In
last
year’s
edition
of
the
Security
Navigator
we
noted
that
the
Manufacturing
Industry
appeared
to
be
totally
over-represented
in
our
dataset
of
Cyber
Extortion
victims.
Neither
the
number
of
businesses
nor
their
average
revenue
particularly
stood
out
to
explain
this.
Manufacturing
was
also
the
most
represented
Industry
in
our
CyberSOC
dataset
–
contributing
more
Incidents
than
any
other
sector.
We
found
this
trend
confirmed
in
2023
–
so
much
in
fact
that
we
decided
to
take
a
closer
look.
So
let’s
examine
some
possible
explanations.
And
debunk
them.
Hunting
for
possible
explanations
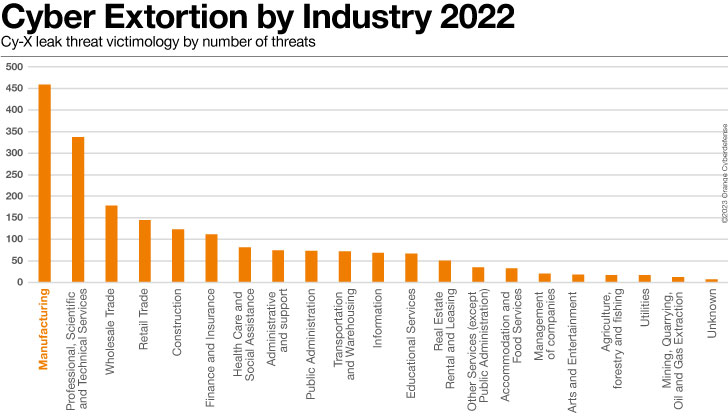
Manufacturing
is
still
the
most
impacted
industry
in
our
Cyber
Extortion
dataset
in
2023,
as
tracked
by
monitoring
double-extortion
leak
sites.
Indeed,
this
sector
now
represents
more
than
20%
of
all
victims
since
we
started
observing
the
leak
sites
in
the
beginning
of
2020.
Approximately
28%
of
all
our
clients
are
from
Manufacturing,
contributing
with
an
overall
share
of
31%
of
all
potential
incidents
we
investigated.
We
note
that
58%
of
the
Incidents
this
industry
deals
with
are
internally
caused,
32%
were
externally
caused,
1%
was
classified
as
“Partner”
or
3rd
parties.
When
external
threat
actors
had
caused
the
security
incident,
we
observed
the
top
3
threat
actions
were
Web
Attacks,
Port
Scanning
and
Phishing.
On
the
other
hand,
Manufacturing
has
the
lowest
apparent
number
of
confirmed
security
vulnerabilities
per
IT
Asset
in
our
Vulnerability
scanning
dataset.
Our
pentesting
teams
on
the
other
hand
report
4.81
CVSS
findings
per
day,
which
is
quite
a
bit
above
the
average
of
3.61
across
all
other
industries.
Several
questions
present
themselves,
which
we
will
attempt
to
examine
here:
-
What
part
does
Operation
Technology
play? -
Are
businesses
in
Manufacturing
more
vulnerable? -
Is
the
Manufacturing
sector
being
deliberately
targeted
more? -
Do
our
Manufacturing
clients
experience
more
incidents?
What
part
does
OT
play?
A
tempting
assumption
to
make
is
that
businesses
in
the
Manufacturing
sector
are
compromised
more
often
via
notoriously
insecure
Operational
Technology
(OT)
or
Internet
of
Things
(IoT)
systems.
Plants
and
factories
can
often
not
afford
to
be
disrupted
or
shut
down
and
that
Manufacturing
is
therefore
a
soft
target
for
extortionists.
It
sure
sounds
plausible.
The
catch
is:
we
don’t
see
these
theories
supported
in
our
data.
The
attack
against
US
Energy
giant
Colonial
Pipeline
was
probably
the
most
notable
recent
example
of
a
successful
attack
against
an
industrial
facility.
Discover
the
latest
in
cybersecurity
with
comprehensive
“Security
Navigator
2023”
report.
This
research-driven
report
is
based
on
100%
first-hand
information
from
17
global
SOCs
and
13
CyberSOCs
of
Orange
Cyberdefense,
the
CERT,
Epidemiology
Labs
and
World
Watch
and
provides
a
wealth
of
valuable
information
and
insights
into
the
current
and
future
threat
landscape.
