place,”
he
explained.
Khafagy
declined
to
elaborate
on
the
five-year
stint
in
his
resume
marked
“Confidential.”
When
asked
directly
whether
he
had
ever
been
associated
with
the
BHProxies
service,
Mr.
Khafagy
said
no.
That
Confidential
job
listing
is
interesting
because
its
start
date
lines
up
with
the
creation
of
BHproxies[.]com.
Archive.org
indexed
its
first
copy
of
BHProxies[.]com
on
Mar.
5,
2014,
but
historic
DNS
records
show
BHproxies[.]com
first
came
online
Feb.
25,
2014.
Shortly
after
that
conversation
with
Mr.
Khafagy,
Mr.
Shotliff
shared
a
Facebook/Meta
message
he
received
that
indicated
Mr.
Khafagy
wanted
him
to
support
the
claim
that
the
BHProxies
account
had
somehow
gone
missing.
“Hey
mate,
it’s
been
a
long
time.
Hope
you
are
doing
well.
Someone
from
Krebs
on
Security
reached
out
to
me
about
the
account
I
got
from
you
on
BHW,”
Khafagy’s
Meta
account
wrote.
“Didn’t
we
try
to
retrieve
this
account?
I
remember
mentioning
to
you
that
it
got
stolen
and
I
was
never
able
to
retrieve
it.”
Mr.
Shotliff
said
Khafagy’s
sudden
message
this
week
was
the
first
time
he’d
heard
that
claim.
“He
bought
the
account,”
Shotliff
said.
“He
might
have
lost
the
account
or
had
it
stolen,
but
it’s
not
something
I
remember.”
If
you
liked
this
story,
you
may
also
enjoy
these
other
investigations
into
botnet-based
proxy
services:
A
Deep
Dive
Into
the
Residential
Proxy
Service
‘911’
911
Proxy
Service
Implodes
After
Disclosing
Breach
Meet
the
Administrators
of
the
RSOCKS
Proxy
Botnet
The
Link
Between
AWM
Proxy
&
the
Glupteba
Botnet
15-Year-Old
Malware
Proxy
Network
VIP72
Goes
Dark
Who’s
Behind
the
TDSS
Botnet?