In
July
this
year
US
intelligence
agencies
even
warned
of
a
hacking
toolset
dubbed
‘Pipedream’
that
is
designed
target
specific
Industrial
Control
Systems.
But
it
is
not
clear
to
us
if
or
when
these
tools
have
ever
been
encountered
in
the
wild.
Apart
from
the
infamous
Stuxnet
attack
from
2010,
one
struggles
to
recall
a
single
cyber
security
incident
where
the
entry
point
was
an
OT
system.
At
Colonial
Pipeline
the
backend
‘conventional’
administrative
systems
were
compromised
first.
Looking
more
closely,
this
is
the
case
for
almost
all
reported
incidents
at
industrial
facilities.
Are
businesses
in
the
Manufacturing
sector
more
vulnerable
to
attacks?
To
answer
this
questions
we
examined
a
set
of
3
million
vulnerability
scan
findings,
and
a
sample
of
1,400
Ethical
Hacking
reports.
We
derived
three
metrics
that
facilitate
somewhat
normalized
comparisons
across
the
industries
in
our
client
base:
VOC
scanning
findings
per
asset,
time
to
patch,
Pentest
findings
per
day
of
testing.
If
we
rank
industries
for
their
performance
on
each
of
those
metrics
and
sort
from
worst
to
best,
then
our
clients
in
the
Manufacturing
sector
arrives
in
5th
place
out
of
12
comparable
industries.
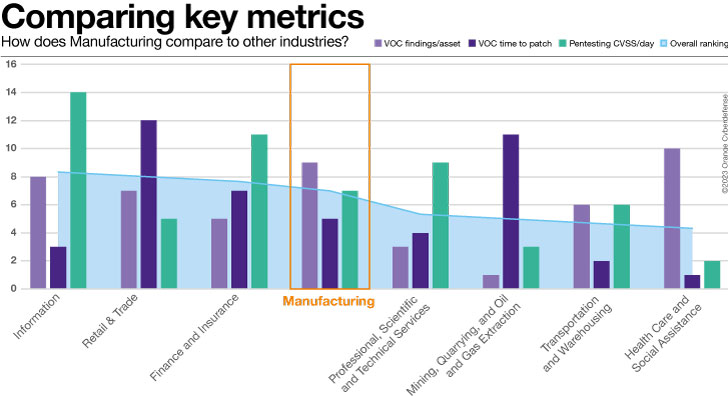
The
chart
below
shows
the
overall
*ranking*
of
our
Manufacturing
clients
out
of
comparable
industries.
VOC
unique
findings/asset
On
this
metric
there
were
seven
other
industries
that
performed
better
than
Manufacturing.
While
we
have
a
comparatively
high
number
of
assets
from
Manufacturing
clients
in
our
scanning
dataset,
we
report
far
fewer
Findings
per
Asset
than
the
average
across
all
industries.
Almost
10
times
fewer,
in
fact.
Time
to
patch
On
this
metric
6
other
industries
ranked
better
than
Manufacturing.
The
average
age
of
all
findings
for
this
industry
is
419
days,
which
is
a
concerning
number
and
worse
than
recorded
for
eight
other
industries
in
this
dataset.
Pentesting
findings
We
observe
that
the
average
CVSS
Per
Day
was
4.81,
compared
to
3.61
on
average
for
clients
in
all
other
sectors
in
the
dataset
–
33%
higher.
Is
the
Manufacturing
sector
being
targeted
more
by
extortionists?
We
use
the
North
American
Industry
Classification
System
–
NAICS
–
classification
system
when
categorizing
our
clients.
A
consideration
of
double-extortion
victim
counts
per
industry
reveals
a
very
interesting
pattern:
Of
the
10
industries
with
the
most
recorded
victims
in
the
dataset,
7
are
also
counted
amongst
the
biggest
industries
by
entity
count.
Manufacturing
however,
is
a
clear
trend-breaker.
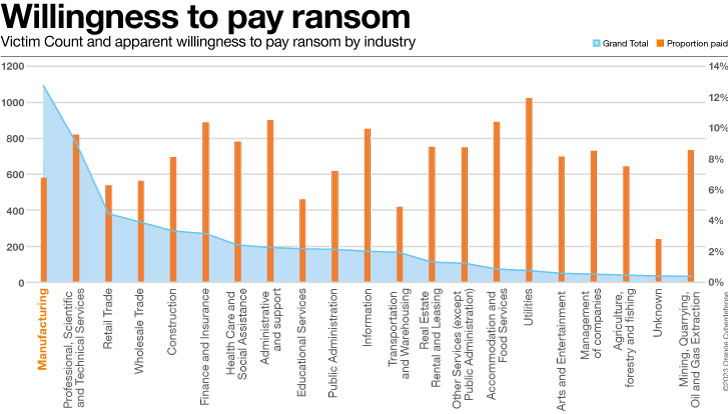
Another
factor
raises
questions:
if
businesses
in
the
Manufacturing
sector
were
more
willing
to
pay
ransom
that
would
make
them
more
attractive
as
victims.
But
then
we
would
expect
to
see
such
businesses
featuring
on
the
‘name
and
shame’
leak
site
less
often,
not
more.
Do
our
Manufacturing
clients
experience
more
incidents?
The
Manufacturing
industry
once
again
generated
the
highest
number
of
Incidents
as
a
percentage
of
the
total
in
our
CyberSOC
dataset.
31%
of
all
Incidents
are
generated
for
the
28%
of
our
clients
that
are
from
this
sector.
The
Incident
data
lacks
context,
however.
To
establish
a
baseline
for
comparison,
we
assign
customers
a
‘Coverage
Score’
between
0
and
5
in
8
different
‘domains’
of
Threat
Detection,
accounting
for
a
maximum
total
detection
score
of
40.
We
use
the
coverage
score
to
normalize
the
incident
count.
Put
simply,
the
lower
a
client’s
assessed
coverage
score
is,
the
more
this
adjustment
will
‘boost’
the
number
of
Incidents
in
this
comparison.
The
logic
is
that
a
low
amount
of
coverage
will
just
not
show
us
a
lot
of
incidents,
though
they
very
likely
occurr.
If
we
adjust
the
True
Positive
and
False
Positive
Incidents
as
described
above,
we
still
see
more
than
seven
times
as
many
Incidents
per
clients
from
Manufacturing
than
the
average
for
all
industries.
In
a
similar
comparison,
limited
only
to
Perimeter
Security,
and
only
Medium
Sized
business,
Manufacturing
ranks
1st
with
the
most
Incidents
per
Customer
out
of
7
comparable
Industries.
Conclusion
We
ruled
out
a
massive
impact
of
OT
security
vulnerabilities,
and
therefore
focus
on
regular
IT
systems.
Our
scanning
teams
assessed
a
large
number
of
targets
but
reported
relatively
few
vulnerabilities
per
asset.
Overall,
we
rank
the
Manufacturing
sector
as
5th
or
6th
weakest
of
all
industries
from
a
vulnerability
point
of
view.
The
question
of
why
we
consistently
record
such
a
high
proportion
of
victims
from
the
Manufacturing
industry
is
not
readily
answered
with
the
data
we
have.
We
believe
that
in
the
end
it
still
comes
down
to
the
level
of
vulnerability,
best
reflected
in
our
Penetration
Testing,
and
Findings
Age
data.
All
of
our
data
points
to
the
fact
that
attackers
are
mostly
opportunistic.
Rather
than
deliberately
singling
industries
out,
they
simply
compromise
businesses
that
are
vulnerable.
The
customers
represented
in
our
datasets
have
engaged
with
us
for
Vulnerability
Assessment
or
Managed
Detection,
and
therefore
represent
relatively
‘mature’
examples
of
that
industry.
We
can
deduce
that
average
businesses
in
this
sector
would
benchmark
worse
in
terms
of
vulnerabilities.
Whether
the
high
number
of
victims
we
observe
on
attacker
leak-sites
is
a
direct
reflection
of
the
high
number
of
overall
victims
in
this
sector,
or
the
skewed
reflection
of
an
industry
that
refuses
to
concede
to
initial
ransom
demands,
is
not
entirely
clear.
What
does
appear
likely,
however,
is
that
vulnerability
is
the
primary
factor
that
determines
which
businesses
get
compromised
and
extorted
–
in
this
sector
as
much
as
any
other.
This
is
just
an
excerpt
of
the
analysis.
More
details
on
how
different
Industries
performed
in
comparison
to
others,
as
well
as
more
CyberSOC,
Pentesting
and
VOC
data
(along
with
plenty
of
other
interesting
research
topics)
can
be
found
in
the
Security
Navigator.
It’s
free
of
charge,
so
have
a
look.
It’s
worth
it!
Note:
This
article
has
been
written
and
contributed
by
Charl
van
der
Walt,
Head
of
Security
Research
at
Orange
Cyberdefense.
this
article
interesting?
Follow
us
on
and
to
read
more
exclusive
content
we
post.